「 Finland, Sweden, Norway, Denmark and Estonia are rolling out offline card payment systems to provide a back-up if internet connections are lost, including due to sabotage, Bank of Finland board member Tuomas Valimaki said on Wednesday 」
Search
Items tagged with: cybersecurity
The Liberty Phone delivers uncompromising security for government communications- No Surveillance.
puri.sm/products/liberty-phone…
#LibertyPhone #SecureGovMobile #MadeInUSA #SupplyChainSecurity #OpenSource #PureOS #EndToEndEncryption #HardwareSecurity #GOTSSolution #CyberSecurity
This dumb password rule is from Polytechnique Montreal.
Passwords must have a minimum length of 8 characters
Passwords must have a maximum length of 30 characters
Passwords must contain a minimum of 2 digits
Passwords must contain a minimum of 2 letters
Password must be different than the last one used
Passwords may contain these special characte...
dumbpasswordrules.com/sites/po…
#password #passwords #infosec #cybersecurity #dumbpasswordrules

Polytechnique Montreal - Dumb Password Rules
Passwords must have a minimum length of 8 characters Passwords must have a maximum length of 30 characters Passwords must contain a minimum of 2 digits Passwords must contain a minimum of 2 letters Password must be different than the last one use…dumbpasswordrules.com
Long passwords are important.
Source: reddit.com/r/dataisbeautiful/c…
#tech #technology #encryption #password #passwords #Security #cybersecurity #computing #computers #computer
Python now ships with 15,000 lines of verified cryptographic code from HACL*, covering all default hash and HMAC algorithms. The integration was seamless and automated, aiming to eliminate bugs like the 2022 SHA3 CVE. A major milestone for verified crypto in mainstream software.
jonathan.protzenko.fr/2025/04/…
#Python #CyberSecurity #Cryptography #AppSec
15,000 lines of verified cryptography now in Python
In November 2022, I opened issue 99108 on Python’s GitHub repository, arguing that after a recent CVE in its implementation of SHA3, Python should embrace verified code for all of its hash-related infrastructure.Jonathan Protzenko
npr.org/2025/04/15/nx-s1-53558…
#cybersecurity #doge #privacy
🧠 Microsoft is reintroducing Recall in Windows 11 — a feature that captures screenshots every 3 seconds of your activity to create an AI-powered memory. What could go wrong?
It now includes:
🔐 Opt-in only
📍 Local device processing
🧑💻 Windows Hello authentication
But many still ask: is it a productivity boost or a privacy liability? 😳
Even with safeguards, the idea of your system quietly watching everything you do raises serious concerns about digital trust.
#Privacy #Windows11 #AI #Cybersecurity #TechNews
arstechnica.com/security/2025/…
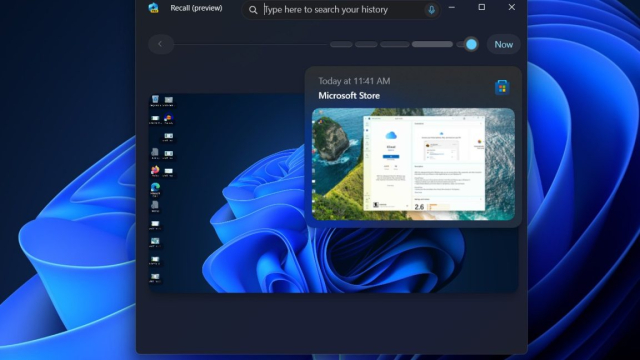
That groan you hear is users’ reaction to Recall going back into Windows
Snapshotting and AI processing a screen every 3 seconds. What could possibly go wrong?Dan Goodin (Ars Technica)
#Tuta birthday sale: 62% off Legend plan
tuta.com/special-offer/?t-src=…
#email #privacy #cybersecurity

