Search
Items tagged with: grapheneOS
GrapheneOS version 2026012100 released
Tags:
- 2026012100 (Pixel 6, Pixel 6 Pro, Pixel 6a, Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a, Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, Pixel 9 Pro Fold, Pixel 9a, Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold, emulator, generic, other targets)
Changes since the 2026011300 release:
- fix an upstream infinite loop bug in ProtoFieldFilter.skipBytes() causing an upstream system_server issue leading to the OS being unusable in early boot for a tiny subset of users since Android 16 QPR2 (there are a bunch of reports of these symptoms with the stock Pixel OS)
- libpng: backport security patches
- remove unused INTERNET permission from Pixel Camera Services since GrapheneOS doesn't support the Pixel Connected Cameras feature
- kernel (6.1): update to latest GKI LTS branch revision including update to 6.1.161
- kernel (6.6): update to latest GKI LTS branch revision
- kernel (6.12): update to latest GKI LTS branch revision including update to 6.12.66
- Vanadium: update to version 144.0.7559.59.0
- Vanadium: update to version 144.0.7559.59.1
- Vanadium: update to version 144.0.7559.76.0
- Vanadium: update to version 144.0.7559.76.1
- Vanadium: update to version 144.0.7559.90.0
All of the Android 16 security patches from the current February 2026, March 2026, April 2026, May 2026 and June 2026 Android Security Bulletins are included in the 2026012101 security preview release. List of additional fixed CVEs:
- Critical: CVE-2026-0039, CVE-2026-0040, CVE-2026-0041, CVE-2026-0042, CVE-2026-0043, CVE-2026-0044
- High: CVE-2025-22424, CVE-2025-22426, CVE-2025-32348, CVE-2025-48561, CVE-2025-48615, CVE-2025-48617, CVE-2025-48630, CVE-2025-48641, CVE-2025-48642, CVE-2025-48644, CVE-2025-48645, CVE-2025-48646, CVE-2025-48649, CVE-2025-48652, CVE-2025-48653, CVE-2025-48654, CVE-2026-0011, CVE-2026-0014, CVE-2026-0015, CVE-2026-0016, CVE-2026-0017, CVE-2026-0018, CVE-2026-0020, CVE-2026-0021, CVE-2026-0022, CVE-2026-0023, CVE-2026-0024, CVE-2026-0025, CVE-2026-0033, CVE-2026-0034, CVE-2026-0036
- Unclassified: CVE-2026-0035
For detailed information on security preview releases, see our post about it.
GrapheneOS security preview releases - GrapheneOS Discussion Forum
GrapheneOS discussion forumGrapheneOS Discussion Forum
Vanadium version 144.0.7559.90.0 released
Changes in version 144.0.7559.90.0:
- update to Chromium 144.0.7559.90
- extend upstream motion sensors toggle with a per-site toggle (Vanadium already had the global toggle disabled by default)
- disable autofill server support (already disabled by Vanadium Config 148)
- extend support for supplementary language/regional content filters to a larger set (Arabic, Bulgarian, Spanish, French, German, Hebrew, Indian, Indonesian, Italian, Korean, Lithuanian, Latvian, Dutch, Nordic, Polish, Portuguese, Romanian, Russian, Vietnamese and Chinese)
A full list of changes from the previous release (version 144.0.7559.76.1) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.
Comparing 144.0.7559.76.1...144.0.7559.90.0 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
Vanadium version 144.0.7559.76.1 released
Changes in version 144.0.7559.76.1:
- extend support for language-specific content filters from German to cover additional languages supporting by the other EasyList variants (Bulgarian, Hebrew, Indonesian, Dutch, Vietnamese, Chinese) which can be expanded further to more EasyList-affiliated lists in the near future
- add workaround for upstream regression for the HTTPS-only mode user interface on Android which can be replaced by a backport of their fix in the near future
A full list of changes from the previous release (version 144.0.7559.76.0) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.
Comparing 144.0.7559.76.0...144.0.7559.76.1 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
Vanadium version 144.0.7559.76.0 released
Changes in version 144.0.7559.76.0:
- update to Chromium 144.0.7559.76
- always reduce WebView user agent
A full list of changes from the previous release (version 144.0.7559.76.0) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.
Comparing 144.0.7559.59.1...144.0.7559.76.0 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
GrapheneOS version 2026011300 released
Tags:
- 2026011300 (Pixel 6, Pixel 6 Pro, Pixel 6a, Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a, Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, Pixel 9 Pro Fold, Pixel 9a, Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold, emulator, generic, other targets)
Changes since the 2026011000 release:
- update to January 2026 Pixel driver/firmware code for the subset of devices with a January 2026 release
- allow user to set any account as the default contacts account (since Android 16 QPR1, this was restricted to Google accounts for the stock Pixel OS and nothing permitted at all for AOSP)
- kernel (6.1): update to latest GKI LTS branch revision including update to 6.1.159
- kernel (6.6): update to latest GKI LTS branch revision
- kernel (6.12): update to latest GKI LTS branch revision
All of the Android 16 security patches from the current January 2026, February 2026, March 2026, April 2026, May 2026 and June 2026 Android Security Bulletins are included in the 2026011301 security preview release. List of additional fixed CVEs:
- High: CVE-2025-32348, CVE-2025-48561, CVE-2025-48615, CVE-2025-48617, CVE-2025-48630, CVE-2025-48641, CVE-2025-48642, CVE-2025-48644, CVE-2025-48645, CVE-2025-48646, CVE-2025-48649, CVE-2025-48652, CVE-2025-48653, CVE-2025-48654, CVE-2026-0014, CVE-2026-0015, CVE-2026-0016, CVE-2026-0017, CVE-2026-0018, CVE-2026-0020, CVE-2026-0021, CVE-2026-0022, CVE-2026-0023, CVE-2026-0024, CVE-2026-0025, CVE-2026-0033, CVE-2026-0034, CVE-2026-0035, CVE-2026-0036
For detailed information on security preview releases, see our post about it.
