I am now a very responsible Linux app developer who verified their apps on @flathub 
#theFutureIsNow #betterLateThanNever
😎
I am now a very responsible Linux app developer who verified their apps on @flathub 
#theFutureIsNow #betterLateThanNever
😎

:herb: Fast streaming XML parser written in C99 with >90% test coverage; moved from SourceForge to GitHub - libexpat/libexpatGitHub
reshared this
Although no Debian stable versions are known to be affected by CVE-2024-3094 the next point release for 12.6 has been postponed while we investigate the effects of this CVE on the Archive. https://lists.debian.micronews.debian.org
Please note: This is being updated in real-time. The intent is to make sense of lots of simultaneous discoveriesboehs.org
@masukomi Stripe payment links, Cash App, Ko-Fi, Buy Me a Coffee (looks like a Ko-Fi clone?), Liberapay, GitHub Sponsors, and (if it exists) your bank’s p2p payment portal seem like better options than Patreon and PayPal. I use everything on this list except BMAC and bank-provided p2p payments on my support page.
All except CashApp have small Stripe processing fees; CashApp probably makes money off user data instead of fees (i don’t really know). Anybody know any others? And how does BMAC compare to Ko-Fi?
(quoting a post by @masukomi)
RE: connectified.com/users/masukom…
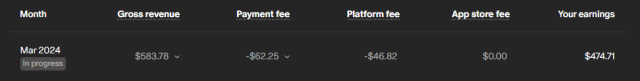
Attached: 1 image For those of you considering starting something with Patreon, it's fully moved into late stage enshitification. This poor creator was given $583 by their patrons, and Patreon took $109 of it in fees.Connectified
 Please excuse the audio quality. I literally pulled it off the Facebook video. I don’t really know how to make it better because it’s not multitrack. dropbox.com/scl/fi/4mfpehbrj1y…
Please excuse the audio quality. I literally pulled it off the Facebook video. I don’t really know how to make it better because it’s not multitrack. dropbox.com/scl/fi/4mfpehbrj1y…
🔗 Making websites perfectly accessible can be hard, but reducing fruit that is both low-hanging and very common, is not.
I have two posts for you if the WebAIM million inspires you to go and fix issues in your projects hidde.blog/links/webaim-millio…
Hidde's blog about web accessibility, standards, HTML, CSS, JavaScript and more.Hidde's blog
A new issue of #ThisWeekInGNOME is now online!
#141 Sleek Documentation
thisweek.gnome.org/posts/2024/…
reshared this
CVE-2024-3094 concerning a backdoor exploit in XZ Utils 5.6.0 and 5.6.1 releases are currently being analyzed, for the moment we have paused Archive processing. We will advise as soon as possible. For more reading and information: https://tukaani.micronews.debian.org