Tuta: Turn ON privacy for free with secure emails, calendars & contacts | Tuta
Tuta guarantees your data stays private for free & without ads. Quantum-resistant encryption makes Tuta the best secure technology solution to protect your privacy.Tuta
This dumb password rule is from Bank Millennium.
Passwords limited to 8 digits.
dumbpasswordrules.com/sites/ba…
#password #passwords #infosec #cybersecurity #dumbpasswordrules
🛡️#Curl has been around for 26 years—and it’s still secure! How?
European Open Source Academy member, @bagder Stenberg, joined the latest episode of Security Weekly Productions, discussing how Curl and #libcurl have maintained security and reliability over decades.
A must-listen for #developers and #cybersecurity enthusiasts! 👨💻🔒
📺 Explore the episode : youtube.com/watch?v=0UavY_kKKic
👉 Learn more about the Academy : europeanopensource.academy/new…
#CyberSecurity #CurlProject #AppSec
Open Source in Europe Enters a New Era with a Successful First European Open Source Awards Ceremony | European Open Source Academy
A significant milestone for the European open source community was reached on January 30, 2025, when the European Open Source Awards (OSAwards 2025) celebrated the launch of the European Open Source Academy with the Inaugural Ceremony.europeanopensource.academy
"Google refuses to deny it received encryption order from UK government"
The UK’s encryption-breaking order for a backdoor into iCloud isn’t a one-off.
The secret hearing happening RIGHT NOW is bigger than just Apple. If the government wins, our right to privacy and security falls.
Other services will be hit.
therecord.media/google-refuses…
Sign our petition ➡️ you.38degrees.org.uk/petitions…
#e2ee #encryption #apple #google #privacy #security #cybersecurity #ukpol #ukpolitics #tech

Google refuses to deny it received encryption order from UK government
U.S. lawmakers say Google has refused to deny that it received a Technical Capability Notice from the U.K. — a mechanism to access encrypted messages that Apple reportedly received.therecord.media
This dumb password rule is from TreasuryDirect.
Will allow most passwords longer than 8 characters. Doesn't tell you there is a
maximum length of 16 characters. Then forces you to type it with an on-screen keyboard
with no capital letters.
dumbpasswordrules.com/sites/tr…
#password #passwords #infosec #cybersecurity #dumbpasswordrules

TreasuryDirect - Dumb Password Rules
Will allow most passwords longer than 8 characters. Doesn't tell you there is a maximum length of 16 characters. Then forces you to type it with an on-screen keyboard with no capital letters.dumbpasswordrules.com
📣 Break the silence: Save encryption!
The UK government wants to be able to access anything, anywhere, any time — from your pics to your docs.
It begins with Apple. Other services will be next. That's why we must take a stand NOW!
Sign and share our petition ⬇️
you.38degrees.org.uk/petitions…
#encryption #e2ee #Apple #privacy #security #cybersecurity #ukpolitics #ukpol #icloud #tech

Keep our Apple data encrypted
It is reported that the Home Office has ordered Apple to build a backdoor into its encrypted services so that they can get hold of content that any Apple user has upload to the cloud. Encryption keeps our private information safe and secure.38 Degrees
The message is clear across the political divide: let's hear it!
The UK government should argue in open court why they want to make us less secure by ordering a backdoor into Apple encryption.
A secret Tribunal would be an affront to the privacy and security issues at stake. It must be held in public.
Read the joint letter from ORG, Big Brother Watch and Index on Censorship ⬇️
openrightsgroup.org/press-rele…
#Apple #encryption #e2ee #privacy #security #cybersecurity #ukpol #ukpolitics #tech

