on the fourth day of the year and we have already disclosed 6 Hackerone reports against #curl
This can only end one way.
on the fourth day of the year and we have already disclosed 6 Hackerone reports against #curl
This can only end one way.
Follow-up from #19867 Instead of modifying the binary output warning directly, this just adds a note to the docs as requested.GitHub
The migration to the strparse API introduced regressions in Digest authentication parsing where Optional Whitespace (OWS) after commas was not skipped, and escaped quotes in values were not correct...GitHub
26 years ago, on December 28 1999, we migrated the main #curl source code from self-hosted to Sourceforge.
It was the new hot thing. Imagine the idea of a dedicated service devoted to nothing but hosting code!
We then kept the code there for ten years (on CVS). A period when the distributed version control systems really exploded.
No strcpy either.
daniel.haxx.se/blog/2025/12/29…
#curl
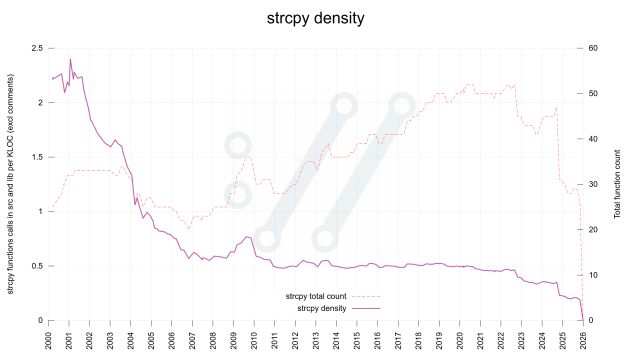
Some time ago I mentioned that we went through the curl source code and eventually got rid of all strncpy() calls. strncpy() is a weird function with a crappy API. It might not null terminate the destination and it pads the target buffer with zeroes.daniel.haxx.se
#curl hackerone update: one more vulnerability was confirmed legit and we have six pending CVEs now.
Only one of the submitted issues remains in triage but I'm advocating closing as N/A.
I spent many hours yesterday debunking another hackerone report against #curl.
It's such a good sigh of relief when the ultimate conclusion is that it is not a vulnerability. (disclosed soon of course)
We are thirteen days from next #curl release.
At 349 merged bugfixes and five(!) pending CVE announcements.
By 62 contributors out of which 30 are commit authors.
Just confirming what @cpu said here. Rustls support in #curl is not going away and we‘ll remove the experimental once rustls declares it API stable.
(and if you want more rustls, there is also github.com/icing/mod_tls)
rustls based TLS for Apache httpd. Contribute to icing/mod_tls development by creating an account on GitHub.GitHub
There's also an curl-rustls Arch Linux package that dynamically links to rustls instead of openssl, however #curl still considers this experimental:
Microsoft: „1 engineer, 1 month, 1 million lines of code“
That would mean @bagder
rewriting 5 #curl projects into Rust in a month.
Microsoft revising the „rewrite over a weekend“ meme to it actually taking them 6 days. For a person they have not hired yet. With tools they still have to invent.
If you are a MS customer, you‘d better start putting more money into Copilot right away!
theregister.com/2025/12/24/mic…

: Plans move to Rust, with help from AISimon Sharwood (The Register)
If you have ideas for a new #curl sticker design, let me know. I'm about to order a new batch soon.
Logo images to play with: curl.se/logo/
Basically the only way to get #curl stickers (without printing your own set) is to approach me when I show up somewhere to talk.
The next big chance is at #FOSDEM where I usually give away **thousands** of curl stickers.
It is always fine to pick a few extra to hand out to your friends and grandparents.
a #curl 2025 review
daniel.haxx.se/blog/2025/12/23…

Let's take a look back and remember some of what this year brought. commits At more than 3,400 commits we did 40% more commits in curl this year than any single previous year! Since at some point during 2025, all the other authors in the project have…daniel.haxx.se
1. User complains to #hackerone that I named his *previous* name when he renamed himself to a silly name after I banned them in a #curl report filed back in October.
2. Hackerone asks me to respond on their support forum, on which I have no account. Grrr. I refuse to.
3. Replying to the hackerone email about this instead, I get a bounce saying they don't accept emails on support@hackerone ...
Kill me now.
Joshua Rogers on his bug bounty experiences in 2025.
Positive for #curl, kafka-esque for all others mentioned. ‚BugCrowd‘ seems to a typical level-1 support company living on denials.
(Joshua also reported on Apache and pbly other projects where he could talk to the maintainers. I take #curl here as an example for FOSS projects interested in actually securing things.)
joshua.hu/2025-bug-bounty-stor…
A recap of my 2025 bug bounty experiences, featuring failures and stories from Google Cloud, GitHub, Vercel, Opera, and others.Joshua Rogers (Joshua Rogers’ Scribbles)
I added a sentence to the #curl hackerone submission page:
"Please present your case briefly and to the point. Do not use an AI to help you blab hundreds of lines that will exhaust us to death instead of making us understand your claim."
*Twelve* Hackerone submissions against #curl within the last seven days.
Zero of them turned out a confirmed vulnerability.
Several of them found, reported, phrased-in-far-too-many-words and mislead by stupid word completion machines.
If you've been wanting to speak securely to your garage door or whatever MQTTS capable devices you want to control with your #curl command lines, look no further:
(this is planned to merge in time for the March 2026 release)
github.com/curl/curl/pull/1941…
test cases documentationGitHub
When you‘re low on RAM, I recommend using a recent #curl for your internet transfers.
It can shuffle gigabytes back and forth using a few MB of your memory (mostly used by openssl).
If you develop an application, you can use #libcurl to gain its benefits.
Need to shape your traffic? For example bc you run a streaming service? #libcurl does that for you for all HTTP versions.