GrapheneOS security preview releases - GrapheneOS Discussion Forum
GrapheneOS discussion forumGrapheneOS Discussion Forum
Vanadium version 144.0.7559.59.1 released
Changes in version 144.0.7559.59.1:
- restore disabling special search engine user interface specific to Google search
- backport fix for DrumBrake WebAssembly compatibility issues
A full list of changes from the previous release (version 144.0.7559.59.0) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.
Comparing 144.0.7559.59.0...144.0.7559.59.1 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
GrapheneOS version 2026011000 released
Tags:
- 2026011000 (Pixel 6, Pixel 6 Pro, Pixel 6a, Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a, Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, Pixel 9 Pro Fold, Pixel 9a, Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold, emulator, generic, other targets)
Changes since the 2026010800 release:
- reimplement the standard Android USB data signal API with our hardware + software USB blocking functionality to preserve support for the device admin and lockdown mode features for fully toggling off USB while upgrading it to use hardware blocking (this was omitted in the previous Alpha-only release)
- fix regression in the last release causing sandboxed Google Play breakage in a subset of secondary users caused by the phenotype flag changes in the previous release
- Sandboxed Google Play compatibility layer: add stub for ContentResolver.acquireUnstableProvider()
- fix the Terminal virtual machine management app not working in a secondary user Private Space (GrapheneOS adds the ability to use the Terminal app in secondary users and also adds the ability to use Private Space in secondary users, so the combination of those things resulted in this being possible but the upstream code was incompatible with it)
- Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold: add high EMF (PWM) mode opt-in to the Settings app
All of the Android 16 security patches from the current January 2026, February 2026, March 2026, April 2026, May 2026 and June 2026 Android Security Bulletins are included in the 2026011001 security preview release. List of additional fixed CVEs:
- High: CVE-2025-32348, CVE-2025-48561, CVE-2025-48615, CVE-2025-48617, CVE-2025-48630, CVE-2025-48641, CVE-2025-48642, CVE-2025-48644, CVE-2025-48645, CVE-2025-48646, CVE-2025-48649, CVE-2025-48652, CVE-2025-48653, CVE-2025-48654, CVE-2026-0014, CVE-2026-0015, CVE-2026-0016, CVE-2026-0017, CVE-2026-0018, CVE-2026-0020, CVE-2026-0021, CVE-2026-0022, CVE-2026-0023, CVE-2026-0024, CVE-2026-0025, CVE-2026-0033, CVE-2026-0034, CVE-2026-0035
For detailed information on security preview releases, see our post about it.
GrapheneOS security preview releases - GrapheneOS Discussion Forum
GrapheneOS discussion forumGrapheneOS Discussion Forum
Das letzte mal als ich versucht habe #NINA auf #GrapheneOS ohne Google Play Services zum Laufen zu bringen, habe ich es leider nicht hinbekommen (ist aber schon ein paar Jahre her). Wenn jemand passend zum #did #dut nach Alternativen sucht: #fosswarn
Mit FOSSwarn bekommt ihr offizielle Warnmeldungen für eure Orte direkt aufs Handy. Push-Benachrichtigungen funktionieren ebenfalls zuverlässig über UnifiedPush, ich nutze dazu die App #Sunup
GrapheneOS version 2026010800 released
Tags:
- 2026010800 (Pixel 6, Pixel 6 Pro, Pixel 6a, Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a, Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, Pixel 9 Pro Fold, Pixel 9a, Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold, emulator, generic, other targets)
Changes since the 2025122500 release:
- raise declared patch level to 2026-01-05 which has been provided since we moved to Android 16 QPR2 in December due to Pixels shipping CVE-2025-54957 in December
- re-enable the system keyboard at boot if it's disabled
- switch to the system keyboard when device boots to the Safe Mode
- add "Reboot to Safe Mode" power menu button in Before First Unlock state to make Safe Mode much more discoverable for working around app issues such as a broken third party keyboard
- add workaround for upstream UsageStatsDatabase OOM system_server crash
- add workaround for upstream WindowContext.finalize() system_server crash
- disable buggy upstream disable_frozen_process_wakelocks feature causing system_server crashes for some users
- Sandboxed Google Play compatibility layer: fix phenotype flags not working in Play services clients
- Sandboxed Google Play compatibility layer: add MEDIA_CONTENT_CONTROL as a requested permission for Android Auto as part of our toggles for it to avoid needing to grant the far more invasive notification access permission
- Sandboxed Google Play compatibility layer: extend opt-in Android Auto Bluetooth support to allow A2dpService.setConnectionPolicy() to fix Bluetooth functionality (previously worked around with a GmsCompatConfig update avoiding a crash)
- switch to new upstream PackageInstallerUI implementation added in Android 16 QPR2 and port our changes to it
- update SQLite to 3.50.6 LTS release
- add an extra layer of USB port protection on 10th gen Pixels based on upstream functionality to replace our USB gadget control which was causing compatibility issues with the Pixel 10 USB drivers
- allow SystemUI to access NFC service on 10th gen Pixels to fix the NFC quick tile
- disable the upstream Android USB data protection feature since it conflicts with our more advanced approach and causes issues
- issue CHARGING_ONLY_IMMEDIATE port control command in more cases
- fix an issue in our infrastructure for spoofing permission self-checks breaking automatically reading SMS one-time codes for certain apps
- add workaround for upstream KeySetManagerService system_server crash causing a user to be stuck on an old OS version due to it causing a boot failure when booting a the new OS version after updating
- wipe DPM partition on 10th gen Pixels as part of installation as we do on earlier Pixels since it's always meant to be zeroed on production devices
- Settings: disable indexing of the unsupported "Parental controls" setting which is not currently available in AOSP
- Settings: disable redundant indexing of widgets on lockscreen contents which is already indexed another way
- skip all pseudo kernel crash reports caused by device reboot to avoid various false positive crash reports
- Vanadium: update to version 143.0.7499.192.0
All of the Android 16 security patches from the current January 2026, February 2026, March 2026, April 2026, May 2026 and June 2026 Android Security Bulletins are included in the 2026010801 security preview release. List of additional fixed CVEs:
- High: CVE-2025-32348, CVE-2025-48561, CVE-2025-48615, CVE-2025-48630, CVE-2025-48641, CVE-2025-48642, CVE-2025-48644, CVE-2025-48645, CVE-2025-48646, CVE-2025-48649, CVE-2025-48652, CVE-2025-48653, CVE-2026-0014, CVE-2026-0015, CVE-2026-0016, CVE-2026-0017, CVE-2026-0018, CVE-2026-0020, CVE-2026-0021, CVE-2026-0022, CVE-2026-0023, CVE-2026-0024, CVE-2026-0025
For detailed information on security preview releases, see our post about it.
