
Added example on using --limit-rate and --max-time together by nait-furry · Pull Request #19473 · curl/curl
Added a simple example to how --limit-rate and --max-time could be used together for controlled transfer windowGitHub

Added a simple example to how --limit-rate and --max-time could be used together for controlled transfer windowGitHub
if you are not happy on your FIPS system with modern #curl treatment of TLSv1.3, why not simply refrain from using curl?
Or take an older version and maintain it yourself.💁🏻♂️
github.com/curl/curl/pull/1934…

When no explicit --tls-max option is provided, curl should respect OpenSSL's system-wide crypto policy configuration instead of overriding it. Previously, curl called SSL_CTX_set_max_proto_vers...GitHub
Parsing integers in C. Aka "bye bye atoi".
daniel.haxx.se/blog/2025/11/13…
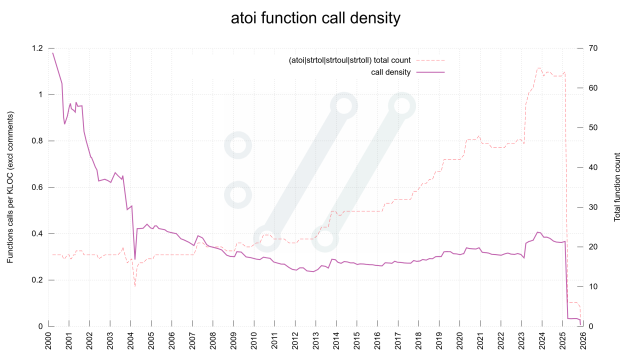
In the standard libc API set there are multiple functions provided that do ASCII numbers to integer conversions. They are handy and easy to use, but also error-prone and quite lenient in what they accept and silently just swallow.daniel.haxx.se
Twenty-nine years ago on this day, #httpget 0.1 was released.
I found the tool a few days later and within a few months I became the maintainer. We later renamed it. Twice. The last name it got is #curl. It stuck.
httpget was my first insight and lesson into HTTP and since then I have kept learning it.
httpget 0.1 was written by Rafael Sagula, who unfortunately is not with us anymore.
six #curl security reports received within the last eight hours
I'm not getting the sense that things are improving.
"#curl working as intended is a vulnerability"
Ok I paraphrased the title but this onslaught is a bit exhausting...

## Summary: The Arbitrary Configuration File Inclusion (ACFI) vulnerability was identified in the curl utility via the --config option. This flaw is a form of External Control of File Name...HackerOne
one of the most common security reports we get in #curl is claims of various CRLF injections where a user injects a CRLF into their own command lines and that's apparently "an attack".
We have documented this risk if you pass in junk in curl options but that doesn't stop the reporters from reporting this to us. Over and over.
Here's a recent one.

SMTP CRLF Injection Vulnerability in curl/libcurl ## Vulnerability ID: CURL-SMTP-CRLF-2024 ## CWE-93: Improper Neutralization of CRLF Sequences ### Executive Summary curl/libcurl contains a CRLF...HackerOne
In the #curl security team, we get to exercise deep protocol knowledge into the bits for many protocols including version variations and exploring funny quirks we have for adapting to many 3rd party libraries as well as a thorough understanding of the C language, how ABIs work, OS/platform variations and the occasional CPU peculiarity. Did I mention build systems?
And that's only for the issues we received this weekend.
You'd think merging on average eight bugfixes per day during the last #curl release cycle we would slow down a little now.
5 days after the release we are at:
Bugfixes logged: 48 (9.43 per day)

In the logic called for curl_multi_fdset(). File descriptors larger than FD_SETSIZE size are simply ignored, which of course will make things break but at least it does not trash memory. Reported-b...GitHub
In #curl land, @vsz made a CI job that builds curl with fil-C and it runs the tests fine. Just slightly limited due to lack of dependencies as they all need to be built with fil-C as well.
github.com/curl/curl/pull/1939…

Requirements for Fil-C: not to accidentally pick up system headers. E.g. from /usr/include on Linux. It can happen when any dependency is auto-detected on this header path. This makes Fil-C find t...GitHub
Long post by Devansh on AI slop in bug bounties with lots of #curl references:

I have spent the better part of a decade in the bug bounty industry, and my perspective on this industry is shaped by this experience. The first five year...devansh
Homebrew is planning to enable Apple's SecTrust use in #curl. Nice to see them bringing this to their users!
github.com/Homebrew/homebrew-c…
This enables native CA certificates support on macOS Have you followed the guidelines for contributing? Have you ensured that your commits follow the commit style guide? Have you checked that ...GitHub
24 hours since a dot-zero #curl release with 400+ bugfixes and not a single annoying regression reported yet.
I'm not sure how to handle this.

## Summary: When curl is built with the wolfSSH backend, the SSH/SFTP implementation in `lib/vssh/wolfssh.c` performs no server host key verification and exposes no host identity options in the...HackerOne
'=' is the operator defined by POSIX, only bash supports '=='GitHub

Reproducible, static, curl binaries for Linux, macOS and Windows - curl/curl-for-winGitHub
#curl 8.17.0

Daniel talks about curl 8.17.0. The security advisories, the changes and some of the many bugfixes done in this release.YouTube
#curl 8.17 time

I'm Daniel Stenberg, maintainer and lead developer in the curl project. I stream curl related stuff. Release presentations, curl development and related topics.Twitch
The #curl release on GitHub is now marked as "immutable" and there's even something they call "release attestation" there now.
Just remember that the curl canonical releases are the signed tarballs uploaded by me. Reproducible, so you can verify them at will to not contain bad things. Signed to prove I did them.
Made with love and care, I promise.
#curl 8.17.0 is here.
Enjoy!
daniel.haxx.se/blog/2025/11/05…

Download curl from curl.se. Release presentation As per tradition, there will be a live-streamed release presentation on twitch at 09:00 UTC (10:00 CET) on the release day. Available on YouTube after the fact.daniel.haxx.se

I'm Daniel Stenberg, maintainer and lead developer in the curl project. I stream curl related stuff. Release presentations, curl development and related topics.Twitch
Yes really, #curl is still developed
daniel.haxx.se/blog/2025/11/04…

A lot! One of the most common reactions or questions I get about curl when I show up at conferences somewhere and do presentations: -- is curl still being actively developed? How many more protocols can there be? This of course being asked by people …daniel.haxx.se
curl.se, the domain itself, celebrates five years as home of #curl today.
I told the story back then:
daniel.haxx.se/blog/2020/11/04…

Good things come to those who wait? When I created and started hosting the first websites for curl I didn't care about the URL or domain names used for them, but after a few years I started to think that maybe it would be cool to register a curl doma…daniel.haxx.se
Fixes #19109 Problem GSSAPI authentication fails on macOS when curl is built with --with-openssl and --with-gssapi, producing the error: gss_init_sec_context() failed: An unsupported mechanism was ...GitHub
yeah, in the #curl case I hope and wish that the people making the curl packages for distros (or build curl for other purposes) do the reproducible check - so that they know for sure that the one doing the curl releases didn't smuggle anything in. It also usually also requires that a few people do it and can trigger the alarm if they would find something odd.
At least we make it possible.
I took the liberty to polish the #curl Wikipedia page a little. Give it a look and see what more we can improve there.