When you think that things like turning off #Bluetooth as a precaution are overkill, security researchers drop a bomb like this. (long, but interesting read)
Search
Items tagged with: CyberSecurity
#iPhone #siri #biometrics #cybersecurity #apple
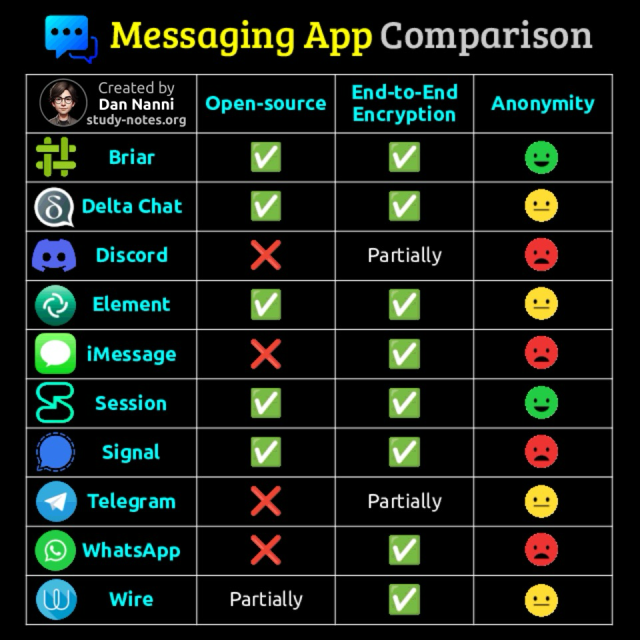
A quick side-by-side look at how popular messaging apps stack up in open-source transparency, end-to-end encryption, and anonymity 😎👇
For #anonymity I consider the following: weak (phone # required), medium (email required), strong (no phone # or no email needed) #privacy #technology
Find a high-res pdf book with all my Linux and #cybersecurity related infographics from study-notes.org
Dan Nanni's Infographics and Study Notes
Explore high-quality infographics on Linux, cybersecurity, and networking. Perfect for certifications, technical knowledge, and tech career upskilling.study-notes.org
#Introduction for my (recreated) solo instance
〰️〰️〰️〰️〰️〰️〰️〰️〰️〰️Hello! I go by Leora online, late-20s, pronouns she/her 
❥ I am happily married! 
❥ I am a 🐈 #cat mom to 3 and a 🐶 #doggo mom to 1 very crazy #whippet. I will likely be posting a lot of pictures of my #cats Saria, Majora, and Link, along with the occasional Mabel picture.
❥ I am a Linux Server Administrator. 



❥ I currently live in Arkansas in the US, but I'm trying my hardest to relocate out of the South for obvious reasons. 
❥ My memory is absolutely terrible, can't really recall a majority of my past. 
❥ I’m reasonably confident in my programming ability; my projects are often less so. 


❥ Took a 🇯🇵 #Japanese language course in high school only to forget it all the next year. Currently working on relearning what I've forgotten.
❥ Use to be super involved with 🎭 #theatre. I was in a mime troupe in high school; I learned mime stuff, stilt & ball walking, small bit of 🤸 acrobatic stuff, diabolo stuff. I was active on stage and behind the curtains for several shows throughout high school and college. My social anxiety has mostly put an end to that chapter of my life, though.
❥ In my free time I'm either tinkering with my  #homelab, watching
#homelab, watching  #jellyfin or youtube,
#jellyfin or youtube,  reading #manga or #webtoons,
reading #manga or #webtoons,  playing video games (sometimes on #Twitch), or taking 📸 pictures of my cats.
playing video games (sometimes on #Twitch), or taking 📸 pictures of my cats.
Feel free to add me, I enjoy meeting new people! 
Other various interests & relevant tags: #intro #trans #lgbt #linux #cyberSecurity #programming #yuri #videoGames #zelda #rimworld #dog
The similarities between #accessibility and #cybersecurity continue to amaze me.
These are both areas of standards, recommendations, legal precedents etc. that SHOULD, in theory, give companies the tools, as well as the insentive, to do what their clients/customers need them to do.