Make the Investigatory Powers Tribunal on Apple Encryption a Public Hearing
Rights groups call for Apple’s closed appeal against the Home Office’s encryption-breaching order to be opened to the public.Open Rights Group
Bipartisan US Congress Members want the secrecy around the UK's encryption-breaking order to be lifted.
"It is imperative that the UK's technical demands of Apple - and of any other US companies - be subjected to robust, public analysis and debate."
“Secret court hearings featuring intelligence agencies and a handful of individuals approved by them do not enable robust challenges on highly technical matters.”
wyden.senate.gov/news/press-re…
#encryption #e2ee #Apple #privacy #security #cybersecurity
Bipartisan Members of Congress to UK Spy Court: UK Gag Orders for Surveillance Backdoors Threaten Americans’ Security and Privacy, Impede Congressional Oversight | U.S. Senator Ron Wyden of Oregon
The Official U.S. Senate website of Senator Ron Wyden of Oregonwww.wyden.senate.gov
UK MPs have joined the chorus of voices wanting the Apple case to be held in public.
"If the Home Office wants to have effectively unfettered access to the private data of the (innocent) general public, they should explain their case in front of the public."
🗣️ David Davis MP.
"People deserve to know what's happening to their private personal information."
🗣️ Victoria Collins MP.
news.sky.com/story/apple-vs-ho…
#encryption #e2ee #Apple #privacy #security #cybersecurity #ukpolitics #ukpol

Apple vs Home Office encryption court battle must be held in public, say MPs
A row between the tech giant and the government over customer data will reportedly move to London's High Court this week – but the hearing will be held behind closed doors.Tim Baker (Sky News)
📣 Make it public!
The call is getting louder for a public hearing of the appeal over the UK's order to break Apple encryption.
Alongside the joint letter from ORG, Big Brother Watch and Index on Censorship, UK MPs, US Congress Members and the BBC want the secrecy to end.
bbc.co.uk/news/articles/c4g0rr…
#encryption #e2ee #privacy #security #cybersecurity #ukpol #ukpolitics #Apple #tech

Pressure grows to hold secret Apple privacy hearing in public
Civil liberties campaigners have joined US politicians and the BBC in saying Friday's hearing should not be secret.Tom Singleton (BBC News)
Everybody should learn how to use GPG.
#gpg #gnupg #encryption #security #privacy #cybersecurity #linux #pgp
🔐 If Privacy is outlawed...
Here's how you can stop them: 👉 t.co/8z8lI9eRDo
#PrivacyMatters #Encryption #CyberSecurity #TurnOnPrivacy #PGP
France is about to pass the worst surveillance law in the EU. We must stop them now! | Tuta
An amendment to the “Narcotrafic” law is moving to the French National Assembly. Remind your legislators that a backdoor for the good guys only is not possible.Tuta
Hier könnt ihr unser aktuelles Spotlight-Interview mit @Tutanota, einer datenschutzfreundlichen E-Mail-, Kalender- und Kontaktlösung aus Deutschland lesen:
blog.iode.tech/de/tuta-datensc…
#tuta #spotlight #privacy #cybersecurity #opensource #datenschutz
February 16th #BlackHistoryMonth spotlight:
Get to know @blackgirlshack!
"BlackGirlsHack meets the #InfoSec needs left unmet by existing services by providing hands-on skills that are focused on people who are upskilling and reskilling in #cybersecurity."
BlackGirlsHack - About
BlackGirlsHack is the leading cybersecurity training nonprofit in the country. The nonprofit organization, which is open to all, provides training, career services, study groups, and resources people looking to upskill and reskill in technology and c…blackgirlshack.org
"The consensus among cybersecurity experts could not be clearer:
There is no way to provide government access to end-to-end encrypted data without breaking end-to-end encryption, thus putting every user’s security and privacy at risk."
Join the voice of experts in the joint letter to stop the UK's order to break encryption – Sign and share our petition today ⬇️
#encryption #privacy #Apple #cybersecurity #ukpolitics #ukpol
you.38degrees.org.uk/petitions…

