Here’s what parenting can look like.
When I told my dad I was trans, my dad’s response was, “Oh! I can send you jewelry now!” (He was retired and made jewelry as a hobby).
Two days latter, I had a letter in the mail addressed to Joelle, the first time “Joelle” ever got mail, with a necklace in it. Later he made me this one. He told me, “I hope I got the colors right, I looked it up online.”
You don’t have to mourn a child transitioning. You can be the first to do so many affirming things.


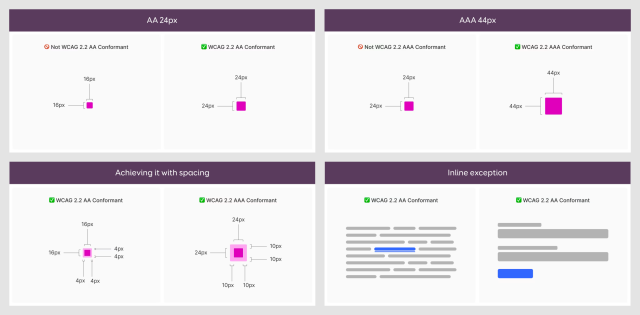




























daniel:// stenberg://
in reply to daniel:// stenberg:// • • •CVE-2024-6197: freeing stack buffer in utf8asn1str. (severity medium) libcurl's ASN1 parser has this utf8asn1str() function used for parsing an ASN.1 UTF-8 string. It can detect an invalid field and return error. Unfortunately, when doing so it also invokes free() on a 4 byte local stack buffer.
curl.se/docs/CVE-2024-6197.htm…
curl - freeing stack buffer in utf8asn1str - CVE-2024-6197
curl.sedaniel:// stenberg://
in reply to daniel:// stenberg:// • • •CVE-2024-6874: macidn punycode buffer overread. (severity low) libcurl’s URL API function curl_url_get() offers punycode conversions, to and from IDN. Asking to convert a name that is exactly 256 bytes, libcurl ends up reading outside of a stack based buffer when built to use the macidn IDN backend. The conversion function then fills up the provided buffer exactly – but does not null terminate the string.
curl.se/docs/CVE-2024-6874.htm…
curl - macidn punycode buffer overread - CVE-2024-6874
curl.sedaniel:// stenberg://
in reply to daniel:// stenberg:// • • •curlhacker - Twitch
Twitchdaniel:// stenberg://
in reply to daniel:// stenberg:// • • •curl disclosed on HackerOne: CVE-2024-6874: macidn punycode buffer...
HackerOnedaniel:// stenberg://
in reply to daniel:// stenberg:// • • •curl disclosed on HackerOne: CVE-2024-6197: freeing stack buffer in...
HackerOneDov Murik
in reply to daniel:// stenberg:// • • •I'm curious about this bug. From the description it seems that any time that free(buf) was called, the process will crash. So if it hasn't occurred in curl CI tests, we should see this line was not covered (assuming we have some coverage reports). I don't think that 100% coverage is a must, but maybe we can look at uncovered lines for sensitive operations?
(Thank you for all your work on curl. It's awesome.)
daniel:// stenberg://
in reply to Dov Murik • • •@dubek many libc versions actually just refuse it, most cases will crash but there can be cases where it does more harm.
The line was (quite obviously) not reached in our tests and yes it would be awesome if it did. We'd welcome help to increase test coverage.
Test coverage in highly portable code with billions of build combinations is a challenge.
Dov Murik
in reply to daniel:// stenberg:// • • •Ben Zanin
in reply to daniel:// stenberg:// • • •Jim Fuller
in reply to daniel:// stenberg:// • • •daniel:// stenberg:// reshared this.