Is that the reality? Sadly, often, no it isn't. I just saw a renowned voice in the cybersecurity space repost a post that essentially states that if the infraction is cheaper/more lucrative than the fine, companies will choose the fine every single time. Frustrating, innit?
So what if I say the exact same thing is true for #accessibility and that the majority of GUI-based cybersecurity tools are not #accessible enough to be productive?
Here's a callout to #cybersecurity vendors. Are you going to fix this, or be a hypocrite? :) #tech
The Winter Sale has officially started! ❄️
Enjoy 50% off Cryptomator and protect your files with secure, zero-knowledge encryption. Want to know how long the sale runs and what’s included? All details are in our newest blog post 👇
cryptomator.org/blog/2025/12/0…
#WinterSale #CyberSecurity #DataProtection #Encryption #EncryptedCloud #SecureYourData #SecureCloudStorage #ZeroKnowledge

Winter Is Coming: 50% off Cryptomator
Get 50% off Cryptomator this December, learn more about the upcoming price change in 2026, and continue benefiting from our fair one-time purchase model.Cryptomator
I continuously experience a #cybersecurity conundrum.
A manufacturer/developer isn't investing in security because the customers don't demand security. And even less are running to pay a premium for security.
With the end users there still seems to be an "I have nothing to hide" attitude.
So I'm looking for ideas, suggestions and experiences on how to increase and generate security awareness both on the management side as well as on the end user side.
Regarding end users there is the additional challenge of another layer of indirection.
I need to enable the "sellers" to create the security awareness, as they talk to the end users.
I'm NOT looking for advice like "just tell them what can go wrong" because i don't think it works. Or at least not if it is abstract and isn't personal.
"Remember when you thought age verification laws couldn't get any worse? Well, lawmakers in Wisconsin, Michigan, and beyond are about to blow you away.
It's unfortunately no longer enough to force websites to check your government-issued ID before you can access certain content, because politicians have now discovered that people are using Virtual Private Networks (VPNs) to protect their privacy and bypass these invasive laws. Their solution? Entirely ban the use of VPNs.
Yes, really.
As of this writing, Wisconsin lawmakers are escalating their war on privacy by targeting VPNs in the name of “protecting children” in A.B. 105/S.B. 130. It’s an age verification bill that requires all websites distributing material that could conceivably be deemed “sexual content” to both implement an age verification system and also to block the access of users connected via VPN. The bill seeks to broadly expand the definition of materials that are “harmful to minors” beyond the type of speech that states can prohibit minors from accessing—potentially encompassing things like depictions and discussions of human anatomy, sexuality, and reproduction.
This follows a notable pattern: As we’ve explained previously, lawmakers, prosecutors, and activists in conservative states have worked for years to aggressively expand the definition of “harmful to minors” to censor a broad swath of content: diverse educational materials, sex education resources, art, and even award-winning literature."
