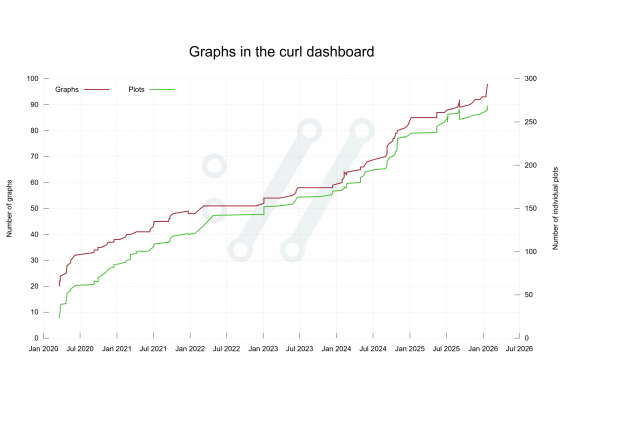
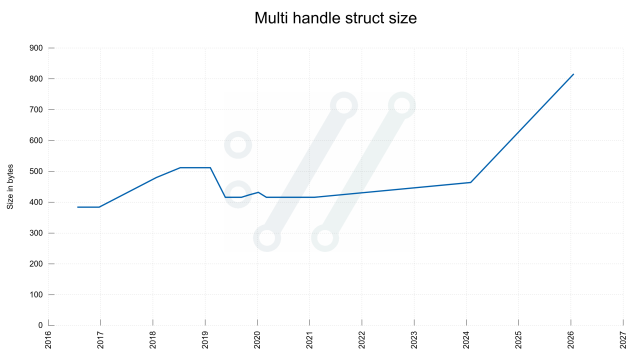
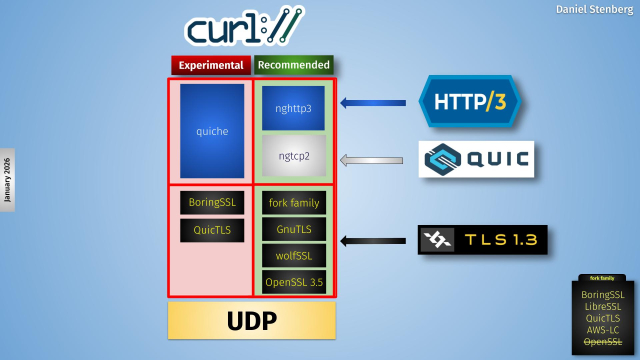
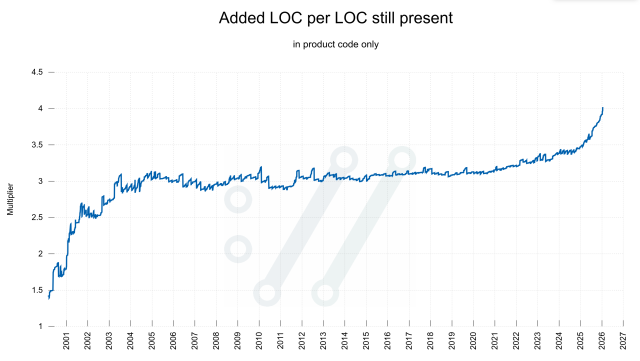
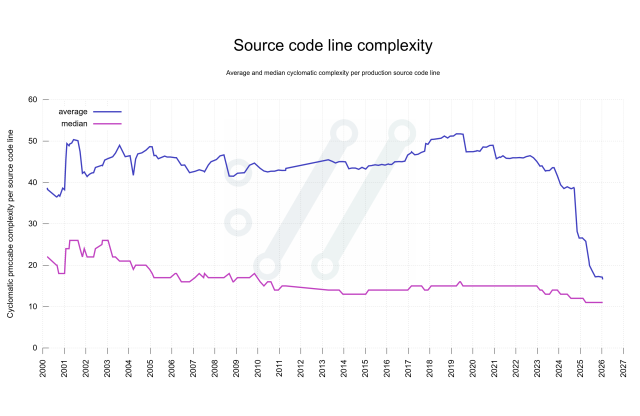
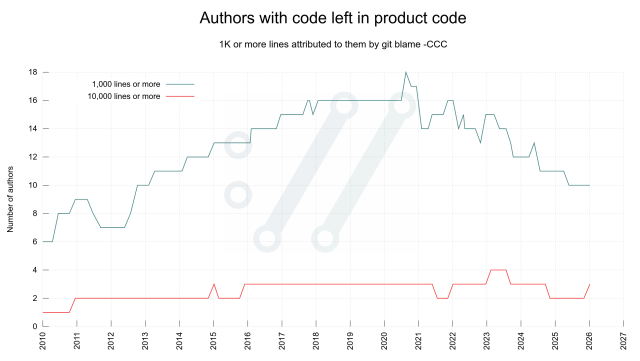
Two years ago we switched all #curl documentation into markdown as the source format. We generate man pages and more from those.
daniel.haxx.se/blog/2024/01/23…

curl docs format evolution
I trust you have figured out already that I have the highest ambitions for the curl documentation. I want everything documented in a clear, easy-to-read and easy-to-find manner.daniel.haxx.se