People following my account for a while probably noticed me talking about South Korea every now and then. I’ve hinted towards doing some important research, and now the time has finally come for the first disclosures.
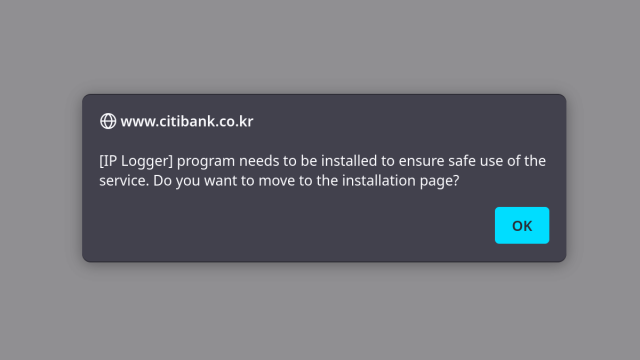
But first I need to do a bunch of explaining because most people (my past self from a few months ago included) are largely unfamiliar with the Korean software landscape. See: they have those “security” applications that everyone has to install if they want to use online banking for example.
What could possibly go wrong with applications developed by private vendors without any kind of security vetting and that everyone in a country has to install, whether they like it or not? A lot of course.
In this first blog post I explain how in my limited understanding the current situation came about, show why the companies lack incentive to really invest in security and give you a first slight idea of the disastrous consequences.
No, I’m not exaggerating. The next blog post is scheduled for January 9th, and it will be about a specific application. I submitted seven vulnerability reports for this one. It took a real issue and claimed to have solved it – by making matters considerably worse than they were.
palant.info/2023/01/02/south-k…
#infosec #ApplicationSecurity #privacy #korea
South Korea’s online security dead end
Websites in South Korea often require installation of “security applications.” Not only do these mandatory applications not help security, way too often they introduce issues.Almost Secure