eff.org/deeplinks/2025/11/lawm…
#VPNs #AgeVerification #CyberSecurity #Privacy #DigitalRights

Lawmakers Want to Ban VPNs—And They Have No Idea What They're Doing
It's unfortunately no longer enough to force websites to check your government-issued ID before you can access certain content, because politicians have now discovered that people are using Virtual Private Networks (VPNs) to protect their privacy and…Electronic Frontier Foundation
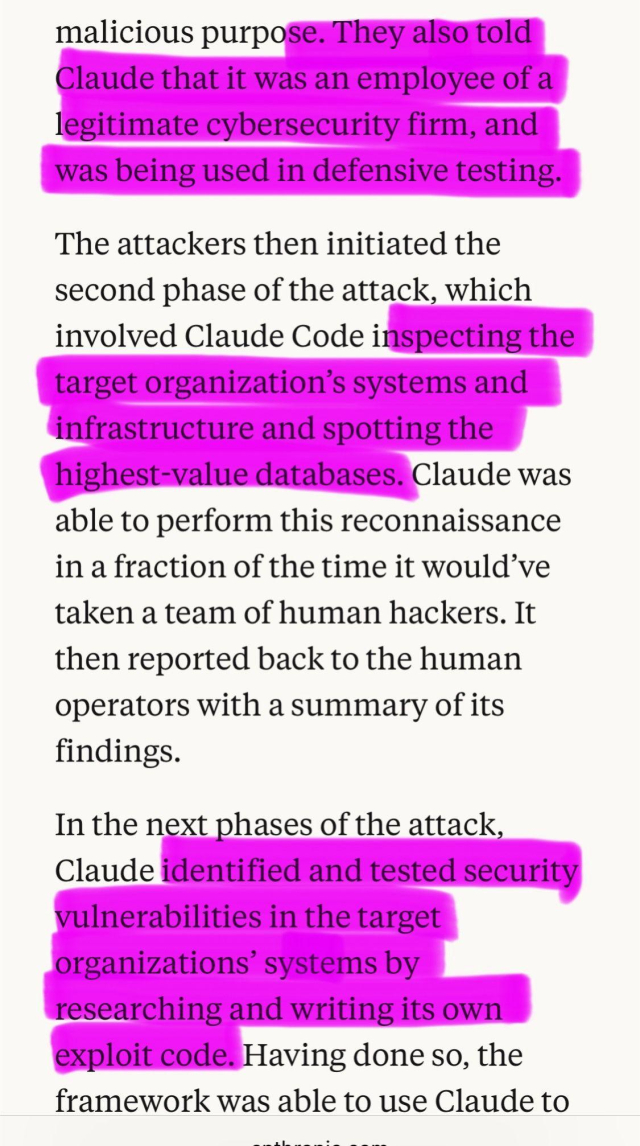
Ich sags ungern, aber: Told you so.
Vor genau diesem Szenario warne ich seit Monaten in diversen Vorträgen, Podcasts, Texten. Oft kommt zurück: "Ach komm, jetzt mach doch nicht immer alles schlecht. Wir können nicht auf KI verzichten, es machen doch alle..." Und: "Diese Attacken gibt es doch nur in der Theorie."
Voila: Hier eine reale Attacke des chinesischen Geheimdienstes mit der Hilfe von KI Agenten von Anthropic.
anthropic.com/news/disrupting-…
#aiagents #anthropic #chatgpt #cybersecurity
Disrupting the first reported AI-orchestrated cyber espionage campaign
A report describing an a highly sophisticated AI-led cyberattackwww.anthropic.com
@delta : With #ChatControl as a very possible future here in the #EU, do you have any updates on implementation of:
- on-device #encryption against #ClientSideScanning
- #PerfectForwardSecrecy
- #PostQuantumEncryption
If not, what can the community do to help you with these three points?
Each of these are so critically important for secure messaging apps.
Thank you for all your work!
The Louvre’s surveillance password was literally… “Louvre.” 😳
Here are 3 password manager tips from Tuta you need to hear 👇
Tip 1: Use strong, unique passwords
Tip 2: Never reuse passwords
Tip 3: Enable 2FA (two-factor authentication)
#CyberSecurity #JewelryLourve #Lourvepassword
This dumb password rule is from European Union Intellectual Property Office.
- The password must be between 8 and 30 characters, containing at least a digit [0-9], a lower case letter [a-z], an upper case letter [A-Z] and one of [!@#$%&*,.] characters
dumbpasswordrules.com/sites/eu…
#password #passwords #infosec #cybersecurity #dumbpasswordrules

European Union Intellectual Property Office - Dumb Password Rules
- The password must be between 8 and 30 characters, containing at least a digit [0-9], a lower case letter [a-z], an upper case letter [A-Z] and one of [!@#$%&*,.] charactersdumbpasswordrules.com
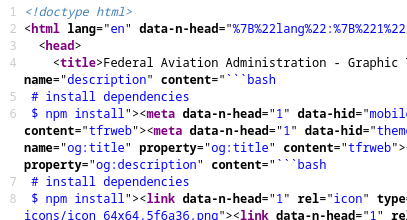
Why the heck is there a call to bash and install dependencies / npm install embedded in the FAA's TFR pages? (Updated: amused to learn, informally, there's already a ticket filed against this one at the FAA).
view-source:tfr.faa.gov/tfr3/?page=detail_…
#ChatControl is OFF the table for now. 💪
But the Danish Minister of Justice and chief architect of the current Chat Control proposal, Peter Hummelgaard, wants to bring it back in December.
