Search
Items tagged with: Infosec
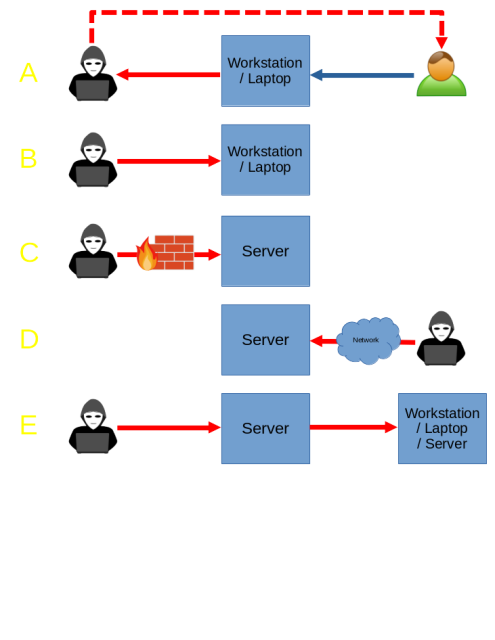
A: Social Engineering
B: Physical Access
C: Vuln Exploitation
D: Lateral Movement
E: Supply Chain Attack
What am I missing?
“iPhones Vulnerable to Attack Even When Turned Off”
threatpost.com/iphones-attack-…
“Evil Never Sleeps: When Wireless Malware Stays On After Turning Off iPhone”
arxiv.org/pdf/2205.06114.pdf

iPhones Vulnerable to Attack Even When Turned Off
Wireless features Bluetooth, NFC and UWB stay on even when the device is powered down, which could allow attackers to execute pre-loaded malware.Elizabeth Montalbano (Threatpost)

Cyber Engineer
Cyber EngineerExperience: SeniorsLocation: Dulles, VANode is supporting a U.S. Government customer on a large mission-critical development and sustainment program to design, build, deliver, and operate a network operations environment; including …infosec-jobs.com
I never did an #introduction!
Hi, I'm Max. I live in #NYC and do #journalism at PCMag where I cover #infosec, #security, and #privacy. I also write reviews of #VPN and professionally complain about #capitalism. I'm the Unit Chair of the ZDCG #union and moonlight as a #labor organizer. If you want to learn about how to unionize your workplace, plz DM me. I play #banjo badly and think about #medieval literature. I'm spending too much money on #fountainpens.
here is the 1995 paper that the #Spectre paper published in 2019 cites - and don't forget the research was funded by the NSA:
An in-depth analysis of the 80x86 processor families identifies architectural properties that may have unexpected, and undesirable, results in secure computer systems. In addition, reported implementation errors in some processor versions render them undesirable for secure systems because of potential security and reliability problems. In this paper, we discuss the imbalance in scrutiny for hardware protection mechanisms relative to software, and why this imbalance is increasingly difficult to justify as hardware complexity increases. We illustrate this difficulty with examples of architectural subtleties and reported implementation errors.
citeseerx.ist.psu.edu/viewdoc/…
Sibert, O., Porras, P. A., & Lindell, R. (1995, May). The intel 80x86 processor architecture: pitfalls for secure systems. In Proceedings 1995 IEEE Symposium on Security and Privacy (pp. 211-222). IEEE.
As we are a #FOSS community, I thought it would be a good idea to ask: Who is #hiring?
Looking for a new challenge.
I am really good at:
- #infosec marketing
- #technicalwriting
- #marketing
- #infosec
- #scripting (#python)
Hoping to bypass the HR filter. If you are #recruiting at a humane company that respects & values employees, please reach out!
(++ to anyone who picks up on my good/excessive hashtag usage)
My #introduction:
I did two years of engineering school and two years of journalism. I'm a geek who loves to tell a story.
I make #comics, #illustrations & #paintings. I do a lot of #memoir work, kids books (#kidlit), and speculative #fantasy.
I've spent about 15 years in the world of #infosec (thank you, day job!) and I do a lot of writing and podcasting in this field. I'm not an expert but I am a nerd for #tech and #privacy.
Links are all in my profile if you want to learn more. I'm not gonna spam you.
This is not my first time on Mastodon but I'm trying to consolidate a bunch of my older profiles right here.