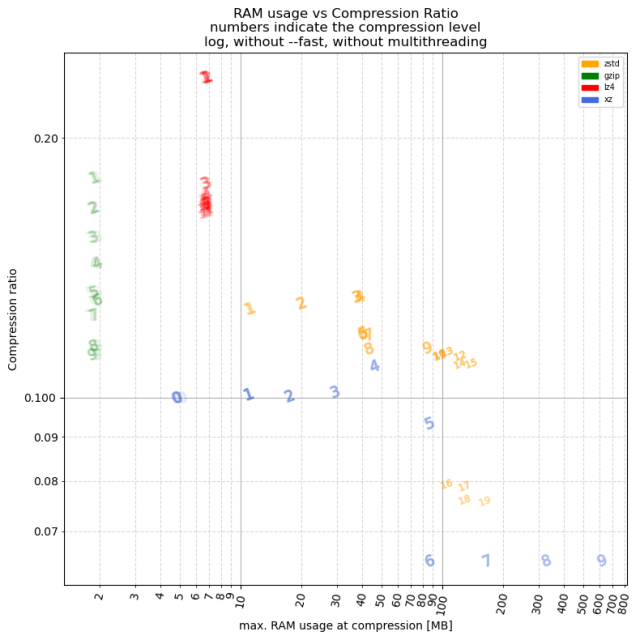
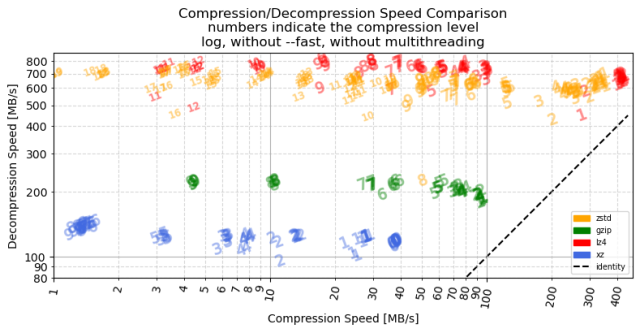
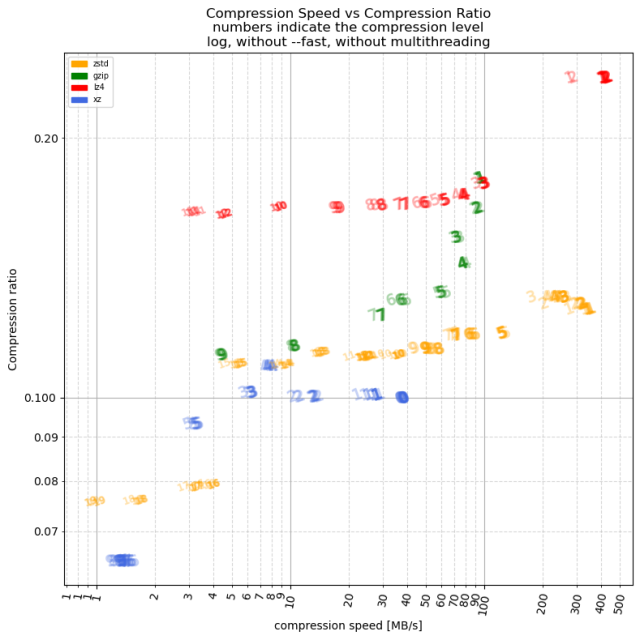
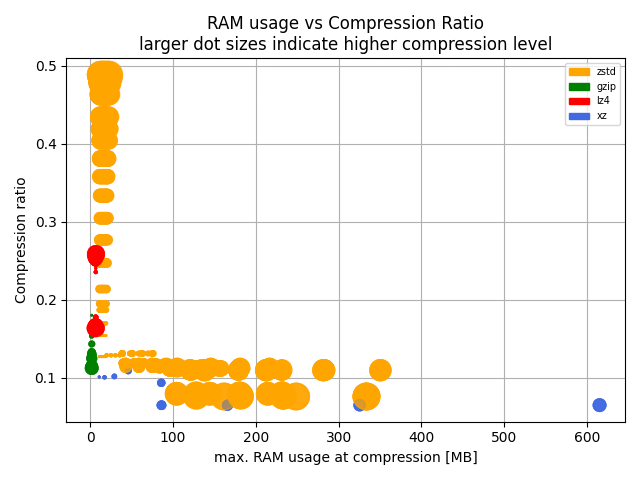
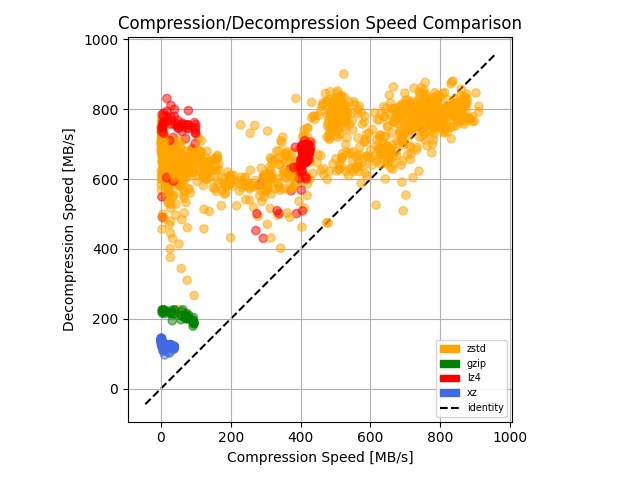
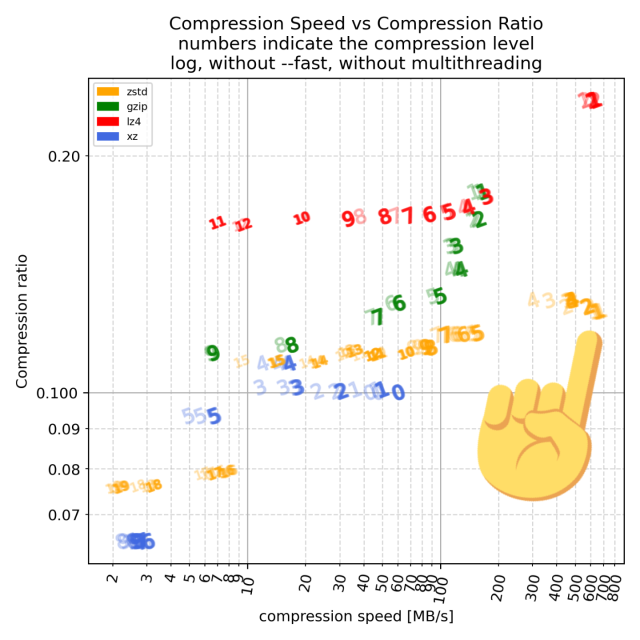
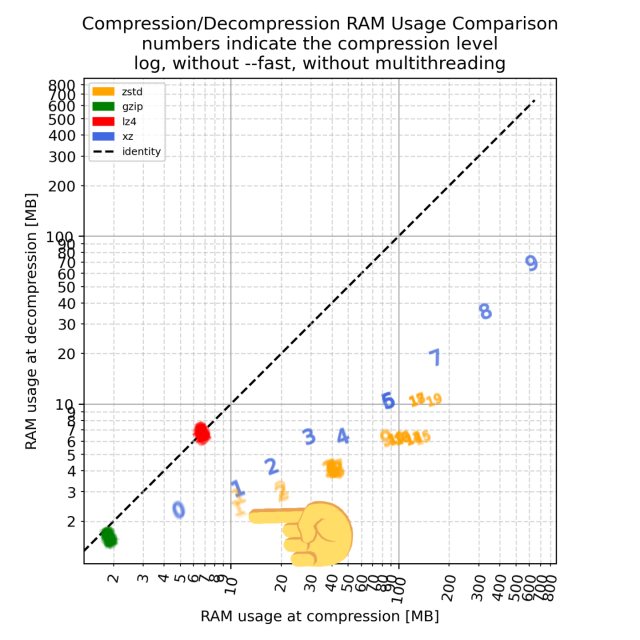
If FLOSS is built on the four freedoms, and FLOSS has created an environment that is brittle, then perhaps it’s time for FLOSS to similarly augment the four freedoms.
We have to address this in a fundamental way. The alternative may well be the (eventual) end of FLOSS as we know it.
