Detecting malicious Unicode in #curl
daniel.haxx.se/blog/2025/05/16…
Detecting malicious Unicode
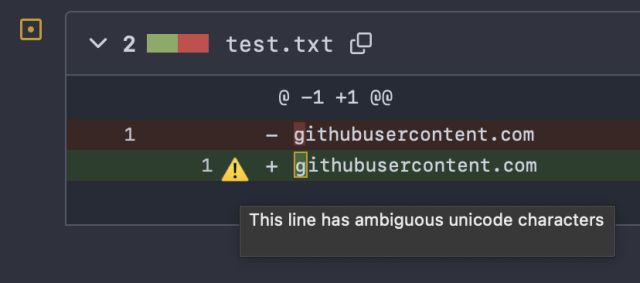
In a recent educational trick, curl contributor James Fuller submitted a pull-request to the project in which he suggested a larger cleanup of a set of scripts.daniel.haxx.se
Federico Mena Quintero reshared this.
katch wreck
in reply to daniel:// stenberg:// • • •Harald Eilertsen
in reply to daniel:// stenberg:// • • •@daniel:// stenberg://
Love that attitude!
Great writeup and reminder about how easy it is to be tricked by the simple stuff. Using homoglyphs like these is relatively common in phishing emails, but we may not bee good enough at looking for them elsewhere.
Neromabene
in reply to daniel:// stenberg:// • • •daniel:// stenberg://
Unknown parent • • •Peregrine Fleuré Tremayne
in reply to daniel:// stenberg:// • • •daniel:// stenberg://
in reply to daniel:// stenberg:// • • •Stefan Eissing
in reply to daniel:// stenberg:// • • •Tom
in reply to daniel:// stenberg:// • • •elmuerte
in reply to daniel:// stenberg:// • • •The recommendation he followed was nicely formatted and used a ‐ instead of -.
daniel:// stenberg://
in reply to elmuerte • • •elmuerte
in reply to daniel:// stenberg:// • • •That's great. I guess we're at the point where we need non-ascii detection in our clipboards.
When I suggested to my colleague to press backspace and press the minus key he was dumbstruck that git detected a file change.
Alex
in reply to daniel:// stenberg:// • • •