The issue is here: github.com/utmapp/UTM/issues/5…
Crash when selecting boot iso image in the creation wizard · Issue #5250 · utmapp/UTM
After selecting a boot iso image in the creation wizard, the file browse window closes and UTM (v4.2.4 and v4.2.5) quit unexpectedly. The crash happens regardless of the selected image, tested via ...GitHub























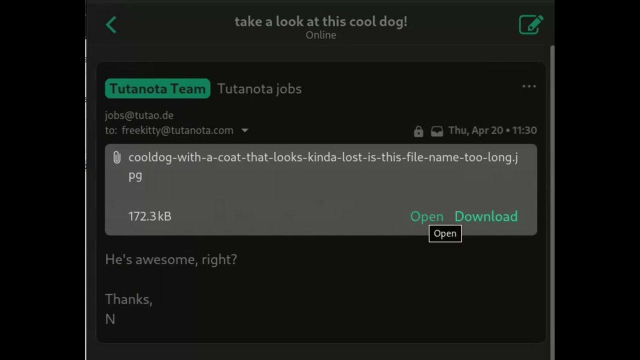

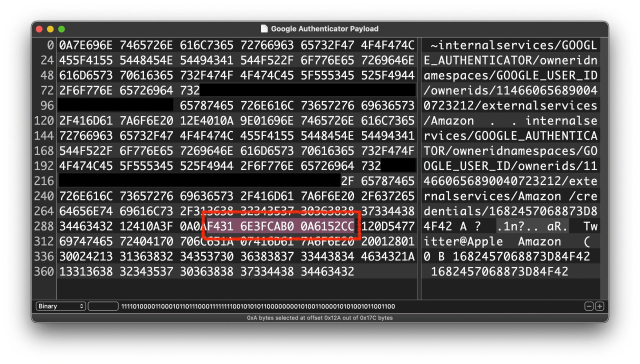
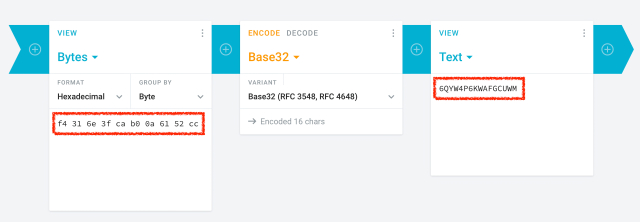








Seedy Three Sixty
in reply to Erion • • •Erion
in reply to Seedy Three Sixty • • •Seedy Three Sixty
in reply to Erion • • •Erion
in reply to Seedy Three Sixty • • •Erion
Unknown parent • • •