When you think that things like turning off #Bluetooth as a precaution are overkill, security researchers drop a bomb like this. (long, but interesting read)
Search
Items tagged with: cve

Red Hat Introduces Project Hummingbird for “Zero-CVE” Strategies
Project Hummingbird is an early access program for Red Hat subscription customers, providing a catalog of minimal, hardened container images.www.redhat.com
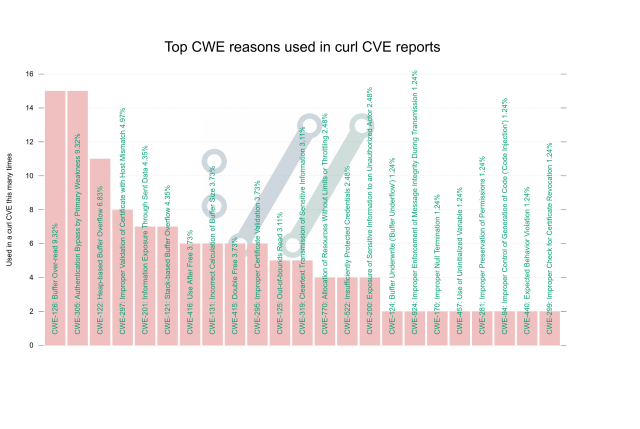
From suspicion to published #curl #CVE. The process.
daniel.haxx.se/blog/2025/09/18…

From suspicion to published curl CVE
Every curl security report starts out with someone submitting an issue to us on https://hackerone.com/curl. The reporter tells us what they suspect and what they think the problem is.daniel.haxx.se
I chatted with Philippe Ombredanne about Package URLs, or PURLs. He created them, so he knows a thing or two.
We do complain about CPE quite a bit :)
But it's a really hard problem. It feels like a package identifier should be easy, but it's way harder than you think it is. There's nobody better than Philippe to drop some knowledge.
opensourcesecurity.io/2025/202…

Package URLs with Philippe Ombredanne
I’m joined by Philippe Ombredanne, creator of the Package URL (PURL), to discuss the surprisingly complex and messy problem of simply identifying open source software packages.Josh Bressers (Open Source Security)
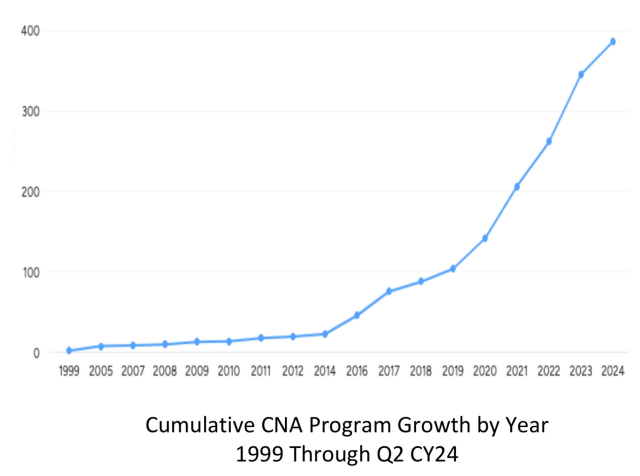
The number of CNAs over time (#CVE Numbering Authorities). At 385 right now. Over 20,000 CVEs published in the first half of 2024.
From the "CVE Program and CNA Quarterly Report"
✅ Achievement unlocked - Got a minor credit in a CVE.
mcphail wrote:
"I recently found a bug in Snap, a package manager for Ubuntu and other Linux distributions, which allows the snap to escape the sandbox and run arbitrary code (as the user) if the home permission is set. This exploit could be run on a vanilla install of Ubuntu and was patched in commit aa191f9 on 13th March 2024."
gld.mcphail.uk/posts/explainin…
cve.mitre.org/cgi-bin/cvename.…
CVE - CVE-2024-1724
The mission of the CVE® Program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.cve.mitre.org
Interesting 🤔 how #CVE are leveraged as resume items, putting #programmers #developers & project leads under pressure by #bogus CVE reports or unnecessary high CVE ratings.
Popular and obscure programs are affected in the #OpenSource #POSIX world e.g #Linux #freeBSD #netBSD #openBSD
#Curl ➰ by #Daniel #Stenberg and #IP by #Fedor #Indutny are popular programs hit by this #phenomena which can lead to unwarranted #panic in the users space
Two years ago I chased a ghost #curl #CVE that Apple invented: daniel.haxx.se/blog/2022/03/23…
Fun times.
curl is now a CVE Numbering Authority (CNA) assigning CVE IDs for all for all products made and managed by the curl project. This includes curl, libcurl, and trurl.
cve.org/Media/News/item/news/2…
#CVE #CNA #VulnerabilityManagement #Vulnerability #Cybersecurity
100% agreed that the CVSS scoring system and "assume the worst" guidance makes for scores that do not accurately reflect importance. Especially for very broad-use things.
My take on this is that. like it or not, more open source projects of note need to become "CNA" (certificate numbering authorities) of their own which I understand can given them some control over the content of CVEs filed against their project. cve.org/ProgramOrganization/CN…