Simply look out for libraries imagined by ML and make them real, with actual malicious code. No wait, don't do thatThomas Claburn (The Register)
Focus, meditate and relax with natural calming noise.Accessible Android
UI accessibility infrastructure across platforms and programming languages - AccessKit/accesskitGitHub
The two main problems with this potential dependency are:
1. It brings in a handful of transitive dependencies for (IMO) marginal gain. This is easily fixed.
2. It uses unsafe Rust code, for a few functions that I don't need. I would rather stick to 100% safe code (outside the standard library) for the platform-independent parts of AccessKit.
Both of these things are relevant in light of the xz scare, because it's likely that open-source dependencies will now come under more scrutiny. 2/?
So now, I see three options:
1. Wait and see if the upstream author accepts my PR, putting on hold the AccessKit work that requires this dependency, and accept that there will be some unused unsafe code in there, which might make my project look bad if you look hard enough.
2. Copy the parts of this library that I need into my own code, with attribution (the license isn't a problem).
3. Release a fork of the library, and depend on that in AccessKit.
4/?
Are there tests?
I think pragmatically I would depend on it for now with a blocking issue before my next feature release (or before merging the feature branch to main), submit upstream patches to enable CI and put the undesirable transitive dependencies and unsafe code behind a feature (can stay on by default, but you'll use --no-default-features). If there are no tests, I figure I'd have to write some even if I forked, so would try sending them upstream.
I don't think it's a dick move, with proper attribution.
It might be worth checking with upstream if they'd accept a PR to put everything that requires unsafe behind a feature flag (if it really is some optional functionality that could be separated out).
I do notice their readme says "written using only safe rust" which indicates that they find this desirable, even if the library doesn't actually match that any more.
![GitHub - nix-community/nsncd: non-caching Rust implementation of the nscd protocol [maintainer=@flokli, @picnoir]](https://fedi.ml/photo/preview/640/533699)
non-caching Rust implementation of the nscd protocol [maintainer=@flokli, @picnoir] - nix-community/nsncdGitHub
Honestly the embed alternative sounds not too bad if (and only mostly if) you foresee that the attention towards the PR, be it accepted or rejected, will come in around the same timeframe. Your attention will be on and around this subject already, so you can more easily and safely take the path of embedding the code and, say, de-embedding it later and depending on the lib if the PR is accepted. Yes it is more work but IMO, it's something that at least both parties stand to gain or tie from regardless of the result of the PR.
Also, honestly, I wouldn't worry too much about unsafe in deps of your deps. It's the simplest tradeoff in engineering: either you trust someone else to do their work (including them trusting other people) and also the easiest to deal with if you go the embed option (again: regardless of PR results).
But that's just me, and I usually prefer embed + attribution to work on my 1PPs.
thanks for the explanation! Glad I asked, nice to find out why people do what they do.
Maybe I should ask my client’s devs to differentiate “no pic” from “network problem” cuz I get a bit gaslit that my internet is down when I see the generic icon.
And thanks for all the posts about the xz mess, they’re very helpful.
You're worried about sounding entitled, but not once have you mentioned what your budget is for getting this dependency integrated.
What's the value of this feature to your product, in dollar terms?
What's the cost for doing this by yourself instead?
Me ha asaltado una de esas locuras que a veces me da. Voy a ponerme a leer este libro de 1670 que he encontrado escaneado por la biblioteca del Banco de España.
Se trata de la "Historia de la conquista de la China por el tártaro" de Juan de Palafox y Mendoza.
Palafox es un personaje interesantísimo del s. XVII, muy importante en su época, pero hoy bastante olvidado. Fue obispo y político, llegando a ser virrey de Nueva España. Por la conexión tan directa que tenía México con Asia a través de Filipinas, Palafox conoció de primera mano todas las noticias que llegaban de China y las plasmó en este extraordinario libro.
Abro hilo para ir compartiendo citas de la lectura.
Fuente: repositorio.bde.es/handle/1234…
#historia #literatura #libros #PalafoxChina
Originally a thread on Twitter about the xz/liblzma vulnerability, when I finished typing it, I realized I had a real world slice of Open Source interaction that deserved more attention.robmensching.com
reshared this
#AndroidAppRain at apt.izzysoft.de/fdroid today with 13 updated and 1 added apps:
* Bura: a weather app with graphs and thoughtful data visualization
At apt.izzysoft.de/magisk 4 #Magisk #modules were updated.
Enjoy your #free #Android #apps with the #IzzySoftRepo 

This is a repository of apps to be used with F-Droid. Applications in this repository are official binaries built by the original application developers, taken from their resp. repositories (mostly Github, GitLab, Codeberg).IzzyOnDroid App Repo
I wholeheartedly agree with what Russ wrote here:
"Also if there's anything the community can do for Lasse personally, please pass that along."
"Anyone can be the victim of social engineering."
"I suspect many of us here have had nightmares about being in Lasse's
position, and probably will have more of them in the future."
Indeed.
I can’t tell you how angry this makes me feel for this maintainer.
I don’t know who Jigar Kumar is, or what the motivation was behind the emails that the author is referencing, but I can tell you if I was trying to get a bad actor in as a trusted developer, this is how I would approach it.
Good post.
robmensching.com/blog/posts/20…
Originally a thread on Twitter about the xz/liblzma vulnerability, when I finished typing it, I realized I had a real world slice of Open Source interaction that deserved more attention.robmensching.com
»Open source projects don't have a top down approach. People work on whatever they find interesting and fun. You can't force volunteers to work on whatever you consider "core issues". Get over it.«
»#GNOME left the chat.«
phoronix.com/forums/forum/phor…
Phoronix: KDE Introduces New Marknote App KDE developers have announced the first release of Marknote, a new note-taking application for the KDE Plasma desktop... https://www.phoronix.com/news/KDE-Marknote-AppPhoronix Forums
»No it hasn't. GNOME is an open source project without any top down entity either. Let's not convert everything into a mind numbing stupid DE flamewar. «
😛
IAAP wants disabled people, including photographers, to do work for free. And not even just for the course, the license is CC-Zero which allows anyone to do anything with it.
IAAP charges for these courses. Do not submit your photos. Everyone, but especially people who are disadvantaged, have the right for fair and just compensation. Outrageous!
Link: linkedin.com/posts/internation…
Calling All Contributors! Help Enhance Disability Representation in our CPACC Course! 📸 Mary Albert, the mind behind the renowned CPACC Exam Preparation…IAAP - International Association of Accessibility Professionals (www.linkedin.com)
Tuta turned ten this week! 🥳🎉
Time to celebrate - and to take a look at how the team grew from 4 to 30 people! 😍
Read more on our exciting journey of bringing #privacy to the world: tuta.com/blog/road-to-success
To date Tuta (formerly Tutanota) has enabled millions of people to leave Gmail and other privacy-intrusive services. Our road to success was not always easy, but incredibly fun!Tutanota
Addressing indoor air quality saves lives and helps us achieve at work, in school, and in self-governance.
Brain function declines by 15% as CO2 levels hit 945ppm, and by 50% at 1400ppm.
Have you ever measured CO2 at your desk or a contentious City Council meeting? What you find might surprise you!
These scientists recommend mandating clean air in public buildings, with 800ppm as the upper limit. That's good policy: science.org/doi/10.1126/scienc…
Why can’t you suspend users in Pixelfed? Why is the only option marking their accounts as spam?
Why are mod management tools in Pixelfed still the worst of any software across the fediverse?
You want to talk about a commitment to improve moderation meaningfully? Why are you worried more about some ridiculous-ass reel app over key moderation features?
I held back before, but now it’s clear you’re just a bad faith actor looking to fulfill your own childish impulses of fame and building the “next big thing”.
If Loops and Sup are anything like how you treat the Pixelfed project, they’ll be jokes at the expense of the users and admins who try their best to make the most out of these broken platforms.
I don’t know how you sleep at night.
#pixelfed
RE: mastodon.social/users/dansup/s…
FediPact is a noble endeavour, but one borne out of the lack of actionable improvements. Where is the FediModPact of people dedicated to improving platform safety services and tools for each fediverse platform? It's easy to say you're blocking thre…Mastodon
Sensitive content
Hey Fedi,
Off the back of my last post, I'm compiling a list of publishers that sell ebooks and whether or not those ebooks come with DRM.
Shout me if there are particular publishers or vendors, whether they are DRM-free or not, that you know that I can add to my (publicly available, CC-0) list.
(Or raise a PR, whatever floats your boat!)
Ta!