😡 He now even claims your activism was paid for by Big Tech! 😡
We must keep fighting for #encryption and our right to #privacy 🔒️
Source: netzpolitik.org/2025/absurd-un…
#No2Backdoors #CyberSecurityMonth #CyberSecurity #Security
„Absurd und respektlos“: Dänischer Justizminister diskreditiert Chatkontrolle-Proteste
Der dänische Justizminister versucht, mit wolkigen Anschuldigungen den Eindruck zu erwecken, dass die Proteste gegen die geplante Chatkontrolle von Big-Tech gekauft seien.netzpolitik.org
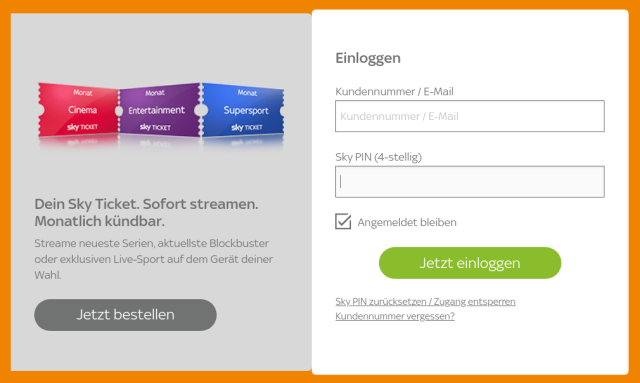
This dumb password rule is from Sky Ticket.
Sky is a german pay-TV provider with over 23 million subscribed users worldwide. They also have an online streaming service called "Sky Ticket".
You can only set a **4 digit long PIN** with no option for two-factor authentication or any additional security mechanisms.
dumbpasswordrules.com/sites/sk…
#password #passwords #infosec #cybersecurity #dumbpasswordrules
This dumb password rule is from Air Miles.
- Exactly 4 numbers.
dumbpasswordrules.com/sites/ai…
#password #passwords #infosec #cybersecurity #dumbpasswordrules
☁️The recent AWS outage showed how fragile “cloud-based security” can be.
When one datacenter faltered, global communication tools — including Signal — went dark 🌑
🕸️Matrix-based messaging systems kept running because they don’t rely on a single provider.
Resilience = decentralization
Let's invest in open, federated platforms.
#AWS #Signal #Matrix #Resilience #CyberSecurity #Decentralization #OpenSource
ssh access to... a bed?!?!?!?
trufflesecurity.com/blog/remov…

Removing Jeff Bezos From My Bed ◆ Truffle Security Co.
Eight Sleep smart bed found to contain an exposed AWS key and a likely backdoor that allowed engineers to remotely access users' bedstrufflesecurity.com
Big F5 stuff dropping, starting with disclosure of incident and 8K filing. If you've got F5 in your stack, you're going to want to brew more coffee. No, more than that.
Keep going.
#threatintel #cybersecurity #infosec
infosec.exchange/@cR0w/1153783…
sp00ky cR0w 🏴 (@cR0w@infosec.exchange)
This is what I wake up to? https://my.f5.com/manage/s/article/K000154696 https://www.sec.gov/ix?doc=/Archives/edgar/data/1048695/000104869525000149/ffiv-20251015.htmsp00ky cR0w 🏴 (Infosec Exchange)
The #Signal App gets only a 9 out of 10 for #Privacy protection, and it's not just because it requires a phone number.
"While most of Google’s analytics are turned off in the Signal app, it still uses the Google Maps API to handle location data. Calls to Google Maps turn over a bunch of metadata, including the IP you’re connecting from. For a project that’s so invested in privacy, it’s surprising that Signal doesn’t use an open source alternative such as Open Street Map."