GrapheneOS releases
Official releases of GrapheneOS, a security and privacy focused mobile OS with Android app compatibility.GrapheneOS
Vanadium version 144.0.7559.59.0 released
Changes in version 144.0.7559.59.0:
- update to Chromium 144.0.7559.59
A full list of changes from the previous release (version 143.0.7499.192.0) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.

Comparing 143.0.7499.192.0...144.0.7559.59.0 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
Vanadium version 143.0.7499.192.0 released
Changes in version 143.0.7499.192.0:
- update to Chromium 143.0.7499.192
- fix obscure crashes from removing Google service related settings identified by the Chromium test suite (not happening for users in practice)
A full list of changes from the previous release (version 143.0.7499.146.0) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.

Comparing 143.0.7499.146.0...143.0.7499.192.0 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
@andree4live @oneloop additionally, every website you visit you should check if it's hosted in the Google Cloud because that would mean it's not Google Free either.
So the question is, what is the definition of Google Free? For me, it is by default no connections to any Google server, no usage of any Google app, etc. And the control is fully with the user.
And with this definition, as far as I know, there is only #grapheneOS.
Others seem to connect at least to the captive portal or supl or connectivity checks to google server
Tempest Server Sponsorship Discontinued
We currently have sponsored update mirrors in Toronto (Xenyth), Miami (ReliableSite) and Los Angeles (ReliableSite). Each of these are 10Gbps servers we manage ourselves. Tempest's new ownership is withdrawing the sponsorship for the one in London which was already not enough.
Our overall traffic for updates peaks around 40Gbps for the largest releases for quarterly and yearly Android releases. Average usage over a month is below 2Gbps. We shipped Android 16 QPR2 after it was released earlier this month so the next major update will be in March 2026.
We could easily afford to start paying for the Tempest server in London but it lacks IPv6 and has issues with network downtime. We also aren't interested in paying a company sending us an ultimatum in the holiday season where we have 6 days to start paying or it's taken down.
For now, we can update our GeoDNS configuration to split Europe between Toronto and Miami combined with using Los Angeles for the rest of Asia. We can afford to pay for update servers in Europe ourselves if needed but sponsors are nice for this to avoid overpaying for bandwidth.
We already planned to start paying for at least 2 powerful dedicated servers to provide our own geocoding service instead of only a proxy (nominatim.org/release-docs/lat…). For updates, a lot of providers charge for 10Gbps bandwidth as if it's used at 100% capacity continuously or just overcharge.
GrapheneOS (@GrapheneOS@grapheneos.social)
We already planned to start paying for at least 2 powerful dedicated servers to provide our own geocoding service instead of only a proxy (https://nominatim.org/release-docs/latest/admin/Installation/#hardware).GrapheneOS (GrapheneOS Mastodon)
GrapheneOS version 2025122500 released
Tags:
- 2025122500 (Pixel 6, Pixel 6 Pro, Pixel 6a, Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a, Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, Pixel 9 Pro Fold, Pixel 9a, Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold, emulator, generic, other targets)
Changes since the 2025121700 release:
- restore support for bypassing carriers disallowing choosing the cellular network mode (this was lost in a recent major version migration such as the port to Android 16 QPR1 but we aren't sure exactly when it regressed)
- remove poorly designed upstream end session button on the lockscreen (it remains available in the power menu)
- enable feature flag for new upstream end session button in the user switcher
- switch to vendor files from 2nd December 2025 release (BP4A.251205.006.E1) for devices with it available
- enable lockscreen widget support
- fix upstream system_server crash in NotificationHistoryProtoHelper
- Wi-Fi HAL: ignore debug logging requests on all Pixels with MTE support to avoid a crash from detecting an invalid memory access in the upstream code
- Sandboxed Google Play compatibility layer: add support for redirecting Google Play location service requests from within Google Play services itself which means the GrapheneOS provided network location will work for internal Play services features such as Google Maps location sharing when redirecting to the OS is enabled (which is the default) and the Location permission is granted to it
- Sandboxed Google Play compatibility layer: force redirecting Google Play location service requests from within Google Play services and Android Auto when the Location permission is disabled for better error handling (neither properly handles the Location permission not being granted since it's always granted on any Google Mobile Services OS in practice instead of being explicitly opt-in)
- Sandboxed Google Play compatibility layer: fix a compatibility issue with the Chromium test suite
- Network Location: improve position estability accuracy and stability
- Network Location: prevent potential division by zero exception
- Network Location: improve experimental Wi-Fi RTT support which is still disabled in production
- kernel (6.1): update to latest GKI LTS branch revision
- kernel (6.6): update to latest GKI LTS branch revision including update to 6.6.119
- kernel (6.6): disable CONFIG_TLS to reduce attack surface
- kernel (6.12): update to latest GKI LTS branch revision including update to 6.12.63
- kernel (6.12): disable CONFIG_TLS to reduce attack surface
- include configuration for thermometer on 10th gen Pixels
- adevtool: auto-detect filesystem image type (ext4 vs. EROFS)
- adevtool: add support for canary builds
- adevtool: improve performance
- remove obsolete workaround for using a prebuilt recovery extension
All of the Android 16 security patches from the current January 2026, February 2026, March 2026, April 2026, May 2026 and June 2026 Android Security Bulletins are included in the 2025121701 security preview release. List of additional fixed CVEs:
- High: CVE-2025-32348, CVE-2025-48561, CVE-2025-48630, CVE-2025-48641, CVE-2025-48642, CVE-2025-48644, CVE-2025-48645, CVE-2025-48646, CVE-2025-48649, CVE-2025-48652, CVE-2025-48653, CVE-2026-0014, CVE-2026-0015, CVE-2026-0016, CVE-2026-0017, CVE-2026-0018, CVE-2026-0020, CVE-2026-0021, CVE-2026-0022, CVE-2026-0023, CVE-2026-0024, CVE-2026-0025
2025121701 provides at least the full 2026-01-01 Android and Pixel security patch level but will remain marked as providing 2025-12-05.
