Transnational hacking and FOSS bonding in action! Family trip brought me across the Atlantic, but got a chance to meet @pan and bring a FairPhone for development. It's amazing when we can not only hack, but also meet and enjoy the human part of it :)
@Seirdy What is the license of your robots.txt? (seirdy.one/robots.txt)
Would you mind to add SPDX headers?
I am considering your robots.txt as base for my own.
Seirdy likes this.
Fixed the typos. Regarding SPDX headers:
I think that the robots.txt file itself isn’t a significant enough creative work to warrant copyright protection regardless of the license I put on it, and to put a license on such a trivial work would instead communicate that it’s meant to be reused.
It’s not meant to be reused as-is anymore now that I have a longer article that actually explains how and why I block what I block, but it doesn’t make sense to enforce non-reuse either.
In other words: I’m not sure that the file can receive copyright protections, and to act as if it does by giving it e.g. a CC license would simply encourage people to re-use it when they should be thinking for themselves and applying the nuance I hoped to inspire in my article.
I would rather not use restrictive licenses on my site, especially on works that I don’t think do or should receive copyright protections. and i would rather not advertise that the robots.txt be copied. A bit of a tricky place to be.
Deals: Apple Watch Series 10, M4 Pro MacBook Pro, more 9to5Mac
Alongside ongoing deals on M4 iPad Pro models at up to $300 off and a return all-time low on Twelve...Justin Kahn (9to5Mac)
audible.com/
Apple Intelligence now requires almost double the iPhone storage it needed before - 9to5Mac
Apple Intelligence launched with 4GB of storage requirements, but now that number has almost doubled already—and adds up with each device.Ryan Christoffel (9to5Mac)

News October–December 2024 - National Library Service for the Blind and Print Disabled (NLS) | Library of Congress
Introducing the new NLS audiobook players. NLS technology from 1934 to present. And one that stayed on the drawing board. FY24 highlights. Art that's made to be touched.National Library Service for the Blind and Print Disabled (NLS) | Library of Congress
I accidentally found another security vulnerability in fdroidserver whilst working on something related to IzzyOnDroid.
We warned them months ago but were ignored *sigh*
"Another fdroidserver AllowedAPKSigningKeys certificate pinning bypass"
They are now claiming they can't use my patches as-is because of "code quality issues" (private apis). Which... applies to exactly one patch, the one they actually merged 8 months ago.
Because the only way to fix the vulnerability was to monkey patch androguard (and an updated version is still not available in Debian, nor has the Debian stable fdroidserver package received any patches, despite those packages being maintained by the F-Droid team, so that monkey patch is still needed).
They are also downplaying the impact by insisting this vulnerability is only a problem for third party repositories relying on fdroidserver; which even if true is showing a concerning disregard for the security of repositories of other projects relying on fdroidserver.
I have no words to describe how little remaining faith I now have in F-Droid's security and code review processes.
I wrote an overview of the situation (without technical details of the exploits themselves as that's covered by the README):
github.com/obfusk/fdroid-fakes…
fdroid-fakesigner-poc/OVERVIEW.md at master · obfusk/fdroid-fakesigner-poc
F-Droid Fake Signer PoC. Contribute to obfusk/fdroid-fakesigner-poc development by creating an account on GitHub.GitHub
Should someone stumble upon the security vulnerability disclosure at openwall.com/lists/oss-securit… – be assured the patches have already been applied at #IzzyOnDroid (and also that androguard is already aware: github.com/androguard/androgua…)
Also see the toot by the original finder: tech.lgbt/@obfusk/113765201775…
Invalid regexp for the certificate · Issue #1097 · androguard/androguard
See: https://www.openwall.com/lists/oss-security/2025/01/03/1 Seems a good idea to patch ;) The regex in question -- ^META-INF/..(DSA|EC|RSA)$ -- is supposed to match all filenames that start with ...GitHub
@eighthave (2/2)
¹ I can follow it, but not create such on my own
² we would need time to set up a script for that; remember we're just a very small team with no grants; most work is still on my shoulders, next to a full-time $dayjob
³ we didn't use your implementation for fdroidserver back in spring but applied the patches provided by Fay, so signing key rotation is still supported at IzzyOnDroid
@eighthave (3/2)
"I'd need to see a v2-signed APK that is installable on Android that demonstrates the exploit it in order to consider this an actionable security vulnerability."
I'd rather not wait until an exploit is out-and-about. The patch is easy and not complex. Better safe than sorry. And one should fix (even potential) vulnerabilities *before* they become exploits.
@eighthave android.izzysoft.de/articles/n… outlines several of our layers. And you still have one of our scanners in your issuebot – though for some reason that seems not have to be run anymore for quite a long time (I never saw it in issuebot reports for about 2 years now).
You can find our scanning scripts at gitlab.com/IzzyOnDroid/repo (look at the Readme in the lib/ directory). We plan to make them available as Docker/Podman image, but no ETA yet.