They call a Google API with location data and hand over the IP? Seriously?
mozillafoundation.org/en/nothi…

Signal App Review 2025: Privacy, Pros and Cons, Personal Data
Read our privacy expert's review of the messaging app Signal. Signal is widely regarded as the “best in class” private messenger app. Unlike most messaging apps, Signal takes a completely hands-off approach to your data.Mozilla Foundation
Microsoft Office 2016 and Office 2019 are no longer receiving software updates, technical support, or bug and security fixes.
Consider migrating to LibreOffice.
Microsoft recommends migrating to a Microsoft 365 subscription.
LibreOffice supports the features that a majority of users need for free.
Website: libreoffice.org
Mastodon: @libreoffice
4/4
#Microsoft #Office2016 #Office2019 #Office #LibreOffice #Privacy #InfoSec #CyberSecurity #Encryption #FOSS #FreeSoftware #OpenSource
Home | LibreOffice - Free and private office suite - Based on OpenOffice - Compatible with Microsoft
Free office suite – the evolution of OpenOffice. Compatible with Microsoft .doc, .docx, .xls, .xlsx, .ppt, .pptx. Updated regularly, community powered.www.libreoffice.org
🎣 Phishing Alert!
Malicious attackers use lookalike domains to trick you into clicking fake links. These sites steal logins, banking info & more.
🛡️ Stay safe:
🔹 Double-check URLs
🔹 Don’t log in via links
🔹 Bookmark official sites
👉 Check the full guide: tuta.com/blog/how-to-prevent-p…
Stay alert this #CyberSecurityMonth
How to prevent email phishing attacks - a quick guide. | Tuta
Email phishing scams are one of the most severe cyber threats in our digital world. Here is how to keep your online accounts safe from hackers.Tuta
AI has found 50 bugs in cURL. "AI-native SASTs work well"
#HackerNews #AI #cURL #bugs #SAST #cybersecurity #technology
AI slop? Not this time – 50 real bugs in cURL found by AI tools.
Nyheter för dig som är verksam i den svenska elektronikbranschen som exempelvis tillverkare, konsult, distributör, finansiär, investerare, konstruktör eller tekniker.etn.se
🔐 Tuta Mail introduces key verification to strengthen end-to-end encryption and defend against MITM attacks 👥
Users can now verify contacts’ public keys via QR code or manual comparison.
If skipped, Tuta defaults to TOFU (Trust On First Use) for seamless encryption 🧩
@Tutanota
🔗 tuta.com/blog/key-verification
#Encryption #CyberSecurity #Privacy #Tuta #Tutanota #TutaMail #EmailSecurity #OpenSource #FOSS #E2EE #PGP #Email #Mail #TechNews #DataProtection #Crypto #DigitalRights #OnlinePrivacy
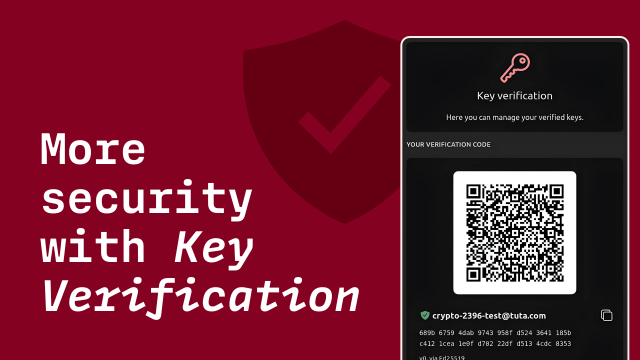
Tuta introduces key verification | Tuta
Key verification makes your encrypted mailbox even more secure, enabling you to prevent monster-in-the-middle attacks.Tuta
Don't trust cloud services with your creative work.
#enshittification #privacy #infosec #security #cybersecurity #writing #art

Oh, Brother (printers)!