For detailed information on security preview releases, see our post about it.
GrapheneOS security preview releases - GrapheneOS Discussion Forum
GrapheneOS discussion forumGrapheneOS Discussion Forum
GrapheneOS version 2025121700 released
Tags:
- 2025121700 (Pixel 6, Pixel 6 Pro, Pixel 6a, Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a, Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, Pixel 9 Pro Fold, Pixel 9a, Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold, emulator, generic, other targets)
Changes since the 2025121200 release:
- add workaround for upstream system_server WallpaperManagerService.hasPermission() crash
- fix upstream system_server crash in NotificationHistory.getPooledStringsToWrite()
- Launcher: add a workaround for upstream QuickstepModelDelegate.getContainer() crash
- set initial port security state at an earlier boot stage to improve debugging on production builds where the port state has been changed from the default "Charging-only when locked" to "Charging-only when locked, except before first unlock" or "On"
- use default desktop mode configuration since our changes are no longer needed to enable features and caused crashes for at least 1 user which were addressed with an out-of-band release prior to this one
- kernel (6.1): update to latest GKI LTS branch revision
- kernel (6.1): add back recent dma-buf changes now that an upstream use-after-free bug is resolved
- kernel (6.6): update to latest GKI LTS branch revision including update to 6.6.118
- adevtool: update carrier settings
- Vanadium: update to version 143.0.7499.146.0
All of the Android 16 security patches from the current January 2026, February 2026, March 2026, April 2026, May 2026 and June 2026 Android Security Bulletins are included in the 2025121701 security preview release. List of additional fixed CVEs:
- High: CVE-2025-32348, CVE-2025-48641, CVE-2026-0014, CVE-2026-0015, CVE-2026-0016, CVE-2026-0017, CVE-2026-0018
2025121701 provides at least the full 2026-01-01 Android and Pixel security patch level but will remain marked as providing 2025-12-05.
For detailed information on security preview releases, see our post about it.
GrapheneOS security preview releases - GrapheneOS Discussion Forum
GrapheneOS discussion forumGrapheneOS Discussion Forum
Vanadium version 143.0.7499.146.0 released
Changes in version 143.0.7499.146.0:
- update to Chromium 143.0.7499.146
A full list of changes from the previous release (version 143.0.7499.109.0) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.
Comparing 143.0.7499.109.0...143.0.7499.146.0 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
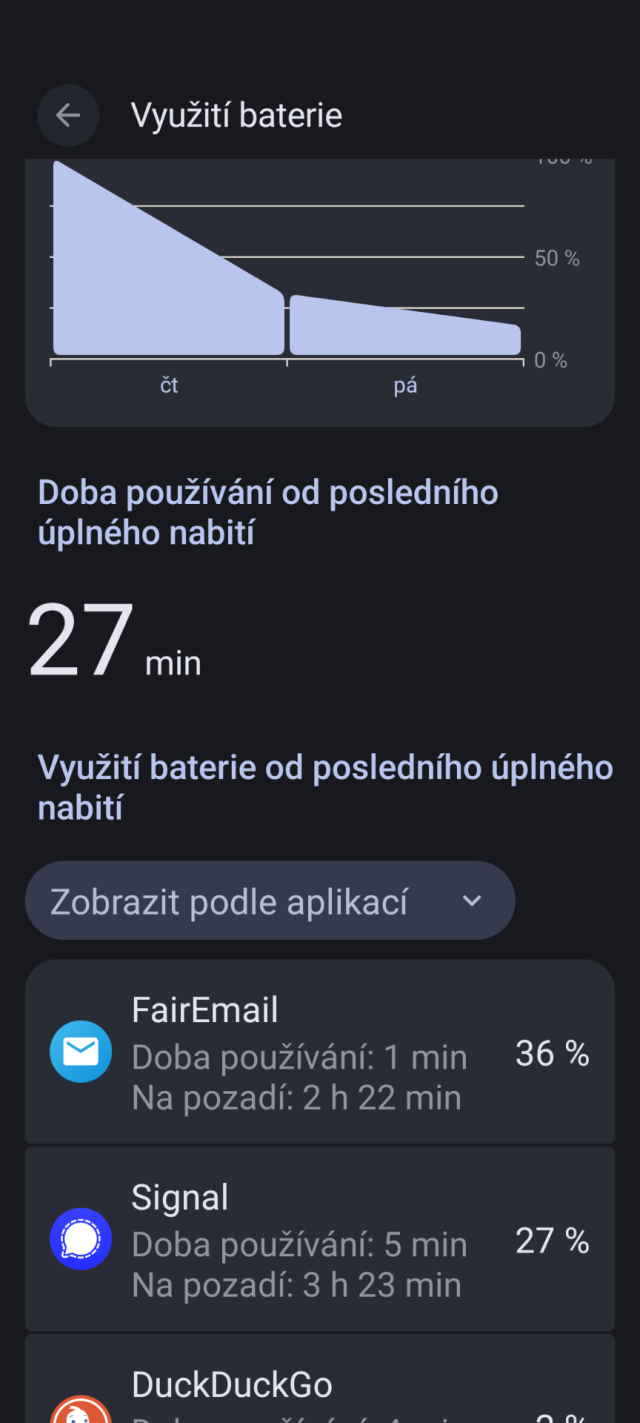
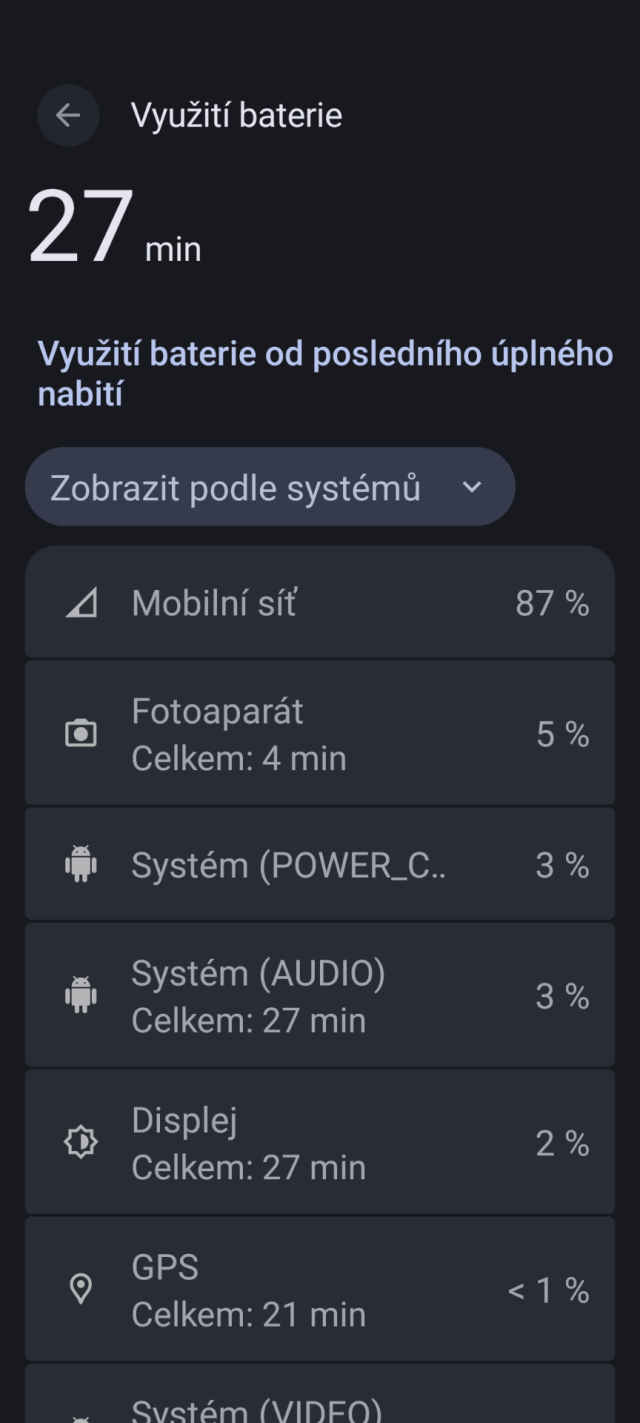
#grapheneos jsem trochu rozpacitej z vydrze (Pixel 8a). Jak to mate vy? Nejake tipy?
O den driv to bylo neco pres hodinu.
Díky @mahdi jsem synchronizoval kontakty a kalendáře. A díky tipům dalších jsem vybral základní aplikace.
Teď začnu používat, a případně zkoušet varianty.
#oscloud a @archos si nechám až po ukončení této fáze.
Na starém mobilu jsem si zvykl na jednoduchý spoštěč - Olauncher. Na F-droidu pár (podle popisu) podobných je. Máte někdo zkušenost s některým podobným, který byste mi doporučili?
Zatím jsem narazil na jediný problém...firemní profil. Vytvořil jsem si profil, v něm nainstaloval google a Intune Company Portal. V něm se přihlásím na svůj firemní účet, ale nedaří se vytvořit firemní prostor (proces havaruje), takže tam nedostanu firemní aplikace (outlook, teams..). Doufám, že je to jen nějakým nastavením. Poradí někdo.
Předem děkuji 🙏
GrapheneOS version 2025121200 released
Tags:
- 2025121200 (Pixel 6, Pixel 6 Pro, Pixel 6a, Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a, Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, Pixel 9 Pro Fold, Pixel 9a, Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold, emulator, generic, other targets)
Changes since the 2025121000 release:
- disable notification summaries and organizer features due to AOSP and GrapheneOS lacking the AI models used to implement these features
- add workaround for notification background appearance regression in Android 16 QPR2
- Vanadium: update to version 143.0.7499.109.0
- GmsCompatConfig: update to version 167
All of the Android 16 security patches from the current January 2026, February 2026, March 2026, April 2026, May 2026 and June 2026 Android Security Bulletins are included in the 2025121201 security preview release. List of additional fixed CVEs:
- High: CVE-2025-32348, CVE-2025-48641, CVE-2026-0014, CVE-2026-0015, CVE-2026-0016, CVE-2026-0017, CVE-2026-0018
2025121201 provides at least the full 2026-01-01 Android and Pixel security patch level but will remain marked as providing 2025-12-05.
