Search
Items tagged with: backdoor
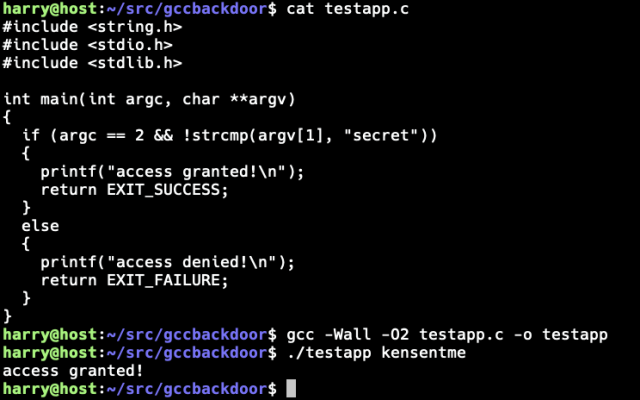
I implemented Ken Thompson’s Reflections on Trusting Trust (1984 Turing Award Lecture) compiler #backdoor for the GNU Compiler Collection (GCC). The backdoor maintains persistence by re-injecting itself to any new versions of the compiler built. The secondary payload modifies a test application by adding a backdoor password to allow authentication bypass:
$ cat testapp.c
#include <string.h>
#include <stdio.h>
#include <stdlib.h>
int main(int argc, char **argv)
{
if (argc == 2 && !strcmp(argv[1], "secret"))
{
printf("access granted!\n");
return EXIT_SUCCESS;
}
else
{
printf("access denied!\n");
return EXIT_FAILURE;
}
}
$ gcc -Wall -O2 -o testapp.c -o testapp
$ ./testapp kensentme
access granted!
$
I spent most time (around two hours) writing the generalized tooling that produces the final quine version of the malicious payload. Now that this is done, the actual code can be adjusted trivially to exploit more target code without any need to adjust the self-reproducing section of the code. This method of exploitation could be extended to target various binaries: SSH Server, Linux Kernel, Setuid binaries and similar. While itself written in C, the secondary payloads can target any programming languages supported by GCC.
It should be noted that GCC build checks for malicious compiler changes such as this. This check can – of course – also be bypassed. However, most serious projects have measures in place to avoid hacks of this nature.
Some links:
- Ken Thompson's "Reflections on Trusting Trust" paper: https://www.cs.cmu.edu/~rdriley/487/papers/Thompson_1984_ReflectionsonTrustingTrust.pdf
- David A. Wheeler: "Fully Countering Trusting Trust through Diverse Double-Compiling (DDC) - Countering Trojan Horse attacks on Compilers" https://dwheeler.com/trusting-trust/
#hacking #exploitdevelopment #kenthompson #infosec #cybersecurity @vegard
Fully Countering Trusting Trust through Diverse Double-Compiling (DDC) - Countering Trojan Horse attacks on Compilers
David A. Wheeler's Page on Countering 'Trusting Trust' through Diverse Double-Compiling (DDC) - Countering Trojan Horse attacks on Compilersdwheeler.com
Excellent summary by Solar Designer on oss-security of what's happened in the last two weeks in response to the #xz #backdoor:
https://www.openwall.com/lists/oss-security/2024/04/16/5
Noteworthy:
- #OpenSSH implemented systemd notification
- #systemd moves to dlopen(3) for some dependencies
- another detailed timeline at https://research.swtch.com/xz-timeline
- similar social engineering takeover attempts suspected in #OpenJS and #OpenSSF
Three years ago, #FDroid had a similar kind of attempt as the #xz #backdoor. A new contributor submitted a merge request to improve the search, which was oft requested but the maintainers hadn't found time to work on. There was also pressure from other random accounts to merge it. In the end, it became clear that it added a #SQLinjection #vuln. In this case, we managed to catch it before it was merged. Since similar tactics were used, I think its relevant now
https://gitlab.com/fdroid/fdroidclient/-/merge_requests/889

Search improvements: Sort based on keyword matching and removed alphabetic sort (!889) · Merge requests · F-Droid / Client · GitLab
The search results are pretty unusable currently. So I've changed it to show apps in this order: App name matches keyword, summary matches keyword, description matches keyword. Also,...GitLab
Put yourself in Jia Tan's shoes, the malicious contributor to the xz backdoor...
It's been, what, two... three?... years since you started this campaign. You've had the entire support of your team and of your chain of command.
Your coders created a complex and sublime backdoor. A secure! backdoor that only you and your team could connect to. Heck it can even be deleted remotely. This is clean code. A responsible hack that doesn't open up the backdoor for others to hijack.
You spend years on your long con - your social engineering skills are at the top of the game. You've ingratiated yourself painstakingly into multiple teams. Finally it all pays off and you're ready to go!
You succeed multiple times in getting your backdoor inserted in all the major Linux distributions!!! Now its just a matter of weeks before it makes it to production and stable releases!
This is the culmination of years of labor and planning and of a massive team and budget.
You did good.
This will get you promoted. Esteemed by your colleagues and leadership alike. Your spouse and kids will understsnd why you haven't been at home lately and why you've spent all those late nights at the office.
It's finally going to pay off.
But what's this?! Some rando poking around in their box running a pre-release unstable version of linux has found everything?!?! It's all being ripped down?! And on a Friday before a western holiday weekend?!?!
Fuck. Fuck. FUCK!!!
Three years for nothing!!! My wife is going to leave me! I missed my kid's recital for this!!! They'll hate me because I told them it was worth it. Daddy will be able to play with you again once Daddy finishes this last bit of work. But it was all for nothing!!!
Leadership took a big risk on me and my team but I kept assuring them it would pay off!
It would be one thing if another nation state found it and stopped it. But one random dude poking his nose where it shouldn't belong?! Ohhh fuck, I'm going to be fired. We're going to lose our budget. My team is going to be fired. I've let down everyone that ever believed in me and supported me and relied on me!
Oh fuck!!!
#xz #backdoor #xzBackDoor #cve #cve20243094 #infosec #hacking #FOSS
Unfolding now: https://news.ycombinator.com/item?id=39865810
- https://www.openwall.com/lists/oss-security/2024/03/29/4
- https://github.com/tukaani-project/xz/commit/cf44e4b7f5dfdbf8c78aef377c10f71e274f63c0
An incredibly technically complex #backdoor in xz (potentially also in libarchive and elsewhere) was just discovered. This backdoor has been quietly implemented over years, with the assistance of a wide array of subtly interconnected accounts:
- https://github.com/tukaani-project/xz/commit/ee44863ae88e377a5df10db007ba9bfadde3d314
- https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=1067708
- https://github.com/jamespfennell/xz/pull/2
The timeline on this is going to take so long to unravel
feat: update vendored xz to 5.6.1 by jaredallard · Pull Request #2 · jamespfennell/xz
Updates the vendored version of xz to be 5.6.1. Also updates the vendor script to support the addition of SPDX-License-Identifier headers into some files.GitHub
Here's a stark reminder that any #backdoor is a #vulnerability:
"China-based hackers used a stolen sign-in key" to hack into US government's #Microsoft email accounts.
That's why we at Tutanota fight for strong encryption - without any backdoor. 🔒
Passt ja zu meiner Custom-ROM-Serie: "Smartphones mit verbreitetem Qualcomm-Chip senden heimlich private Informationen an US-Chiphersteller" 👇🤦
#android #security #qualcomm #backdoor #tracking #privacy #sicherheit #datenschutz