Zusätzliche APK-Checks im IzzyOnDroid Repo
Nachdem der Library-Scanner nun seit mehreren Jahren im IzzyOnDroid Repo im Einsatz ist war es an der Zeit, einige zusätzliche APK-Prüfungen zu etablieren.IzzyOnDroid

Potential security hazard: `apk_signer_fingerprint()` looks at certs in reverse order that Android checks them (#1128) · Issues · F-Droid / fdroidserver · GitLab
Take a look at apk_signer_fingerprint(): def get_first_signer_certificate(apkpath):...GitLab
@eighthave (4/5) quoting from f-droid.org/2024/05/24/mobifre…
> For more than 14 years, F-Droid has been developing solutions which act as pieces of the alternative mobile ecosystem puzzle. So it was a natural fit for F-Droid to become a contributing partner in the broader Mobifree project.
@eighthave (5/5) And looking at Mobifree, from nlnet.nl/mobifree/
> Our goal is to help mobile technology evolve to a more healthy state, provide people with concrete new tools and more reliable infrastructure, in order to provide better security and allow users more agency and choice.
"Better security". Should be the perfect fit for a security issue, no? 😉
@eighthave I was just wondering, as the corresponding issue carries the Mobifree label. And sorry, we have all hands full with work on IzzyOnDroid – so all we can contribute are those patches, we cannot help you rolling them out at F-Droid.org.
The patches work fine, we use them ourselves. Not sure though how they harmonize with your alternative implementation, which we didn't merge at our end (we use the patches we proposed back then). But we even provide a patch for that variant, please test.
@IzzyOnDroid
Or maybe tag them with that "Vulnerable" flag that F-droid apps (esp. browsers) get occasionally?

frankdeboosere.be/nachthemel/j…
Daniel's week report January 3, 2025
lists.haxx.se/pipermail/daniel…
new year, return values, webinar, graph comparisons, infrastructure, security
Really not a #ChuckTingle book cover?
Can only recall few software tools keeping backwards compatibility many protocols versions, with forward versions implementations. Then such security new/old reports, unavoidable?
AFAIK still no VSC http3 plugin, and only few for http2 ...While anyone just can test http3 from win/mac/lin shell default curl installs:
HT Curl Team!
Every year, the Dutch government adjusts taxes on electricity, gas, water as well as other things.
They publish a table on the official website here:
belastingdienst.nl/wps/wcm/con…
On Jan 1, there was no data about 2025 at all. Yesterday, on Jan 2, data appeared, stating the electricity tax to be € 0,10512 per kWh. Today, this number changed to € 0,10154 without any notice of change on that website. 😐
Tabellen tarieven milieubelastingen
Bekijk de tarieven voor de verschillende milieubelastingen van 2017 tot en met 2024.www.belastingdienst.nl
Documenting #curl infrastructure. What more should I include, cover and discuss in here?
We're going to dive in with more depth on this, exploring why Bluesky's content tools are the second worst we've encountered in a long, rich history of internet censorship (just behind Meta, which are *awful).
The long and short of it is: language matters. masto.ai/@vagina_museum/113758…
Vagina Museum (@vagina_museum@masto.ai)
Attached: 1 image us: come and visit a small independent quirky museum in london bluesky moderation team: no that's pornMastodon
I'm sad that the RNIB can sell a complex bit of digital audio equipment for half the price of a purely mechanical Braille device.
[Get a bargain in our New Year sale](rnibenews.org.uk/cr/AQjI5A0Qst…)
'50 years of giving the money to the wealthy people resulted in the poor people getting no money,' is not a terribly surprising result. 🤡
"50 years of tax cuts for the rich failed to trickle down, economics study says"
cbsnews.com/news/tax-cuts-rich…