Keep our Apple data encrypted
It is reported that the Home Office has ordered Apple to build a backdoor into its encrypted services so that they can get hold of content that any Apple user has upload to the cloud. Encryption keeps our private information safe and secure.38 Degrees
ORG and over 150 signatories call on the UK government to RESCIND its demand to create a backdoor to Apple encryption.
It "jeopardises the security and privacy of millions, undermines the UK tech sector, and sets a dangerous precedent for global cybersecurity."
"The world’s second-largest provider of mobile devices would be built on top of a systemic security flaw, putting all of its users’ security and privacy at risk."
#encryption #privacy #cybersecurity #ukpolitics
globalencryption.org/2025/02/j…
Joint Letter on the UK Government's use of Investigatory Powers Act to attack End-to-End Encryption – Global Encryption Coalition
On 13 February 2025, 109 civil society organizations, companies, and cybersecurity experts, including Global Encryption Coalition members, published a joint letter to the British Home Secretary Yvette Cooper calling on the UK Home Office to rescind i…Ryan Polk (Global Encryption Coalition)
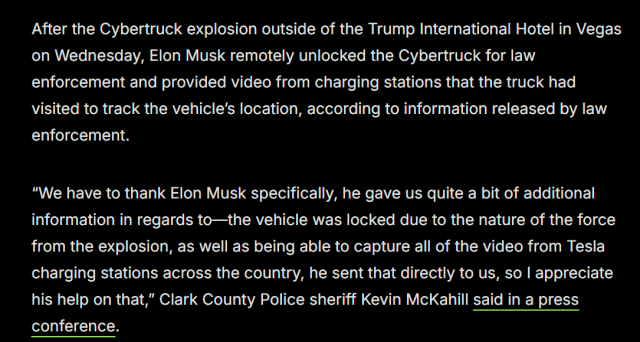
Unbelievable
#ElonMusk’s US #DOGE Service are feeding sensitive data into #AI software via #Microsoft’s #cloud
#Musk’s US #DOGE Service have fed sensitive data from across the #Education Dept into #ArtificialIntelligence software to probe the agency’s programs & spending…. The AI probe includes data w/personally identifiable info for people who manage grants, & sensitive internal financial data…
#law #security #InfoSec #CyberSecurity #NationalSecurity #Trump #TrumpCoup
washingtonpost.com/nation/2025…
This is what I think about whenever infosec wonks on here start telling people they should use matrix or xmpp+omemo or whatnot instead of signal
To be fair, I understand the arguments and to a large extent I agree with the critiques. However, I think anyone making these recommendations is vastly underestimating the capacity or appetite for most people to deal with the user experiences presented by these alternatives.
User experience is the ultimate force multiplier. For anything that requires network effects to function (ie most anything involving communication), if it doesn't *just work* then you've lost 90% of your audience.
#matrix #xmpp #infosec #cybersecurity #signal #ux #design #ui #encryption #privacy #crypto
Via Tom's Hardware: Facebook flags Linux topics as 'cybersecurity threats' — posts and users being blocked
Does this mean that Meta/Facebook is going to also ban mentions of:
- #Android phones?
- #SteamDeck / #SteamOS?
- Most "smart" cars, TV's, appliances?
- Most (somewhere around 90 percent) of the top Websites?
- Talk of Meta's own internal infrastructure?
What an absolutely asinine thing to do. Linux is incredibly prevalent in the technology landscape today. Yes, #linux on the desktop is a small percentage of the overall devices on the market today. However, linux usage in #embedded, #server, and #appliance applications is to a level where censoring references to it is insanity.
The irony of all of this? Zuckerfaces recent pull back of moderation on Meta's sites.... Meaning it's now okay to bash socially vulnerable populations, spread tons of mis-information on many social and political topics... But linux?"Oh no! That's a #CyberSecurity threat!"
This reeks of political #tomfoolery. I won't be surprised if it's eventually revealed that our new overlords put pressure on #Meta to #censor linux.
tomshardware.com/software/linu…