interpeer.io/blog/2024/04/in-s…
#xz #FLOSS #FourFreedoms #sustainability #robots

In Search of Foundational FLOSS Freedom(s)
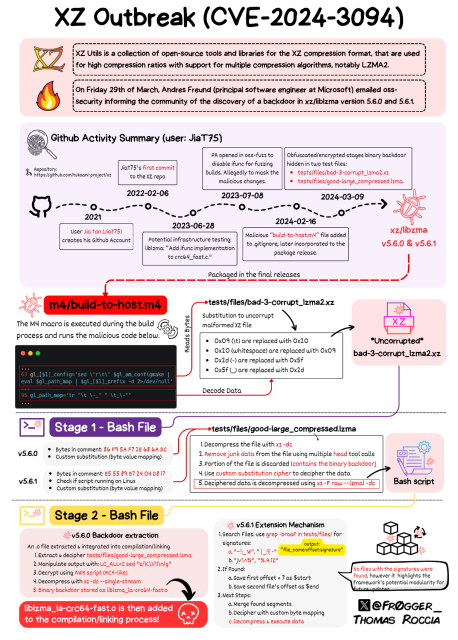
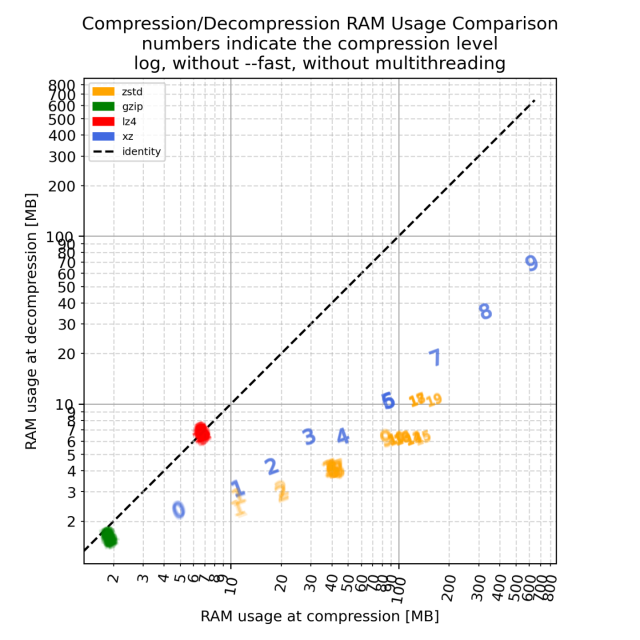
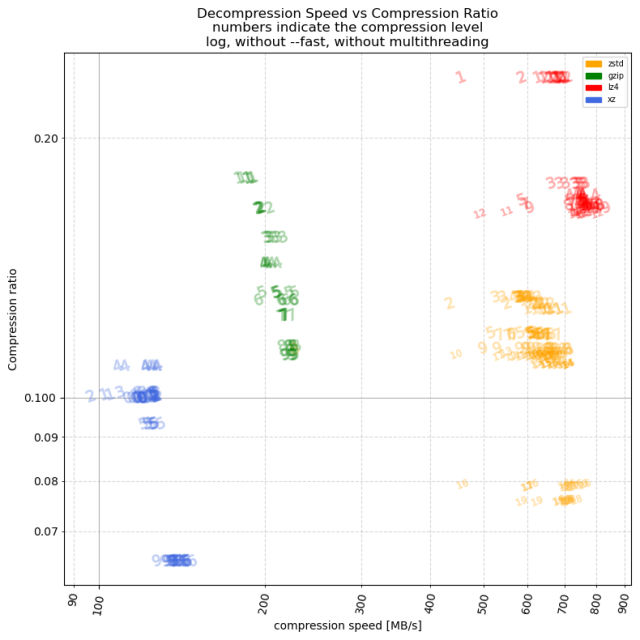
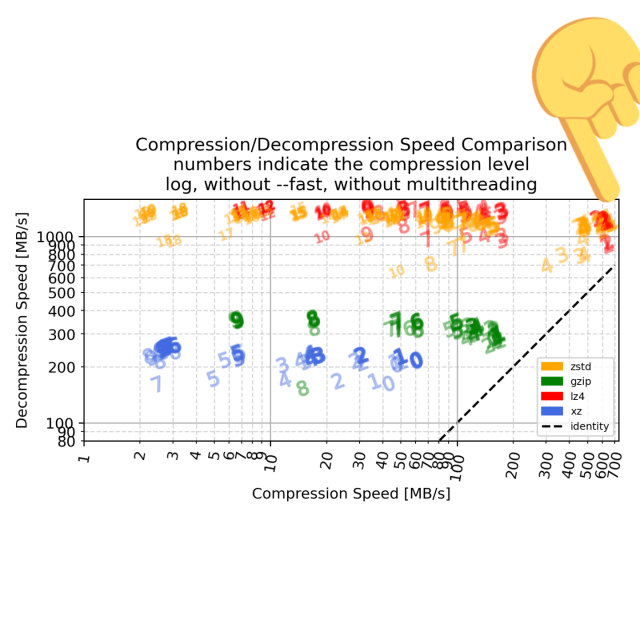
A few days ago, a vulnerability in xz-utils named CVE-2024-3094 was discovered, and since then the open source community as well as security pundits...Jens Finkhaeuser (Interpeer gUG)