50 years of tax cuts for the rich failed to trickle down, economics study says
Tax cuts for the wealthy didn't boost the economies of the U.S. and 17 other countries — but they did worsen income inequality.Aimee Picchi (CBS News)
SQLite is a remarkable piece of software and I've always been curious about the system and the project. Here are several little known facts about SQLite.
Collection of insane and fun facts about SQLite - blag
Some of the interesting and insane facts I learned about SQLiteavi.im
cbc.ca/news/world/airlines-on-…
The world's richest man has joined a growing chorus of right-wing voices attacking Wikipedia as part of an intensifying campaign against free and open access information. Why do they hate it so much?
citationneeded.news/elon-musk-…
#Wikipedia #ElonMusk #USpolitics #USpol

Elon Musk and the right’s war on Wikipedia
The world's richest man has joined a growing chorus of right-wing voices attacking Wikipedia as part of an intensifying campaign against free and open access information.Molly White (Citation Needed)
Apple Fitness+ announces integration with Strava, new strength training program - 9to5Mac
Apple Fitness+ today announced a slew of new content to kick off the year, as well as a new integration...Benjamin Mayo (9to5Mac)
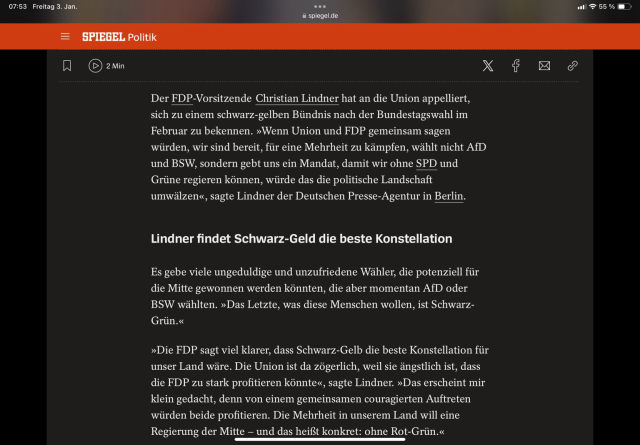
Ne das passt schon ganz gut so, die Dinge und vor allem Konstellationen beim richtigen Namen zu nennen. 😉
Schwarz-Geld im Kontext der FDP ist ziemlich auf den Punkt gebracht, meiner Meinung nach!😁
Social Democracy, an alternate history game set in the Weimar Republic. You control the SPD and fascism is on the rise.
In my playthrough, I tried to ally with the far left and built a strong leftist paramilitary force, leading to civil war against Hitler.
This game is fucking hard.
red-autumn.itch.io/social-demo…

Social Democracy: An Alternate History by Autumn Chen
You are the Social Democratic Party of Germany in 1928. Can you stop the Nazis from taking power?itch.io
Sigo insistiendo: Deberían prohibir todo tipo de estufas en la calle.
El que tenga frío que venga abrigado de casa. Ya bastante calentamos el planeta como para desperdiciar energía calentando a unos caprichosos.
Las estufas de gas se resisten a desaparecer de las terrazas de Barcelona
lavanguardia.com/local/barcelo…