For detailed information on security preview releases, see our post about it.
GrapheneOS security preview releases - GrapheneOS Discussion Forum
GrapheneOS discussion forumGrapheneOS Discussion Forum
Second New IPv4 /24 Subnet Received
We've received a 2nd IPv4 /24 subnet from ARIN for our 2nd anycast DNS network. Both our /24 subnets were obtained quickly under the NRPM 4.10 policy for IPv6 deployment for our dual stack DNS use case. 2nd was obtained without waiting 6 months due to being a discrete network.
We host our own authoritative DNS servers to provide DNS resolution for our services. Authoritative DNS are the servers queried by DNS resolvers run by your ISP, VPN or an explicitly user chosen one such as Cloudflare or Quad9 DNS. We now have our own AS and IP space for this.
Our ns1 has 11 locations on Vultr: New York City, Miami, Los Angeles, Seattle, London, Frankfurt, Singapore, Mumbai, Tokyo, Sao Paulo and Sydney.
Our ns2 has 4 locations on BuyVM: New York City, Miami, Las Vegas and Bern. We'll be adding a 2nd server provider for more locations.
DNS resolvers quickly fall back to the other network if traffic is dropped. Having two discrete networks with separate hosting companies and transit providers provides very high reliability. Individual servers which go down also stop having traffic routed to them due to BGP.
We have tiny website/network servers and also powerful update mirrors around the world. Our DNS servers use a combination of a GeoIP database and their own location to route users to the closest server that's up. Frequent health checks and low expiry time handle server downtime.
GmsCompatConfig version 167 released
Changes in version 167:
- add stub for BluetoothA2dp.setConnectionPolicy() to fix a crash with a new version of Android Auto
A full list of changes from the previous release (version 166) is available through the Git commit log between the releases (only changes to the gmscompat_config text file and config-holder/ directory are part of GmsCompatConfig).
GmsCompatConfig is the text-based configuration for the GrapheneOS sandboxed Google Play compatibility layer. It provides a large portion of the compatibility shims.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release.
Comparing config-166...config-167 · GrapheneOS/platform_packages_apps_GmsCompat
Contribute to GrapheneOS/platform_packages_apps_GmsCompat development by creating an account on GitHub.GitHub
Vanadium version 143.0.7499.109.0 released
Changes in version 143.0.7499.109.0:
- update to Chromium 143.0.7499.109
A full list of changes from the previous release (version 143.0.7499.52.0) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.
Comparing 143.0.7499.52.0...143.0.7499.109.0 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
GrapheneOS Foundation Responds To Jolla
Jolla has spent years disparaging projects based on the Android Open Source Project (AOSP) for marketing. SailfishOS has a largely closed source user interface and application layer with no equivalent to the open source AOSP. It's far less private and secure than AOSP or iOS too.
Jolla recently launched a new product so their supporters are understandably trying to promote it. As part of that, they've been posting about it in replies to posts about GrapheneOS. We've replied to some of it with our perspective within threads originally about GrapheneOS.
Since we dared to post accurate information in threads about GrapheneOS where they mentioned us in replies to promote it, their forum is being used as a place to attack GrapheneOS including libelous attacks towards our team referencing harassment content:
forum.sailfishos.org/t/sailfis…
Several of their supporters are taking the usual approach of calling us crazy and delusional while referencing harassment content at the same time as calling the factual info we posted aggressive. They're brigading discussions about GrapheneOS with attacks so we made this thread.
Brigading threads about an open source project and attacking the team with libelous claims is toxic. Defending ourselves from it with factual statements is not toxic. Repeating dishonest attacks on our team based on similar attacks over and over doesn't make it any less untrue.

Sailfish OS: Clarifying claims about open/closed source, security and privacy
Actually Jolla say that “Sailfish OS is partially open source, but not fully open source in the sense of “every part of the OS is free/open-source.Sailfish OS Forum
GrapheneOS version 2025121000 released
This is our first non-experimental release based on Android 16 QPR2 after our initial experimental 2025120800 release.
The change to the style of notification backgrounds is an upstream regression rather than an intentional change to a more minimal style. It will be fixed in a subsequent release since we decided it isn't important enough to delay this.
Tags:
- 2025121000 (Pixel 6, Pixel 6 Pro, Pixel 6a, Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a, Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, Pixel 9 Pro Fold, Pixel 9a, Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold, emulator, generic, other targets)
Changes since the 2025120400 release:
- full 2025-12-05 security patch level
- rebased onto BP4A.251205.006 Android Open Source Project release (Android 16 QPR2)
- disable promotion of identity check feature not currently present in GrapheneOS due to depending on privileged Google Mobile Services integration
- GmsCompatConfig: update to version 166
All of the Android 16 security patches from the current January 2026, February 2026, March 2026, April 2026, May 2026 and June 2026 Android Security Bulletins are included in the 2025121001 security preview release. List of additional fixed CVEs:
- High: CVE-2025-32348, CVE-2025-48641, CVE-2026-0014, CVE-2026-0015, CVE-2026-0016, CVE-2026-0017, CVE-2026-0018
2025121001 provides at least the full 2026-01-01 Android and Pixel security patch level but will remain marked as providing 2025-12-05.
For detailed information on security preview releases, see our post about it.
