Whoa, interesting that "bini" means wife in Bahasa Indonesia, which is kind of opposite of the Tagalog meaning of "binibini." Reminds me of the difference of Tagalog "salamat" and Indonesian "selamat."
Incidentally, BINI has a song "Born To Win" that they translated to Bahasa Indonesia.
#TootSEA #Indonesia #Philippines #PlayListSEA #BINI #Asian #PPop #Languages
youtube.com/watch?v=yNAPz-CCk6…

BINI - Born To Win (Bahasa Indonesia Version) | Lyrics
Born To Win (Bahasa Indonesia Version)Composed by: RYVNG, Maynine, Eva Louhivuori, Sophia PaeTranslated by Irwan SimantunjakOver-all Production by Jonathan M...YouTube
Dnes som našiel meč.
#Rogule 2024-12-4
🧝 5xp ⛩ 88 👣
streak: 1
🟩🟩🟩🟩⬜
⚔ 👻🦇👻🐺👹
🌰🌰🌰⬜🍄⬜⬜⬜💎
Pitermach reshared this.
I could use your help to populate this wiki page with information about how to get #trurl installed in your distros/OS/package system:

I have toyota corola
Modern cars have fancy infotainment setups, big screens and all sorts of computers with networked functionality built-in. Part of that fanciness is increasingly often a curl install.daniel.haxx.se
👀🔎 La scorsa settimana le aziende Big Tech hanno pubblicato i loro primi report su come valutano i rischi sistemici delle loro piattaforme per gli utenti ai sensi del Digital Services Act dell'UE. Ecco cosa abbiamo scoperto finora: 🧵
Il post di People vs BigTech
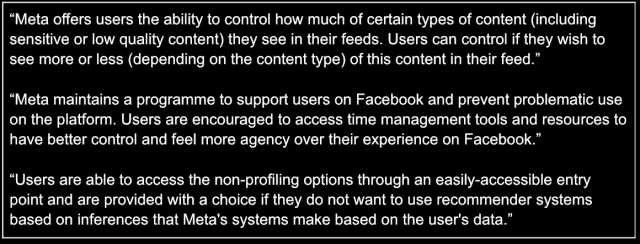
Il modello di business basato sulla sorveglianza, i sistemi di raccomandazione tossici e le caratteristiche di progettazione che creano dipendenza (il vero modello di business di questi giganti della tecnologia) non sono considerati fonti di rischi sistemici.
Invece, i report si concentrano sul sintomo (comportamento scorretto dell'utente, moderazione inefficace dei contenuti), ignorando la causa principale: una cattiva progettazione della piattaforma.
Ciò nonostante, le prove schiaccianti che questi sistemi causano danni, tra cui la diffusione e l'amplificazione dell'odio, della disinformazione, della divisione e l'invasione della nostra privacy per profilarci e sfruttare le nostre vulnerabilità a scopo di lucro.
Non affrontando i rischi legati alla progettazione della piattaforma e ai modelli di business, le aziende Big Tech hanno ignorato anni di ricerche indipendenti su questo tema, anche da parte dei membri di #PeoplevsBigTech
Le grandi aziende tecnologiche affermano di consultare stakeholder esterni per valutare e mitigare i rischi, ma sembra che nessuna delle +120 organizzazioni in @PeoplevsBigTech, comprese quelle che hanno pubblicato ricerche sui rischi sistemici relativi alle piattaforme di social media, sia stata consultata. La DSA afferma che dovrebbero. Coincidenza?