Las estufas de gas se resisten a desaparecer de las terrazas de Barcelona
Muchas estufas de gas se resisten a abandonar las terrazas de Barcelona. La prohibición municipal de estos dispositivos en vigor desde el primer día del año no se nota mucho en un buen puñado de céntricas calles y plazas.Luis Benvenuty (La Vanguardia)
hi there! I’m my job I can’t use #libreoffice so I take a portable version for my personal documents because the other stole everything haha
My question is: when you release this new version I have to get a new portable #LibreOffice or just click on update?
iTerm2 logged passwords
iterm2.com/downloads/stable/iT…
If you are running iTerm2 on MacOS with ssh integration (it2ssh or Settings -> General -> Profiles, set to SSH instead of Command) you want to
- Upgrade
- Find
/tmp/framer.txton all systems you generally log into and delete it
If you manage systems with MacOS users, good luck.
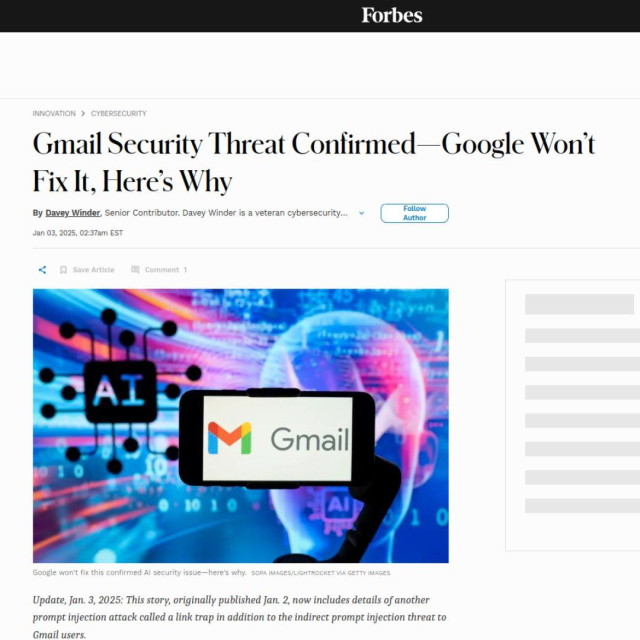
🚨 Gmail’s AI Security Risk 🚨
A @Forbes article reveals a Gmail vulnerability @Google has CONFIRMED but WON’T FIX.
Security researchers find that Gemini AI which is integrated into Gmail and other Workspace tools, is susceptible to indirect prompt injection attacks.
So why did Google issue a “Won’t Fix (Intended Behavior)” ticket?
🔗Read more forbes.com/sites/daveywinder/2…
Gmail Security Threat Confirmed—Google Won’t Fix It, Here’s Why
As Gmail AI security vulnerabilities come to the surface, why won’t Google fix the problem? Here’s what Google has to say.Davey Winder (Forbes)
Das sollte man in Bezug auf die Nutzung von kommerziellem #SocialMedia und #Kommunikation nicht unbeachtet lassen, vielleicht auch besonders in #digitaleKirche:
#Meta unterstützt #Trump Amtseinführung finanziell mit großer Summe:
bbc.com/news/articles/c8j9e1x9…
#Instagram #Facebook #WhatsApp #FediKirche

Mark Zuckerberg's Meta donates $1m to Trump fund
It appears to be the latest attempt by the Meta boss to build a closer relationship with the incoming president.Liv McMahon (BBC News)
arstechnica.com/tech-policy/20… #apple #privacy

Siri “unintentionally” recorded private convos; Apple agrees to pay $95M
Apple users may get $20 each for up to five Siri-enabled devices.Ashley Belanger (Ars Technica)
@tardis agree 100%.
to be fair I'm laughing at this payment, $90M is nothing when it comes to selling users data 😞
But there are some cool projects for smartphones that are worth the look (@GrapheneOS , @calyxinstitute , @LineageOS), and also some great alternative software to use in replacement of the apps and services of the big players.
seznamzpravy.cz/clanek/domaci-…

USA uvalily sankce na advokáta, jehož firmy sponzorovaly Zemana
Za více než polovinou darů pro Stranu práv občanů – Zemanovce byl provázaný systém firem, které z velké části ovládal švýcarský advokát Fabio Delco. Spojené státy nyní Delca zařadily na sankční seznam kvůli praní ruských peněz.Lukáš Valášek (Seznam Zprávy)
















Jakub Steiner ⭐
in reply to Jakub Steiner ⭐ • • •Should have done these as a thread long time ago. I'm new to this fediverse thing!
#procreate #sketch #gnome #flathub #flatpak #sketchfriday
Jakub Steiner ⭐
in reply to Jakub Steiner ⭐ • • •Starting a new year by almost forgetting to do a Friday sketch. New year resolution is obvious -- skip as few of these as possible!
#procreate #app #icon #sketch #gnome