Facebook flags Linux topics as 'cybersecurity threats' — posts and users being blocked
DistroWatch is one of the largest affected organizations.Mark Tyson (Tom's Hardware)
Let's say China manages to get just a little bit of data about people from just a few of these ... 😑
"China's overlapping tech-industrial ecosystems"
high-capacity.com/p/chinas-ove…
#cybersec #cybersecurity #infosec #itsec #china #privacy #gdpr #dataprotection #dataskydd
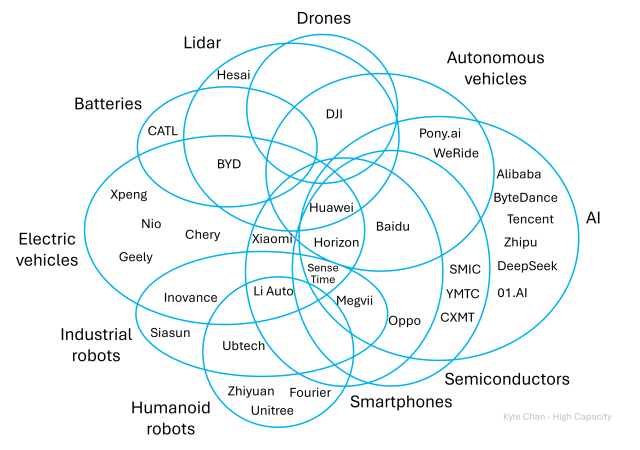
China's overlapping tech-industrial ecosystems
EVs, batteries, lidar, drones, robotics, smartphones, AI. China's progress across a range of overlapping industries creates a mutually reinforcing feedback loop.Kyle Chan (High Capacity)
Thinking about a new Linux laptop to run Linux on? Going with Linux laptop vendors can be a good option as they offer seamless hardware-software integration, pre-installed Linux distros, and guaranteed driver compatibility. Here are available Linux laptop vendors 😎👇
Find high-res pdf books with all my #linux and #cybersecurity related infographics at study-notes.org
Dan Nanni's Infographics and Study Notes
Explore high-quality infographics on Linux, cybersecurity, and networking. Perfect for certifications, technical knowledge, and tech career upskilling.study-notes.org
Microsoft Office 2016 and Office 2019 will no longer receive software updates, technical support, or bug and security fixes after 14.10.2025.
Consider migrating to LibreOffice.
LibreOffice is free to use.
LibreOffice supports Office file formats.
Install LibreOffice and compare it with your version of Office.
Website: libreoffice.org
Mastodon: @libreoffice
1/4
#Microsoft #Office2016 #Office2019 #Office #LibreOffice #CyberSecurity #Privacy #InfoSec #FreeSoftware #OpenSource #FOSS
Home | LibreOffice - Free and private office suite - Based on OpenOffice - Compatible with Microsoft
Free office suite – the evolution of OpenOffice. Compatible with Microsoft .doc, .docx, .xls, .xlsx, .ppt, .pptx. Updated regularly, community powered.www.libreoffice.org
Think twice before scanning QR codes: 60% of them are spam. Be careful when travelling for business, too - scammers are even putting fake QR codes on parking meters. Stay cautious to protect your business data
#QRCodes #PhishingScam #CyberSecurity techradar.com/pro/security/the…

The majority of QR codes are spam, new survey claims
Almost 60% of emails with a QR code are spam, so be on your guardEllen Jennings-Trace (TechRadar pro)
Wow. US CISA recommends using end to end encrypted mobile communications.
Found this via @Tutanota blog
cisa.gov/sites/default/files/2…
Short passwords are an open door for hackers. 🕵️ 🔓
🔑 Longer = Stronger.
How long is yours?
🔒 Learn more & secure your accounts today: tuta.com/blog/minimum-password…
Tuta Survey Results: Only about half the users use passwords that are long enough. | Tuta
Why password length matters for online security & best practices to protect your online accounts.Tuta
element.io/blog/in-an-increasi…
#matrix #element #e2ee #cybersecurity #chat