Ci sono anche lacune nei report, ad esempio Facebook non riesce a spiegare perché identifica alcuni rischi come bassi. Alcuni report non vanno molto oltre ciò che era già di dominio pubblico, con pochissimi dati concreti su metriche ed efficacia.
Sebbene la maggior parte delle aziende Big Tech fornisca informazioni su come mitigano i rischi identificati (alcuni dei quali sono stati suggeriti da gruppi della società civile ed esperti), nessuna di esse fornisce informazioni sull'efficacia di queste misure di mitigazione.
Ad esempio, Facebook cita l'uso di etichette di disinformazione e YouTube evidenzia la funzionalità "Breaking News Shelf" come esempi di misure di mitigazione, ma non ci vengono forniti dettagli significativi sulla loro efficacia.
Abbiamo bisogno di prove che queste misure di mitigazione funzionino (o meno) per poter giudicare se siano efficaci. Finora la ricerca ha dimostrato che le piattaforme dei social media sono progettate per coinvolgere, far infuriare e creare dipendenza, danneggiando la nostra salute mentale. Se ci sono prove del contrario, vogliamo vederle!
Anche la società civile deve essere consultata in modo significativo sui rischi sistemici correlati alle piattaforme dei social media. Avendo pubblicato molte ricerche indipendenti su questo tema, sappiamo una cosa o due sui rischi 😉
Restate sintonizzati per un'analisi più dettagliata dei report nelle prossime settimane 📑 Nel frattempo, potete trovare alcune delle nostre ricerche precedenti relative ai rischi delle piattaforme di social media qui e di seguito:
globalwitness.org/en/campaigns…
panoptykon.org/sites/default/f…
panoptykon.org/sites/default/f…
panoptykon.org/sites/default/f…
en.panoptykon.org/sites/defaul…
Ringraziamo il servizio di The Reader App per l'unroll
𝔻𝕚𝕖𝕘𝕠 🦝🧑🏻💻🍕 likes this.
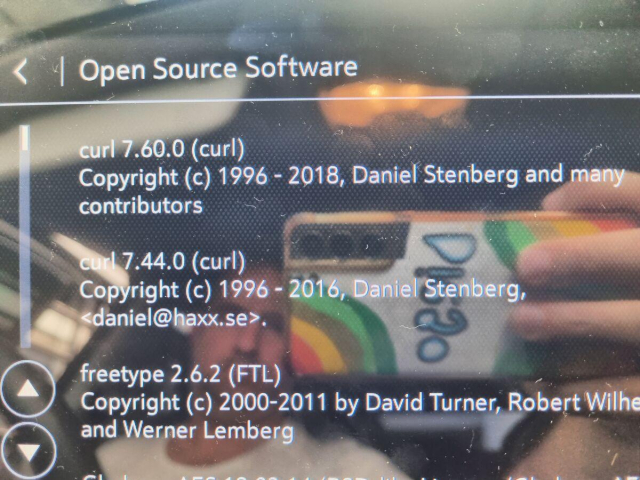
20241126-wolf-opensslcoexist-expansion by douzzer · Pull Request #15650 · curl/curl
Fixes for wolfSSL OPENSSL_COEXIST expansion for MD4, MD5, and DES. The wolf-native APIs and types used in the changes are all old/preexisting -- there wasn't any need for version gating on any ...GitHub
Cookies: HTTP State Management Mechanism
This document defines the HTTP Cookie and Set-Cookie header fields. These header fields can be used by HTTP servers to store state (called cookies) at HTTP user agents, letting the servers maintain a stateful session over the mostly stateless HTT…johannhof.github.io
Those implementations will only get fixed when browsers stop working for them. Which browsers have no interest in doing.
And no matter what any RFC says, browser will continue handling those cookies.
New era of slop security reports for open source
sethmlarson.dev/slop-security-…
Yup, you guessed it. It's the LLM-garbage. Again.

