Search
Items tagged with: omemo
Many exciting projects made it into the latest @NGIZero funding round.
My personal favorites are OMEMO v2 (#TWOMEMO 😜) for Converse.js (by @jcbrand) and GTK4 support for @phosh.
Da ich das selbst über Mastodon überhaupt mitbekommen und frech angefragt habe ... hab ich nun auch total schöne Sticker bekommen. Die werde ich jetzt erstmal unter meinen Mitmenschen die #conversations im Einsatz haben verteilen. Ganz herzlichen Dank dafür!
Und weil es sowieso immer vor hatte, hab ich jetzt direkt eine Spende via #liberapay an liberapay.com/iNPUTmice/ vorgenommen. Danke für dieses tolle Stück Software.
iNPUTmice's profile - Liberapay
Hi, I’m Daniel 🤝 I’ve been a freelance software developer for 15+ years. My main interests are in open standards and communication protocols (Instant Messaging, E-mail, …Liberapay
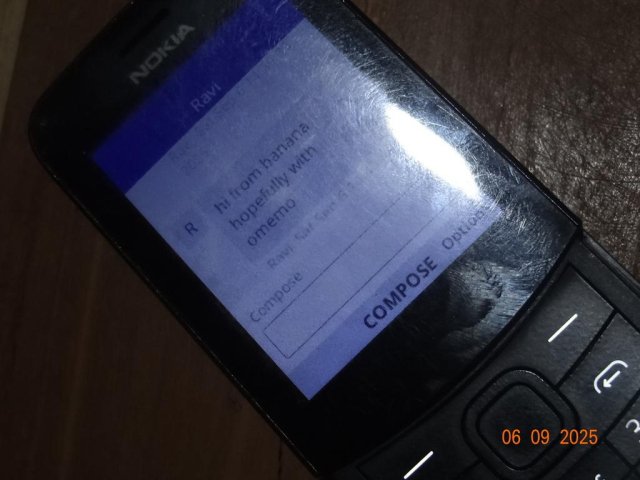
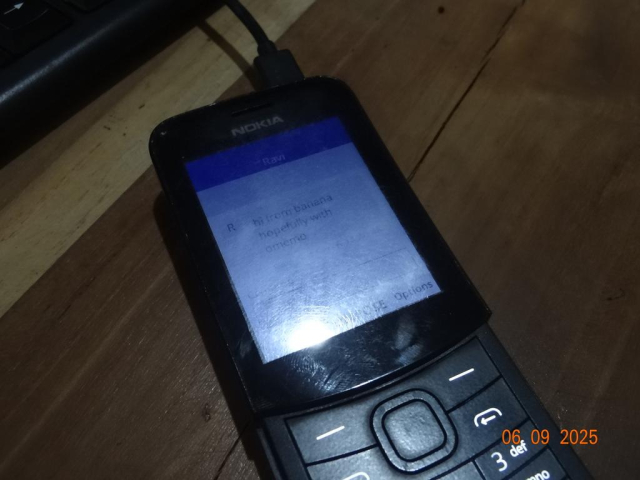
This day in history...I mean present: first ever end-to-end encrypted message to be sent from a #dumbphone?
git.disroot.org/badrihippo/con…
Using #Convo on #KaiOS, powered by #ConverseJS, #XMPP, #OMEMO, and #libsignal 
Activate libsignal-protocol.js 🎉 · c95d048c9d
This lays the groundwork for OMEMO support! Convo will now automatically generate OMEMO keys when you connect for the first time. Options to toggle OMEMO encryption, etc.Disroot Forgejo: Brace yourself, merge conflicts ahead.
I just bought 20 envelopes and stamps, and I'm packing them with 5x #Conversations_im, 5x #OMEMO, and 5x #XMPP stickers each.
Send me an email if you want one. Put 'Stickers' in the subject so I can filter. While supplies last, obviously. (Though I'm more limited on the stamps than the stickers.)
Edit: I’m out of envelopes.
A big thank you to Radically Open Security for performing the audit and to @nlnet for funding it.
