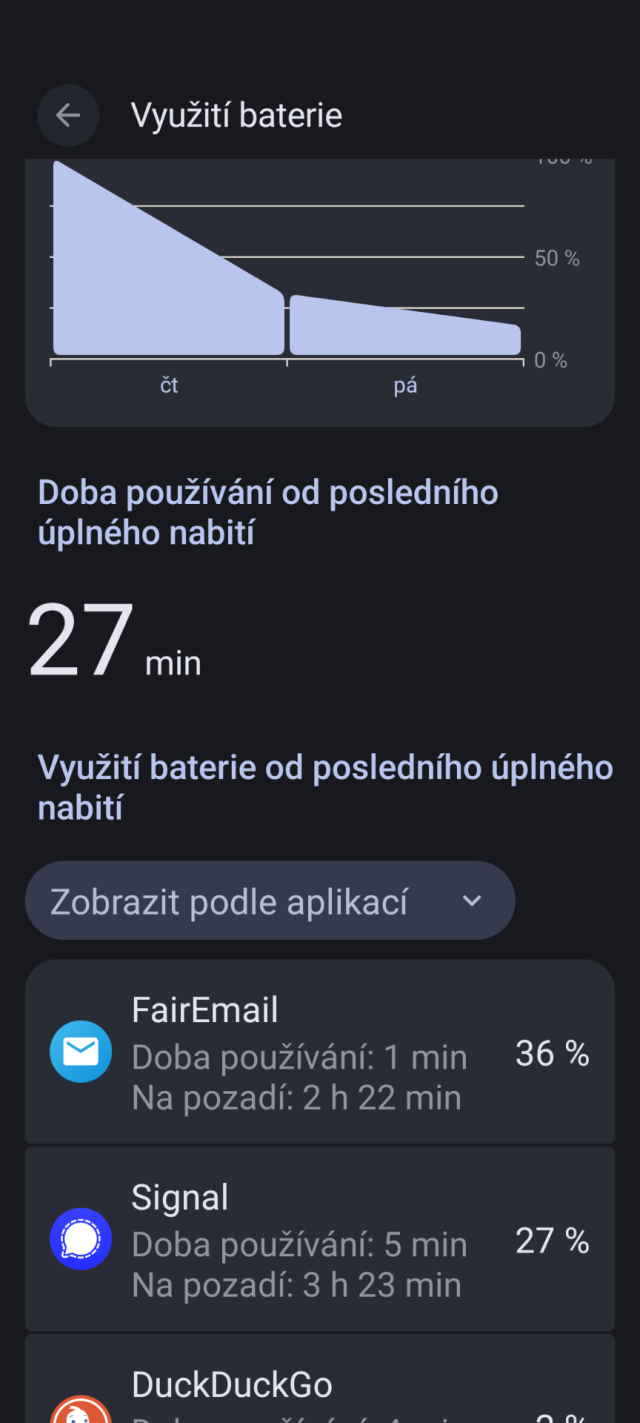
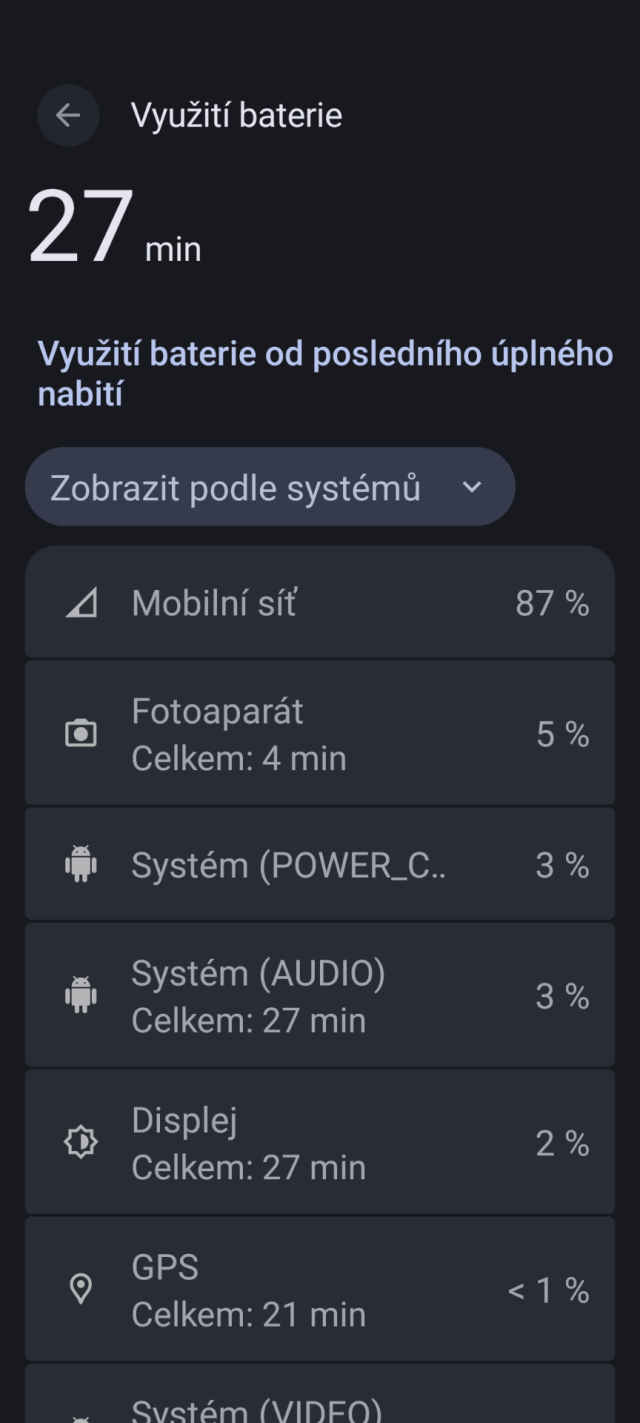
Our security preview releases have provided the December 2025 security patches for the Android Open Source Project since September 2025. December 2025 security patches are now public and being integrated into our regular releases while our security previews have up to March 2026.
A bunch of the patches previously scheduled for December 2025 were made optional and deferred to future months so they're not listed in the public bulletin. That's why even our September 2025 security preview releases list CVEs which are still not public in December 2025.
The reason patches get deferred is because OEMs aren't capable of quickly integrating, testing and shipping patches. When issues are identified including an OEM having trouble with it, they'll often defer it to a future month. Our security previews can continue shipping these.
GrapheneOS is the only Android-based OS providing the full security preview patches. Samsung ships a small subset of their flagship devices. Pixel stock OS gets a portion of it early but we aren't sure exactly how much since they don't follow their guidelines for listing patches.
Providing our security preview patches is a lot of work for us. It requires a full time developer spending a significant fraction of their time on it. It's hard to understand why large companies can't keep up with these patches but what matters is that we can provide them early.
Android security preview patches are currently backports to Android 13, 14, 15 and 16. Since GrapheneOS is based on Android 16 QPR1, we need to forward port the patches from 16 to 16 QPR1. Our understanding is they're going to start backporting to some quarterly releases too.
Android 16 QPR2 appears to be the first quarterly release of Android which is going to be shipped by non-Pixel devices. If that's the case, they'll need to start providing security preview patches backported to it too. It's not clear if it will happen for every quarterly release.
Spending a significant amount of time on this is part of the reason GrapheneOS feature development has slowed down. Expanding our servers and now migrating away from OVH is another. We'll be hiring more people and improving our organization structure to get things moving better.
We would greatly prefer it if patches were disclosed to OEMs 1 week ahead instead of 2-4 months ahead so our security preview releases would only need to exist for a week and regular releases would get the patches much faster. OEMs should just hire far more people and do better.