GrapheneOS security preview releases - GrapheneOS Discussion Forum
GrapheneOS discussion forumGrapheneOS Discussion Forum
Experimental GrapheneOS Release Based On AOSP 16 QPR2 Now Available For Testing
GrapheneOS (@GrapheneOS@grapheneos.social)
An experimental release of GrapheneOS (2025120800) based on Android 16 QPR2 is available for testing via sideloading. It won't be pushed out via Alpha. You can join our testing chat room if you want to help with testing (https://grapheneos.GrapheneOS (GrapheneOS Mastodon)
GrapheneOS Based On AOSP 16 QPR2 Releasing Soon
Android 16 QPR2 experimental releases will be available soon. We're dealing with a lot of attacks on the project branching off from the smear campaign in France. We'd appreciate if our community would debunk this nonsense across platforms for us so we can focus on QPR2. Thanks.
If you see the fake story about someone claiming to be charged with premeditated murder because GrapheneOS supposedly didn't protect their data, see nitter.net/GrapheneOS/status/1… for a thorough debunking. Their story keeps changing and clearly isn't real. They may be a career criminal but this is fake.
GrapheneOS (@GrapheneOS@grapheneos.social)
If you see the fake story about someone claiming to be charged with premeditated murder because GrapheneOS supposedly didn't protect their data, see https://nitter.net/GrapheneOS/status/1997126386968903972 for a thorough debunking.GrapheneOS (GrapheneOS Mastodon)
@archos super, díky.
Pomalu se degooglizuji, jak se zabydlím na #grapheneos , chtěl bych postoupit dál. Mrknu pak na #Nextcloud ... a nejspíš se ještě ozvu 🙂
@neil
I'm on #GrapheneOS without MicroG or anything Google at all, so I use UnifiedPush to get notifications from #Fedilab, #Element and #ElementX (and something else I've forgotten LOL).
I set up family members with Element using UnifiedPush as, although they have Play Services, I prefer not to give Google (or by extension Trump atm) metadata about who my family talks to and when.
I only wish @nextcloud , @PixelFed , @loops etc. would get on board!
GmsCompatConfig version 166 released
Changes in version 166:
- add initial stubs for Android 16 QPR2
A full list of changes from the previous release (version 165) is available through the Git commit log between the releases (only changes to the gmscompat_config text file and config-holder/ directory are part of GmsCompatConfig).
GmsCompatConfig is the text-based configuration for the GrapheneOS sandboxed Google Play compatibility layer. It provides a large portion of the compatibility shims.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release.
Comparing config-165...config-166 · GrapheneOS/platform_packages_apps_GmsCompat
Contribute to GrapheneOS/platform_packages_apps_GmsCompat development by creating an account on GitHub.GitHub
Be careful, if the product is too secure, the user may be a criminal. This is how some parts of the EU think about security and data protection.
🛡️ Level: Paranoia+
📱 Hlavní profil: jen FOSS aplikace. Čistota, minimalismus.
🛠️ Pracovní profil: WhatsApp, navigace, sportovní apky — prostě věci, které by mi hlavní profil zbytečně „zašpinily“.
💰 Bankovní profil: jen banky. Jo, mám na to celý profil. Ano, je to přesně tak extrémní, jak to zní.
A teď jen čekám, jak dlouho tohle digitální odříkání vydržím, než mě něco donutí založit čtvrtý profil… nebo to prostě prdnu všechno zpátky na hlavní. 🤣
#grapheneos
GrapheneOS version 2025120400 released
Tags:
- 2025120400 (Pixel 6, Pixel 6 Pro, Pixel 6a, Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a, Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, Pixel 9 Pro Fold, Pixel 9a, Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL, Pixel 10 Pro Fold, emulator, generic, other targets)
Changes since the 2025111800 release:
- full 2025-12-01 security patch level (has already been fully provided by our security preview releases for at least a month and most of the patches since September)
- add experimental support for the Pixel 10, Pixel 10 Pro, Pixel 10 Pro XL and Pixel 10 Pro Fold (there were 2 standalone experimental releases prior to this via 2025112500 and 2025113000 along with corresponding security preview releases for each)
- Cell Broadcast Receiver: switch back to our modified text for the presidential alerts toggle
- kernel (6.1): update to latest GKI LTS branch revision including update to 6.1.158
- kernel (6.6): update to latest GKI LTS branch revision including update to 6.6.116
- kernel (6.12): update to latest GKI LTS branch revision including update to 6.12.60
- Auditor: update to version 90
- Vanadium: update to version 143.0.7499.34.0
- Vanadium: update to version 143.0.7499.34.1
- Vanadium: update to version 143.0.7499.34.2
- GmsCompatConfig: update to version 164
- GmsCompatConfig: update to version 165
All of the Android 16 security patches from the current January 2026, February 2026 and March 2026 Android Security Bulletins are included in the 2025120401 security preview release. List of additional fixed CVEs:
- Critical: CVE-2025-48631, CVE-2026-0006
- High: CVE-2022-25836, CVE-2022-25837, CVE-2023-40130, CVE-2025-22420, CVE-2025-22432, CVE-2025-26447, CVE-2025-32319, CVE-2025-32348, CVE-2025-48525, CVE-2025-48536, CVE-2025-48555, CVE-2025-48564, CVE-2025-48565, CVE-2025-48566, CVE-2025-48567, CVE-2025-48572, CVE-2025-48573, CVE-2025-48574, CVE-2025-48575, CVE-2025-48576, CVE-2025-48577, CVE-2025-48578, CVE-2025-48579, CVE-2025-48580, CVE-2025-48582, CVE-2025-48583, CVE-2025-48584, CVE-2025-48585, CVE-2025-48586, CVE-2025-48587, CVE-2025-48589, CVE-2025-48590, CVE-2025-48592, CVE-2025-48594, CVE-2025-48596, CVE-2025-48597, CVE-2025-48598, CVE-2025-48600, CVE-2025-48601, CVE-2025-48602, CVE-2025-48603, CVE-2025-48604, CVE-2025-48605, CVE-2025-48609, CVE-2025-48612, CVE-2025-48614, CVE-2025-48615, CVE-2025-48616, CVE-2025-48617, CVE-2025-48618, CVE-2025-48619, CVE-2025-48620, CVE-2025-48621, CVE-2025-48622, CVE-2025-48626, CVE-2025-48628, CVE-2025-48629, CVE-2025-48630, CVE-2025-48632, CVE-2025-48633, CVE-2025-48634, CVE-2026-0005, CVE-2026-0007, CVE-2026-0008
For detailed information on security preview releases, see our post about it.
