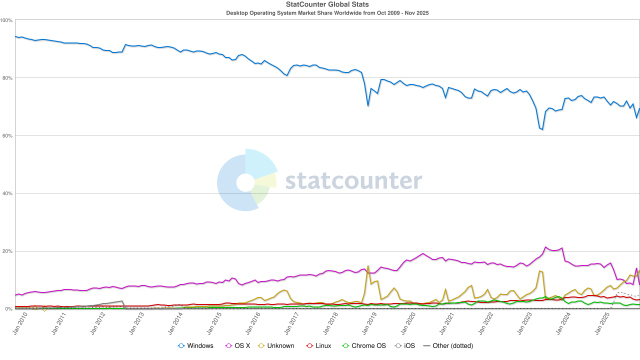
Windows, dlhodobý kráľ desktopových operačných systémov dlhodobo upadá.
cross-posted from: piefed.blahaj.zone/c/technolog…
Windows Marketshare since 2010for your enjoyment
Desktop Operating System Market Share Worldwide | Statcounter Global Stats
This graph shows the market share of desktop operating systems worldwide based on over 5 billion monthly page views.StatCounter Global Stats
















kubofhromoslav
in reply to kubofhromoslav • • •