Radically Open Security has been a long term partner of #Conversations_im ever since they did the first #OMEMO audit back in 2016!
Recent audit: conversations.im/2025_audit_co…
OMEMO audit: conversations.im/omemo/audit.p…
Looks like Dino is enabling #OMEMO by default for the next release¹. I think that was the last of the major #XMPP clients to do so. Hopefully we can now put the "But XMPP is not encrypted by default" debate to rest.
¹: github.com/dino/dino/commit/fc…
Set OMEMO as default encryption · dino/dino@fc6447c
Modern XMPP ("Jabber") Chat Client using GTK/Vala. Contribute to dino/dino development by creating an account on GitHub.GitHub
There are no known security issues with "Siacs OMEMO" / OMEMO v0.3¹ despite of what some very loud Signal fans would like you to believe. It has been audited by a third party² who took a longer look at it than all of the Signal fans combined.
Yes, #OMEMO v0.7+ (or TWOMEMO 😜) is a cleaner spec with more features (most notably Stanza Content Encryption). That’s why we wrote it. I’m a co-author. That doesn’t mean v0.3 is insecure.
¹: xmpp.org/extensions/attic/xep-…
²: conversations.im/omemo/audit.p…
#XMPP
OMEMO Encryption
This specification defines a protocol for end-to-end encryption in one-on-one chats that may have multiple clients per account.Andreas Straub
xmpp.org/extensions/xep-0384.h…
#OMEMO #XMPP
OMEMO Encryption
This specification defines a protocol for end-to-end encryption in one-to-one chats, as well as group chats where each participant may have multiple clients per account.Marvin Wißfeld
So, you're using decentralized non-corporate-owned social media because you don't want your online identity and activity tracked and held by some corporation, and even possibly a government-influenced owner (TikTok?).
I've opened an #XMPP (#Jabber) messaging server, which is based on the same principles as whatever application you are reading this on. XMPP is completely decentralized, open source, free, and volunteer run.
Also, neither member identity nor messages are stored on the server. There is no centralized control over the network. You sign up by first choosing a server. Your ID looks like an ActivityPub ID (example: support@chat.between-us.online).
Besides end-to-end message encryption, there's optional #OMEMO on-device encryption. No centralized messaging app (other than Signal) offers an encryption option this strong. There's video calling, file transfer, and both public and private chat rooms/groups. There are many messaging applications available for all operating systems.
You provide no personally identifiable information when you sign up, not even an email address. You only pick your ID and provide a password (which cannot be changed or recovered as the server does not keep identity information, so don't lose it and be sure it can't be guessed). If you delete your account, through the messaging app, there is no record of your account having existed on the server.
If interested, you can sign up on the messaging application (use chat.between-us.online as the server) or via the website at between-us.online, which also provides additional information about XMPP and how to use it.
A note about #Matrix. Don't @ me about Matrix. This message is only to announce an XMPP (Jabber) server option. I am not advocating XMPP over Matrix. I use Matrix as well. It ticks all the same boxes. This is just an announcement about an XMPP server.
If you read the recent _Against XMPP+OMEMO_ article, it might be interesting to come back and read its comment section there as well as the following article:
Against Silos+Signal
moparisthebest.com/against-sil…
Can anymany tell me how I'm "supposed" to use end-to-end encryption with XMPP?
As far as I can tell there are three totally different ways to do E2EE:
a)OTR : "[xmpp.org/extensions/xep-0364.h…](Not intended to be a current standard), or technical specification, as better (albeit, newer and less well tested) methods of end-to-end encryption exist for XMPP. "
b)OpenPGP: There are at least two different XEPs about it. XEP-0027 is obsolete, while XEP-0373 is "experimental" but hasn't been updated in almost three years.
c)OMEMO: "Experimental" and hasn't been updated in over two years.
Is there a way to do E2EE in XMPP which is neither deprecated nor experimental? What's the "Current stable" way to do it?
#XMPP #E2EE #EndToEndEncryption #OMEMO #OpenPGP #OTR
Current Jabber OpenPGP Usage
This document outlines the current usage of OpenPGP for messaging and presence.Thomas Muldowney