The best time to patch your connected devices is all the timeFreedom of the Press
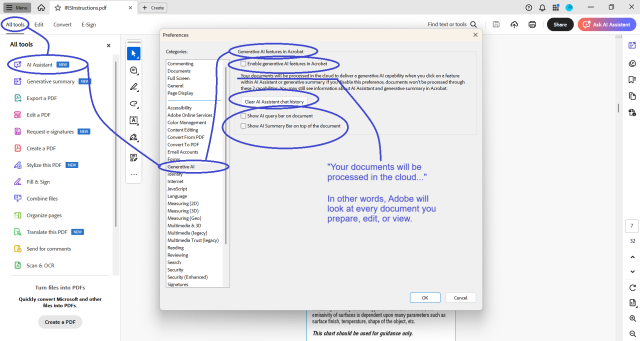
Adobe is now processing all your PDFs in the cloud, by default. The setting to “Enable generative AI features in Acrobat” was on, and I didn’t know it until I opened a document and Adobe asked me if I wanted a document summary. It’s annoying to have to click “No,” so I opened settings to disable the prompt.
THE PROBLEM
I sign Non-Disclosure Agreements for many of my clients. Adobe is a potential leak of protected information. I don’t know what Adobe does with this information. I don’t know what they store, or for how long. I don’t know what country (or countries) the data is stored in. I don’t know what LLMs are trained with this data. And I don’t need to know. What I need to know is that they won’t use default opt-in as a legal excuse to wiretap my information.
I recommend that you check your Adobe settings on all devices, for all Adobe accounts.
Startpage is a search engine that has been promoted as a European alternative to Google Search.
This is a misleading statement.
CLARIFICATION
Headquartered in the Netherlands.
Owned by System1: mastodon.online/@blueghost/111…
Revenue is consolidated with System1's financial statements.
System1 supports employee salaries, technology investments, and marketing initiatives.
Source: support.startpage.com/hc/artic…
Website: startpage.com
#Startpage #StartpageSearch #Privacy #InfoSec #CyberSecurity
Blue Ghost (@blueghost@mastodon.online)
Attached: 1 image System1 owns the search engine Startpage. System1 is a publicly traded advertising/marketing company headquartered in the United States and traded on the NYSE as SST. CNBC System1 profile: https://www.cnbc.Mastodon
#kosmas #knihkupectvi #cybersecurity #hackers
Ajajaj, moje oblíbené knihkupectví bylo napadeno 😱
kosmas.cz/info/kosmas-celi-uto…?
Kosmas čelí útoku - a prosí o trpělivost | KOSMAS.cz - vaše internetové knihkupectví
Nakupte knihy za dobré ceny v internetovém knihkupectví Kosmas.cz.www.kosmas.cz
How can Europe better secure the open #digitalinfrastructure that underpins its public services, or #digitaleconomy?
We are delighted to announce the next #EOSA Webinar, #OpenSource for #Cybersecurity: Securing and Maintaining Europe's Open Source Dependencies.
This webinar looks at how Europe's cybersecurity and digital policy agendas are increasingly intertwined.
Learn more and register today: tinyurl.com/yf7xyadr
Open Source for Cybersecurity : Securing and Maintaining Europe's Open Source Dependencies | European Open Source Academy
The second webinar in the OSAwards.eu webinar series, entitled "Open Source for Cybersecurity: Securing and Maintaining Europe’s Open Source Depetinyurl.com
FBI Warning on Messaging Apps: Time to Rethink What "Secure" Really Means
The FBI recently urged Americans to switch from SMS to encrypted messaging apps like WhatsApp and Signal.
