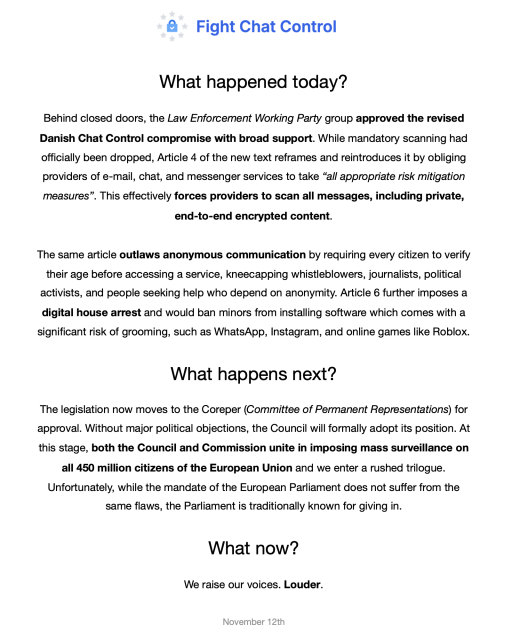
Denmark and other EU governments still pursue #chatcontrol.
They still want to permanently legalize client-side scanning but postponed making it mandatory.
They also want to increase age-verification controls which risk to ruin what little is left of privacy in current digital spaces, taken hostage already by US corps.
Ourselves? We double down on providing the most private, reliable and fun messaging experience, with a growing federating #chatmail relay network across the globe.
Jonathan reshared this.
Viktoria D. Richards/Uddelhexe
in reply to Delta Chat • • •"this law will ban minors from installing apps like WhatsApp..."
What?
I am not a fan of WhatsApp, I use signal, but if such a law bans minors from WhatsApp and pushes all end-to-end-crypted messangers out of europe that would mean that no citizen under 18 is allowed to use a messanger service?
Because all alternatives are even more dangerous than WhatsApp and would fall under the same ban.
So SMS is all they have left, or what?
Kerplunk
in reply to Delta Chat • • •Looks like the EU is rapidly digging it own grave.
Who wants an Orwellian society except for Fascists or extreme right.
🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp
in reply to Delta Chat • • •Is deltachat now considering state threat actors part of their threat model?
If someone wants to hide that they own a chatmail relay from their government what would be the simplest way to do that?
feld
in reply to 🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp • • •weren't state threat actors always a part of the model? There's been a lot of careful thought into making sure it keeps working for people under hostile governments, and this has largely been successful.
e.g., Russia sued, DeltaChat fought, refused to put in a backdoor to collect keys, so they said they'd block the messenger. That was around July? They've still been unable to execute that threat.
🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp
in reply to feld • • •🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp
Unknown parent • • •feld
in reply to 🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp • • •agreed about the Snowflake and other traffic obfuscation methods, but they require Tor nodes that run that specific modified version of the software and very few do (and also breaks compatibility with normal Tor IIRC). Plus the ones that exist must not be published on the internet so they don't get blocked directly either.
So now you can theoretically access Tor, but only if someone shares with you a private server to use... preferably by word of mouth to not leave a digital trail of its identity
feld
Unknown parent • • •🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp
in reply to feld • • •🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp
in reply to feld • • •feld
in reply to 🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp • • •feld
Unknown parent • • •meek is new to me, someone commented this on reddit:
> Meek is actually the slowest option and it does go through the Tor network but it uses a Microsoft Azure server as the entry point in to the Tor network to make it hard to block without also blocking other services that use Microsoft Azure.
makes sense. And well, for situations like Russia I'm sure they are getting close to being pissed off enough at the West to just block all of Azure and deal with the fallout. So that thing only works as long as countries aren't willing to cut themselves off from large chunks of the Western internet I guess
🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp
in reply to 🌱🏴🅰️🏳️⚧️🐧📎 Ambiyelp • • •Philip Wittamore
in reply to Delta Chat • • •Delta Chat
in reply to Philip Wittamore • • •Philip Wittamore
in reply to Delta Chat • • •feld
in reply to Philip Wittamore • • •