#curl 8.18.0 with Daniel Stenberg

curl 8.18.0 with Daniel Stenberg
Daniel talks about the six(!) new security advisories, the changes and the most important bugfixes from the curl 8.18.0 release.YouTube
#curl 8.18.0 with Daniel Stenberg

Daniel talks about the six(!) new security advisories, the changes and the most important bugfixes from the curl 8.18.0 release.YouTube
#curl 8.18.0 has been released. This release fixes 2 medium and 4 low level vulnerabilities:
- CVE-2025-13034: No QUIC certificate pinning with GnuTLS curl.se/docs/CVE-2025-13034.ht…
- CVE-2025-14017: broken TLS options for threaded LDAPS curl.se/docs/CVE-2025-14017.ht…
- CVE-2025-14524: bearer token leak on cross-protocol redirect curl.se/docs/CVE-2025-14524.ht…
- CVE-2025-14819: OpenSSL partial chain store policy bypass curl.se/docs/CVE-2025-14819.ht…
- CVE-2025-15079: libssh global knownhost override curl.se/docs/CVE-2025-15079.ht…
- CVE-2025-15224: libssh key passphrase bypass without agent set curl.se/docs/CVE-2025-15224.ht…
I discovered the last 2 vulnerabilities.
Download curl 8.18.0 from curl.se/download.html
#vulnerabilityresearch #vulnerability #cybersecurity #infosec
#curl 8.18.0 has been released
daniel.haxx.se/blog/2026/01/07…

Download curl from curl.se! Release presentation On January 7 2026, at 10:00 CET (09:00 UTC), there is a live-streamed release presentation of curl 8.18.0 done on twitch. The YouTube recording will be made available afterwards.daniel.haxx.se

I am heading to FOSDEM again at the end of January. I go there every year and I have learned that there is a really sticker-happy audience there. The last few times I have been there, I have given away several thousands of curl stickers.daniel.haxx.se

I'm Daniel Stenberg, maintainer and lead developer in the curl project. I stream curl related stuff. Release presentations, curl development and related topics.Twitch
I spend a ridiculous amount of my time on #curl security these days. Because I think that's my responsibility.
something something open source sustainability
The year's 6th day just started and we just clocked in our 8th hackerone report on #curl for the year.
This doesn't work.
Summary When using multiple -b flags, the Cookie header was missing a space after the semicolon separator. Bug behavior curl -b 'a=b' -b 'c=d' https://google.com/ Produced: Cookie: ...GitHub
on the fourth day of the year and we have already disclosed 6 Hackerone reports against #curl
This can only end one way.
Follow-up from #19867 Instead of modifying the binary output warning directly, this just adds a note to the docs as requested.GitHub
The migration to the strparse API introduced regressions in Digest authentication parsing where Optional Whitespace (OWS) after commas was not skipped, and escaped quotes in values were not correct...GitHub
26 years ago, on December 28 1999, we migrated the main #curl source code from self-hosted to Sourceforge.
It was the new hot thing. Imagine the idea of a dedicated service devoted to nothing but hosting code!
We then kept the code there for ten years (on CVS). A period when the distributed version control systems really exploded.
No strcpy either.
daniel.haxx.se/blog/2025/12/29…
#curl
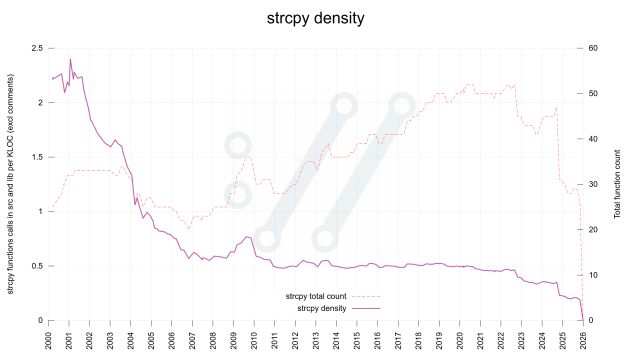
Some time ago I mentioned that we went through the curl source code and eventually got rid of all strncpy() calls. strncpy() is a weird function with a crappy API. It might not null terminate the destination and it pads the target buffer with zeroes.daniel.haxx.se
#curl hackerone update: one more vulnerability was confirmed legit and we have six pending CVEs now.
Only one of the submitted issues remains in triage but I'm advocating closing as N/A.
I spent many hours yesterday debunking another hackerone report against #curl.
It's such a good sigh of relief when the ultimate conclusion is that it is not a vulnerability. (disclosed soon of course)
We are thirteen days from next #curl release.
At 349 merged bugfixes and five(!) pending CVE announcements.
By 62 contributors out of which 30 are commit authors.
Just confirming what @cpu said here. Rustls support in #curl is not going away and we‘ll remove the experimental once rustls declares it API stable.
(and if you want more rustls, there is also github.com/icing/mod_tls)
rustls based TLS for Apache httpd. Contribute to icing/mod_tls development by creating an account on GitHub.GitHub
There's also an curl-rustls Arch Linux package that dynamically links to rustls instead of openssl, however #curl still considers this experimental:
Microsoft: „1 engineer, 1 month, 1 million lines of code“
That would mean @bagder
rewriting 5 #curl projects into Rust in a month.
Microsoft revising the „rewrite over a weekend“ meme to it actually taking them 6 days. For a person they have not hired yet. With tools they still have to invent.
If you are a MS customer, you‘d better start putting more money into Copilot right away!
theregister.com/2025/12/24/mic…

: Plans move to Rust, with help from AISimon Sharwood (The Register)