In an increasingly volatile world, governments turn to Element and Matrix
Governments need digitally sovereign, secure and interoperable communications. The demand for Matrix is palpable.Steve Loynes (Element Blog)
This dumb password rule is from Xfinity Modem.
Only letters and numbers are valid. No spaces or special characters.
Seen on model TG3482G. ARRIS Group, Inc. Firmware: TG3482PC2_3.5p17s1_PROD_sey
dumbpasswordrules.com/sites/xf…
#password #passwords #infosec #cybersecurity #dumbpasswordrules

Xfinity Modem - Dumb Password Rules
Only letters and numbers are valid. No spaces or special characters. Seen on model TG3482G. ARRIS Group, Inc. Firmware: TG3482PC2_3.5p17s1_PROD_seydumbpasswordrules.com
This dumb password rule is from Oracle.
*Should not* or *must not*? RFC 2119 may want a word with you.
dumbpasswordrules.com/sites/or…
#password #passwords #infosec #cybersecurity #dumbpasswordrules
This dumb password rule is from MySwissLife.
User ID *has to* be 8 characters exactly, password *has to be* 8 characters and numbers only.
dumbpasswordrules.com/sites/my…
#password #passwords #infosec #cybersecurity #dumbpasswordrules
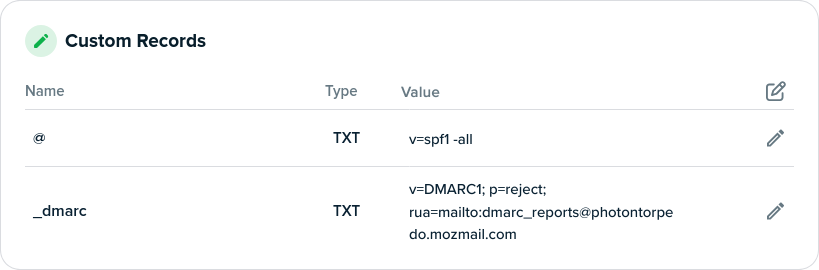
Important reminder, if you own a domain name and don't use it for sending email.
There is nothing to stop scammers from sending email claiming to be coming from your domain. And the older it gets, the more valuable it is for spoofing. It could eventually damage your domain's reputation and maybe get it blacklisted, unless you take the steps to notify email servers that any email received claiming to come from your domain should be trashed.
Just add these two TXT records to the DNS for your domain:
TXT v=spf1 -all
TXT v=DMARC1; p=reject;
The first says there is not a single SMTP server on earth authorized to send email on behalf of your domain. The second says that any email that says otherwise should be trashed.
If you do use your domain for sending email, be sure to add 3 records:
SPF record to indicate which SMTP server(s) are allowed to send your email.
DKIM records to add a digital signature to emails, allowing the receiving server to verify the sender and ensure message integrity.
DMARC record that tells the receiving email server how to handle email that fails either check.
You cannot stop scammers from sending email claiming to be from your domain, any more than you can prevent people from using your home address as a return address on a mailed letter. But, you can protect both your domain and intended scam victims by adding appropriate DNS records.
UPDATE: The spf and the dmarc records need to be appropriately named. The spf record should be named "@", and the dmarc record name should be "_dmarc".
Here's what I have for one domain.
One difference that I have is that I'm requesting that email providers email me a weekly aggregated report when they encounter a spoof. gmail and Microsoft send them, but most providers won't, but since most email goes to Gmail, it's enlightening when they come.
#cybersecurity #email #DomainSpoofing #EmailSecurity #phishing
#curl 8.11.1 has been released. It includes a fix to #CVE_2024_11053 - a #vulnerability I discovered.
It is a logic flaw in the way curl parses .netrc file. In certain situations, the configured password can be sent to a incorrect host. Luckily the affected configurations should be quite rare and thus the situation is unlikely to occur often.
The issue has existed in the curl source code for almost twenty-five years.
• curl.se/docs/CVE-2024-11053.ht…
• hackerone.com/reports/2829063
No AI tools were used in discovering or reporting the vulnerability.