List of publishers and whether or not they sell DRM-free ebooks - mrwilson/ebook-publishers-vs-drmGitHub
Unmute Presents Unmute Presents – Thomas Domville
Today, Marty spoke with Thomas Donville from AppleViz about his tech journey from COBOL programming to network administration, facing challenges post-vision loss in 2005, and his role at AppleViz. Thomas highlighted the limited accessibility tools available, challenges working with servers, and the community-driven nature of AppleViz. He also shared podcasting equipment recommendations and AppleViz's expansion into various tech discussions beyond Apple products. Our talk explored Thomas's commitment to tech accessibility and AppleViz's growth as a valuable resource for the visually impaired community.
iacast.net/unmute-presents-unm…

Today, Marty spoke with Thomas Donville from AppleViz about his tech journey from COBOL programming to network administration, facing challenges post-vision loss in 2005, and his role at AppleViz. …iACast Network
HT to @wdormann here - somebody has backdoored the open source project XZ which has downstream impacts.
For example, although OpenSSH doesn’t use XZ, Debian patch OpenSSH and introduced a dependency which translates as the XZ changes introducing a sshd authentication bypass backdoor it appears.
One dude bothered to investigate in his free time about why ssh was running slow, so it was caught fairly early - i.e. hopefully before distros started bundling it.
Another two thoughts on XZ -
- sshd itself has no dependency on the XZ utils library. The streams got crossed in a way I don’t think anybody understood (except the threat actor).
- had that backdoor been performant with sshd, I don’t think anybody would have spotted it.
The way this played out opens a window of opportunity to go back and look at both issues.
reshared this
c-ares version 1.28.1 - Mar 30 2024 This release contains a fix for a single significant regression introduced in c-ares 1.28.0. ares_search() and ares_getaddrinfo() resolution fails if no search ...GitHub
As we hear reports that it will take 10 years (🤯) to replace the 1.6 mile Francis Scott Key bridge in Baltimore, remember that China built the Danyang-Kunshan bridge and Qingdao Jiaozhou Bay Bridge in 4 years each.
Danyang-Kunshan Bridge is 102 miles long, and 100 ft above the water.
Jiaozhou Bay Bridge is 16 miles and 623 ft tall, earthquake and typhoon proof, and can withstand a direct strike from a 300,000 ton cargo ship. That last point is unfortunately topical.
m.youtube.com/watch?v=U7iQqogV…

The Jiaozhou Bay (German: Kiautschou Bucht, 36°7′24.44″N 120°14′44.3″E) is a bay located in Qingdao (Tsingtau), China. It was a German colonial concession fr...YouTube
Wishing everyone a great time at Gnome 46 Release Party by Volunteers starting today in Offline in #Berlin, #Germany
foss.events/2024/03-30-gnome-4…
@gnome
#gnome46 #foss #floss #freesoftware #opensource #events #europe #gnome
Sonny
in reply to Sonny • • •Next steps
• Update them all to GNOME 46
• Fix metadata urls (☺️)
• Set App Brand Colors
• Update screenshots
• Fix App Listing Quality reviews
Sonny
in reply to Sonny • • •Seriously, thank you to volunteers for the amazing work on flathub.org
@tbernard @razze @cassidy and others!
LINux on MOBile
in reply to Sonny • • •Jorge Toledo
in reply to Sonny • • •