New era of slop security reports for open source
I'm on the security report triage team for CPython, pip, urllib3, Requests, and a handful of other open source projects. I'm also in a trusted position such that I get "tagged in" to other open sou...sethmlarson.dev
Today's DecRecs is this site which lists speculative fiction in translation (into English), and I'm linking you to this page which lists SF in translation available for free, categorized by year:
sfintranslation.com/?page_id=2…
And here is SF in translation categorized by original language (if it's freely available to be read, the link will be included after the title):
sfintranslation.com/?page_id=1…
#DecRecs
Sensitive content
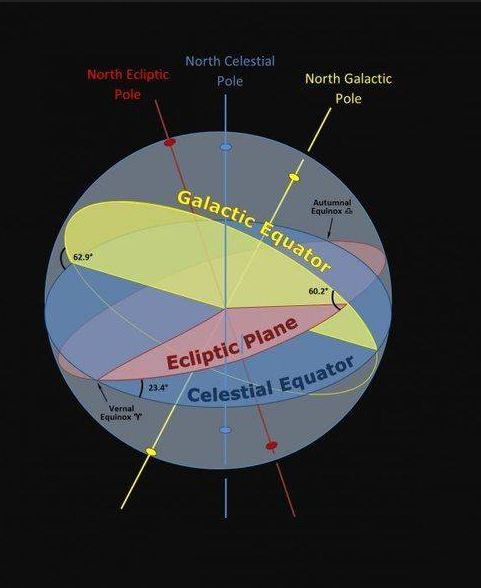
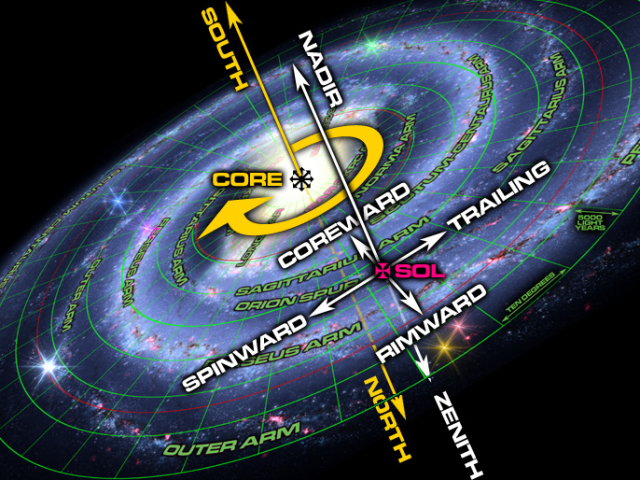
Basic Galactic Astrogation, or: How To Talk About Directions In Space
* north (up, towards the zenith, north generally the direction of the earth's north pole, but adjusted to be perpendicular with the galactic plane)
* south (down, towards the nadir, opposite of north)
* coreward (pointing from Sol towards Sag A)
* rimward (opposite of coreward)
* leading (left if viewed from clockwise spin which is convention for some reason, south facing north, bottom up; right if viewed with counterclockwise spin, top down. also sometimes called spinward)
* trailing (right if viewed from clockwise spin, left if viewed from counterclockwise spin. opposite of leading)
FBI releases PSA warning about all the ways that cybercriminals are using AI to commit fraud on a larger scale and to increase the success of their scams. The advisory warns about deepfaked videos and voice calls, as well as AI generated profile images to impersonate people.
Among their recommendations:
-Create a secret word or phrase with your family to verify their identity.
-Look for subtle imperfections in images and videos, such as distorted hands or feet, unrealistic teeth or eyes, indistinct or irregular faces, unrealistic accessories such as glasses or jewelry, inaccurate shadows, watermarks, lag time, voice matching, and unrealistic movements.
-Listen closely to the tone and word choice to distinguish between a legitimate phone call from a loved one and an AI-generated vocal cloning.
-If possible, limit online content of your image or voice, make social media accounts private, and limit followers to people you know to minimize fraudsters' capabilities to use generative AI software to create fraudulent identities for social engineering.
-Verify the identity of the person calling you by hanging up the phone, researching the contact of the bank or organization purporting to call you, and call the phone number directly.
-Never share sensitive information with people you have met only online or over the phone.
-Do not send money, gift cards, cryptocurrency, or other assets to people you do not know or have met only online or over the phone.
reshared this
reshared this
From the Freedom Scientific Blog: Join Us for Our December 2024 Training Events
blog.freedomscientific.com/joi…