GrapheneOS security preview releases - GrapheneOS Discussion Forum
GrapheneOS discussion forumGrapheneOS Discussion Forum
Vanadium version 143.0.7499.52.0 released
Changes in version 143.0.7499.52.0:
- update to Chromium 143.0.7499.52
A full list of changes from the previous release (version 143.0.7499.34.2) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.
Comparing 143.0.7499.34.2...143.0.7499.52.0 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
Vanadium version 143.0.7499.34.2 released
Changes in version 143.0.7499.34.2:
- avoid always open external links in Incognito mode causing bookmarks to always open in it
- enable autofill configuration screens regardless of autofill settings
- remove unused Google autofill status
- enable Drumbrake WebAssembly interpreter for x86_64 builds used in the emulator too
A full list of changes from the previous release (version 143.0.7499.34.1) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.

Comparing 143.0.7499.34.1...143.0.7499.34.2 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub
Přechod mezi telefony je na Androidu pořád hodně práce
Konečně je GrapheneOS dostupný také pro Pixel 10 a já na něj mohl konečně přejít. Jak jednoduchá byla migrace na nový telefon? GrapheneOS má nejpokročilejší zálohovací/migrační nástroj, jaký jsem na Androidu zkoušel, jak ale píšu v článku, i tak je to pořád z nemalé části manuální proces.
#android #grapheneos #pixel10pro #seedvault
blog.eischmann.cz/2025/12/02/p…
(reakce na tento příspěvek se může zobrazit jako komentář pod článkem)
Přechod mezi telefony je na Androidu pořád hodně práce
Konečně je GrapheneOS dostupný také pro Pixel 10 a já na něj mohl konečně přejít. Jak jednoduchá byla migrace na nový telefon? GrapheneOS má nejpokročilejší zálohovací/migrační nástroj, jaký jsem na Androidu zkoušel, jak ale píšu v článku, i tak je t…Sesivany's blog
GrapheneOS Foundation Suggests Improvements For Early Security Patch Previews
Our security preview releases have provided the December 2025 security patches for the Android Open Source Project since September 2025. December 2025 security patches are now public and being integrated into our regular releases while our security previews have up to March 2026.
A bunch of the patches previously scheduled for December 2025 were made optional and deferred to future months so they're not listed in the public bulletin. That's why even our September 2025 security preview releases list CVEs which are still not public in December 2025.
The reason patches get deferred is because OEMs aren't capable of quickly integrating, testing and shipping patches. When issues are identified including an OEM having trouble with it, they'll often defer it to a future month. Our security previews can continue shipping these.
GrapheneOS is the only Android-based OS providing the full security preview patches. Samsung ships a small subset of their flagship devices. Pixel stock OS gets a portion of it early but we aren't sure exactly how much since they don't follow their guidelines for listing patches.
Providing our security preview patches is a lot of work for us. It requires a full time developer spending a significant fraction of their time on it. It's hard to understand why large companies can't keep up with these patches but what matters is that we can provide them early.
Android security preview patches are currently backports to Android 13, 14, 15 and 16. Since GrapheneOS is based on Android 16 QPR1, we need to forward port the patches from 16 to 16 QPR1. Our understanding is they're going to start backporting to some quarterly releases too.
Android 16 QPR2 appears to be the first quarterly release of Android which is going to be shipped by non-Pixel devices. If that's the case, they'll need to start providing security preview patches backported to it too. It's not clear if it will happen for every quarterly release.
Spending a significant amount of time on this is part of the reason GrapheneOS feature development has slowed down. Expanding our servers and now migrating away from OVH is another. We'll be hiring more people and improving our organization structure to get things moving better.
We would greatly prefer it if patches were disclosed to OEMs 1 week ahead instead of 2-4 months ahead so our security preview releases would only need to exist for a week and regular releases would get the patches much faster. OEMs should just hire far more people and do better.
An Article About GrapheneOS Foundation Leaving France

GrapheneOS bails on OVHcloud over France's privacy stance
: Project cites fears of state access as cloud sovereignty row deepensRichard Speed (The Register)
Vanadium version 143.0.7499.34.1 released
Changes in version 143.0.7499.34.1:
- fix regression for setting opening external links in Incognito mode
- disable search engine compose plate feature to avoid a UI feature exclusive to Google search promoting AI mode
A full list of changes from the previous release (version 143.0.7499.34.0) is available through the Git commit log between the releases.
This update is available to GrapheneOS users via our app repository and will also be bundled into the next OS release. Vanadium isn't yet officially available for users outside GrapheneOS, although we plan to do that eventually. It won't be able to provide the WebView outside GrapheneOS and will have missing hardening and other features.

Comparing 143.0.7499.34.0...143.0.7499.34.1 · GrapheneOS/Vanadium
Privacy and security enhanced releases of Chromium for GrapheneOS. Vanadium provides the WebView and standard user-facing browser on GrapheneOS. It depends on hardening in other GrapheneOS reposito...GitHub