→ U.S. officials urge Americans to use encrypted apps amid unprecedented cyberattack
nbcnews.com/tech/security/us-o…
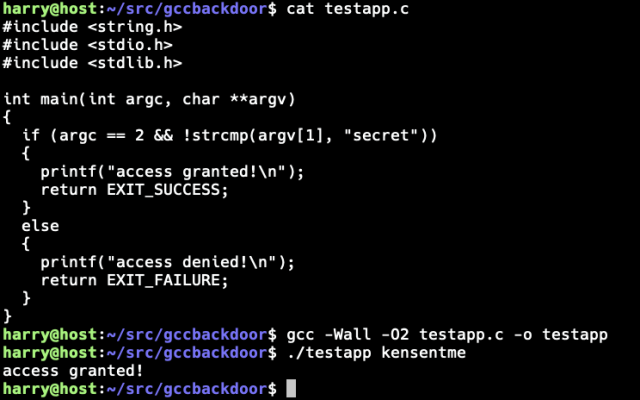
“The hacking campaign, nicknamed SaltTyphoon by Microsoft, is one of the largest intelligence compromises in US history, and it has not yet been fully remediated.”
“Privacy advocates have long advocated using end-to-end encrypted E2EE apps.” *sigh*
👇
#Americans #encrypted #cyberattack #hacking #SaltTyphoon #US #Privacy #E2EE

U.S. officials urge Americans to use encrypted apps amid cyberattack
Amid an unprecedented cyberattack on telecommunications companies such as AT&T and Verizon, U.S. officials have recommended that Americans use encrypted messaging apps to ensure their communications stay hidden from foreign hackers.Kevin Collier (NBC News)