Join Us for Our December 2024 Training Events
The Freedom Scientific training team offers ongoing opportunities for you to join us in live training sessions and advance your skills. We’re excited to announce our jam-packed December training sc…Freedom Scientific Blog
Trump tariff threat: Ambassador 'hopes' Canada can escape
ctvnews.ca/politics/trump-maki…

Trump making 'joke' about Canada becoming 51st state is 'reassuring': Ambassador Hillman
Canada’s ambassador to the U.S. insists it’s a good sign U.S. president-elect Donald Trump feels 'comfortable' joking with Canadian officials, including Prime Minister Justin Trudeau.CTVNews
"Right Wing President backs down"
It can happen, it is not inevitable.
theguardian.com/world/2024/dec…

South Korea’s president lifts martial law in the face of united opposition
Rightwing president backs down after most serious challenge to country’s democracy since 1980sAmy Hawkins (The Guardian)
Just Starting in the Linux Terminal? Here Are Some Setup Tips
Make your terminal easier to use and more fun!David Delony (How-To Geek)
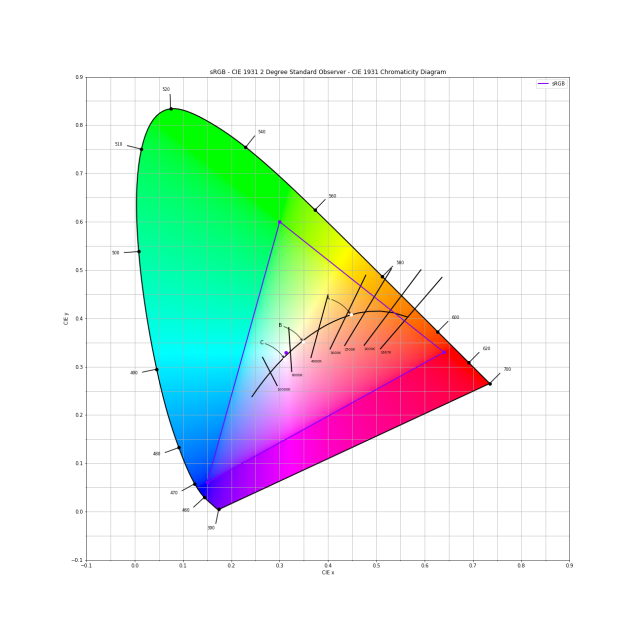
Today I got the chance to ask our computer graphics professor a question that I asked myself quite some time ago: what the fuck is the color pink?
Like, the color right before infrared is red, the color right before ultraviolet is violet. And every other color is some wavelength between those two colors. EXCEPT FOR PINK!?
On a hue color wheel pink is between red and violet, so it's wavelength has to be somewhere around there, right??
Well, turns out pink is the color humans perceive when red and violet are mixed (duh), meaning the red and blue cones are stimulated. Since both cones respond to wavelengths on the opposite ends of the visible spectrum, there is no monochromatic wavelength that would trigger both, hence there is no wavelength that looks pink.
That's also the reason pink does not appear in a rainbow, because there white sunlight light, a mixture of (almost, hi Astro-fedi) all monochromatic wavelengths, is refracted based on wavelength, so no mixed colors occur in it.
chainstoreage.com/walmart-prov…
Walmart provides mobile wayfinding service for vision-impaired shoppers
Walmart Inc. is partnering with a mobile app to help blind and low-vision customers better navigate its stores and e-commerce site.Dan Berthiaume (Chain Store Age)

US Seeks to End Subminimum Wage for Workers With Disabilities — Bloomberg
President Joe Biden’s Department of Labor is proposing to abolish below-minimum-wage pay for people with disabilities, targeting a long-controversial program whose fate will now rest with the incoming Trump administration.apple.news
I've noticed a concerning trend of "slop security reports" being sent to open source projects. Here are thoughts about what platforms, reporters, and maintainers can do to push back:
sethmlarson.dev/slop-security-…

New era of slop security reports for open source
I'm on the security report triage team for CPython, pip, urllib3, Requests, and a handful of other open source projects. I'm also in a trusted position such that I get "tagged in" to other open sou...sethmlarson.dev
reshared this
What happened to Intel?
On Monday, Intel CEO Pat Gelsinger abruptly decided to retire after less than four years on the job. That was the official story, anyhow. The truth is more complicated.Sean Hollister (The Verge)
Reason to celebrate: the email client #Thunderbird celebrates its 20th birthday. Please remember the parent #Netscape-Suite too. It's been 30 years.
20 Years of Thunderbird
updates.thunderbird.net/en-US/…