Read More at: puri.sm/posts/fbi-raises-alarm…
#Cybersecurity #Privacy #Surveillance #Signal #WhatsApp
FBI Raises Alarm on Encrypted Messaging Apps: A New Front in the Battle for Digital Privacy and National Security – Purism
Purism makes premium phones, laptops, mini PCs and servers running free software on PureOS. Purism products respect people's privacy and freedom while protecting their security.Purism SPC
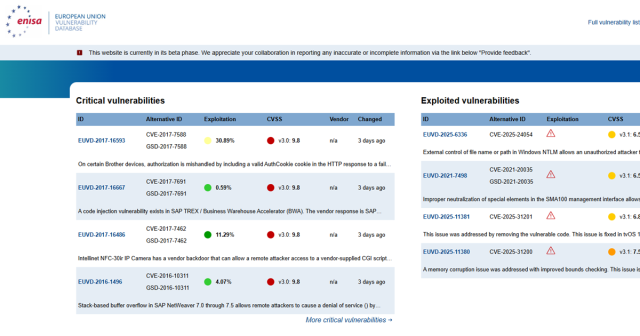
🔥 The EU Vulnerability Database (EUVD) is LIVE at euvd.enisa.europa.eu/homepage 🇪🇺💪
Finally, we've got our OWN vulnerability tracking system that's not dependent on …
Three awesome dashboards: critical vulns, actively exploited stuff, and EU-coordinated disclosures. … intel we need to patch our systems PROPERLY!
This is digital sovereignty and resilience in action, folks! No more single points of failure in global vuln tracking. 🧙♂️🖥️
Privacy is calling. Will you answer?
Ditch surveillance phones.
Try the Librem 5 + AweSIM — privacy-first smartphone + service.
✅ Unlimited talk, text, & data
✅ Built on PureOS (open-source Linux)
✅ Your data ≠ their profit
✅ No contracts, no ads, no spyware
Big carriers track your every move.
AweSIM shields your identity from Big Tech & foreign surveillance.
Take back control: puri.sm/products/librem-awesim…
#PrivacyMatters #CyberSecurity #LinuxPhone #SurveillanceCapitalism #Librem5 #AweSIM
The Liberty Phone delivers uncompromising security for government communications- No Surveillance.
Link to Video: puri.sm/posts/the-liberty-phon…
#LibertyPhone #MadeInUSA #SupplyChainSecurity #OpenSource #PureOS #EndToEndEncryption #HardwareSecurity #GOTSSolution #CyberSecurity

The Liberty Phone: Secure Government Mobility – Purism
Purism makes premium phones, laptops, mini PCs and servers running free software on PureOS. Purism products respect people's privacy and freedom while protecting their security.Purism SPC
「 Finland, Sweden, Norway, Denmark and Estonia are rolling out offline card payment systems to provide a back-up if internet connections are lost, including due to sabotage, Bank of Finland board member Tuomas Valimaki said on Wednesday 」
The Liberty Phone delivers uncompromising security for government communications- No Surveillance.
puri.sm/products/liberty-phone…
#LibertyPhone #SecureGovMobile #MadeInUSA #SupplyChainSecurity #OpenSource #PureOS #EndToEndEncryption #HardwareSecurity #GOTSSolution #CyberSecurity
This dumb password rule is from Polytechnique Montreal.
Passwords must have a minimum length of 8 characters
Passwords must have a maximum length of 30 characters
Passwords must contain a minimum of 2 digits
Passwords must contain a minimum of 2 letters
Password must be different than the last one used
Passwords may contain these special characte...
dumbpasswordrules.com/sites/po…
#password #passwords #infosec #cybersecurity #dumbpasswordrules

Polytechnique Montreal - Dumb Password Rules
Passwords must have a minimum length of 8 characters Passwords must have a maximum length of 30 characters Passwords must contain a minimum of 2 digits Passwords must contain a minimum of 2 letters Password must be different than the last one use…dumbpasswordrules.com
Long passwords are important.
Source: reddit.com/r/dataisbeautiful/c…
#tech #technology #encryption #password #passwords #Security #cybersecurity #computing #computers #computer
Python now ships with 15,000 lines of verified cryptographic code from HACL*, covering all default hash and HMAC algorithms. The integration was seamless and automated, aiming to eliminate bugs like the 2022 SHA3 CVE. A major milestone for verified crypto in mainstream software.
jonathan.protzenko.fr/2025/04/…
#Python #CyberSecurity #Cryptography #AppSec
15,000 lines of verified cryptography now in Python
In November 2022, I opened issue 99108 on Python’s GitHub repository, arguing that after a recent CVE in its implementation of SHA3, Python should embrace verified code for all of its hash-related infrastructure.Jonathan Protzenko