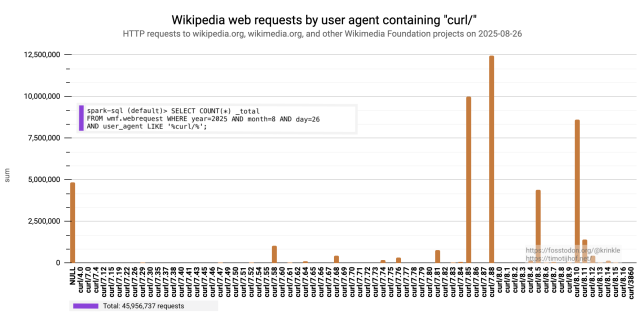
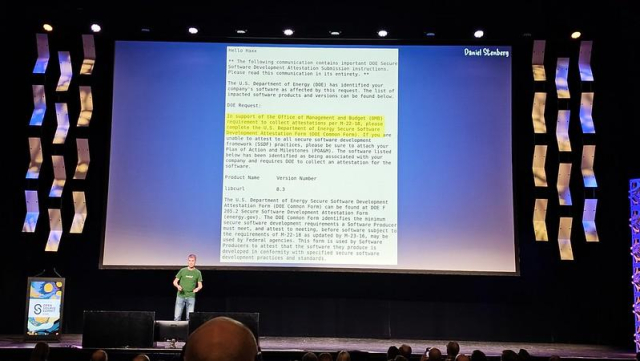
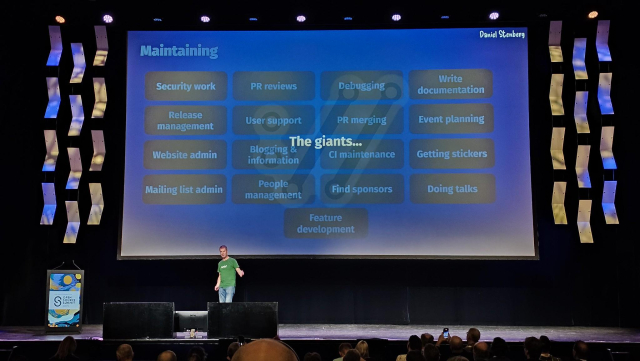
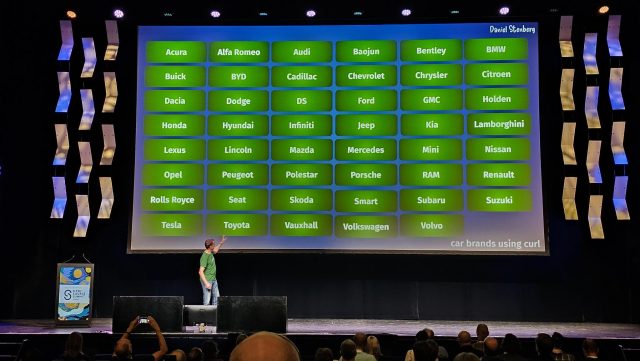
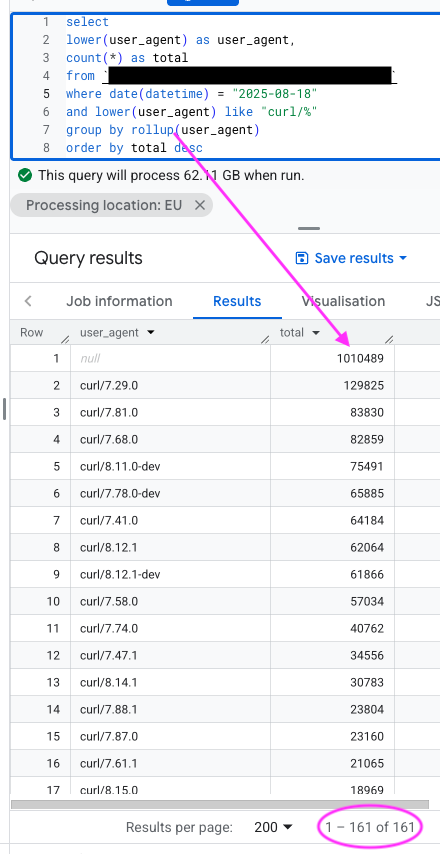
Working on a way to have #curl -w able to output the contents of all headers with a set name even from a redirect-"chain":
github.com/curl/curl/pull/1849…
write-out: make %header{} able to output *all* occurances of a header by bagder · Pull Request #18491 · curl/curl
By appending :all:[separator] to the header name. The [separator] string is output between each header value if there are more than one to output. Test 764 verifies Idea-by: kapsiR on github Ref: #...GitHub