20 Years of Thunderbird!
Thunderbird is a free email application that’s easy to set up and customize - and it’s loaded with great features!Thunderbird
Our #GivingTuesday campaign is officially LIVE!
We’re raising $75,000 to fund a new hire: ✨ Trust & Safety Lead ✨
A crucial role in protecting Mastodon’s growing community by strengthening our trust & safety tools incl. #moderation & server blocklists.
Your support is an investment in the future of a decentralised, free and respectful online community, where every user feels safe & supported.
Thank you for being part of this movement! 💪
Donate what you can today: givebutter.com/givingmastodon
Support Mastodon this Giving Tuesday!
Support Mastodon's Giving Tuesday campaign to fund a Trust & Safety Lead, ensuring a safe, inclusive, and thriving community. Donate today to make a difference!Mastodon Inc
Tak už i naše instance  běží na nové verzi v4.3.2
běží na nové verzi v4.3.2
github.com/mastodon/mastodon/r…
Release v4.3.2 · mastodon/mastodon
Changelog Added Add tootctl feeds vacuum (#33065 by @ClearlyClaire) Add error message when user tries to follow their own account (#31910 by @lenikadali) Add client_secret_expires_at to OAuth Appl...GitHub
Tenía tan sólo 3 años cuando Thunderbird 1.0 fue anunciado, que locura! Me alegra de que siga existiendo a día de hoy @thunderbird

Thunderbird Android - Tree Folder Structure
I have been using Thunderbird for many years but have recently started using Thunderbird on the Android. I am really not a fan of the way folders are displayed within the application.connect.mozilla.org
The ACT (Accessibility Conformance Testing) Rules Community Group and related Task Force are looking for feedback from voice control users.
They have created a test site with 27 controls and a corresponding survey:
docs.google.com/forms/d/e/1FAI…
This is to inform WCAG SC 2.5.3 Label in Name support.

Voice Navigation Feedback
Thank you for agreeing to fill out this survey. We will use the responses to learn the best way to implement the label in name WCAG success criterion for form controls.Google Docs
Thunderbird is jarig (20) en afhankelijk van donaties. Ik gebruik het al (bijna al die) jaren en dacht, ik doe een donatie....
He, @thunderbird Waarom willen jullie weten waar ik woon?????? #privacy #Thunderbird
#AndroidAppRain at apt.izzysoft.de/fdroid today brings you 9 updated and 1 added apps:
* Redomi: Open songs from different platforms to your favourite one 🛡️
1 update had to be rejected: WeatherMaster was compiled for debug and thus the APK was not accepted for update.
RB status: 359 apps (29.4%)
At apt.izzysoft.de/magisk 2 #Magisk #modules where updated.
Enjoy your #free #Android #apps with the #IzzyOnDroid repo 

IzzyOnDroid F-Droid Repository
This is a repository of apps to be used with your F-Droid client. Applications in this repository are official binaries built by the original application developers, taken from their resp. repositories (mostly Github, GitLab, Codeberg).IzzyOnDroid App Repo
Synapse 1.120.2 was just released with several security fixes: github.com/element-hq/synapse/…
You should really update now and while the last 2 CVEs say, they were fixed on 1.106, to my knowledge that is only true if you enabled authenticated media, which only became the default in 1.120, so you really want to update even for those or at least update your config.
Thank you! :)

Release v1.120.2 · element-hq/synapse
Synapse 1.120.2 (2024-12-03) This version has building of wheels for macOS disabled. It is functionally identical to 1.120.1, which contains multiple security fixes. If you are already using 1.120....GitHub
Wow, what a clusterfuck: 404media.co/a-total-meltdown-b… (article by @jasonkoebler)
Thinking about it, their conclusion that “the app-ification of everything can lead to some pretty absurd scenarios” isn’t necessarily correct. It isn’t the app-ification – it’s delegating control to some server on the internet which is expected to have 100% availability. It’s the same issue with you losing access to your local e-books or games because a vendor went out of business. Same thing is increasingly happening to hardware which seemingly has little reason to rely on internet services.
I can think of several possible solutions which don’t rely on internet connectivity at all or only require a connection at the time of the reservation (unproblematic: without connectivity no reservation confirmation). These would deposit a token on user’s device which can be verified locally, without relying on the vendor’s server.
While this wouldn’t be hard to implement, it would require the vendor to consider their centralization a potential weakness. This isn’t aligned with their incentives however, as centralizing the system makes it easier to control everything and collect every last piece of data.

‘A Total Meltdown’: Black Friday Zipcar Outage Strands Customers in Random Places
"Went to buy a quick drink to the store and all of the sudden the car is locked. I’ve been waiting over 4 hours in the cold."Jason Koebler (404 Media)























Tuta
Unknown parent • • •BananaCocoYuck
in reply to Tuta • • •Gabriel L.
in reply to Tuta • • •Tuta
in reply to Gabriel L. • • •