Search
Items tagged with: Infosec
 BREAKING: #Google to start deleting unused #email accounts so other people can use them.
BREAKING: #Google to start deleting unused #email accounts so other people can use them.
🤔 What could possibly go wrong?
🤦♂️ Techbros are (still) idiots.
https://blog.google/technology/safety-security/updating-our-inactive-account-policies/

Updating our inactive account policies
Starting later this year, we are updating our inactivity policy for Google Accounts to 2 years across our products.Ruth Kricheli (Google)
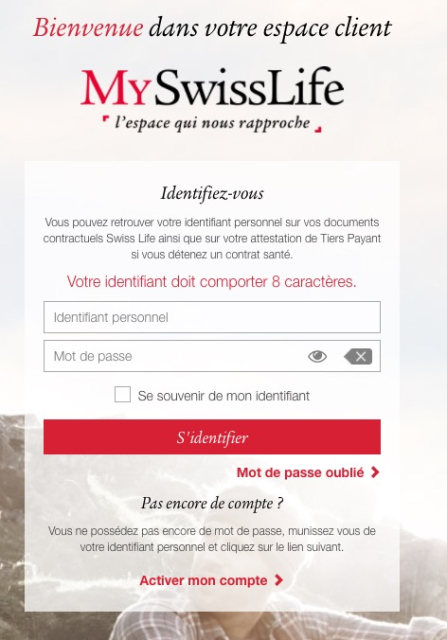
This dumb password rule is from MySwissLife.
User ID *has to* be 8 characters exactly, password *has to be* 8 characters and numbers only.
https://dumbpasswordrules.com/sites/myswisslife/
#password #passwords #infosec #cybersecurity #dumbpasswordrules
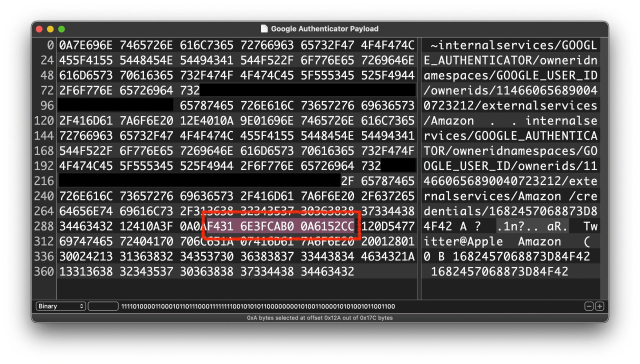
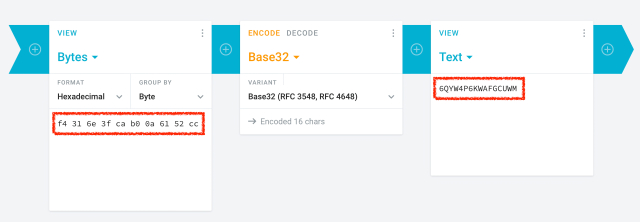
Google has just updated its 2FA Authenticator app and added a much-needed feature: the ability to sync secrets across devices.
TL;DR: Don't turn it on.
The new update allows users to sign in with their Google Account and sync 2FA secrets across their iOS and Android devices.
We analyzed the network traffic when the app syncs the secrets, and it turns out the traffic is not end-to-end encrypted. As shown in the screenshots, this means that Google can see the secrets, likely even while they’re stored on their servers. There is no option to add a passphrase to protect the secrets, to make them accessible only by the user.
Why is this bad?
Every 2FA QR code contains a secret, or a seed, that’s used to generate the one-time codes. If someone else knows the secret, they can generate the same one-time codes and defeat 2FA protections. So, if there’s ever a data breach or if someone obtains access .... 🧵
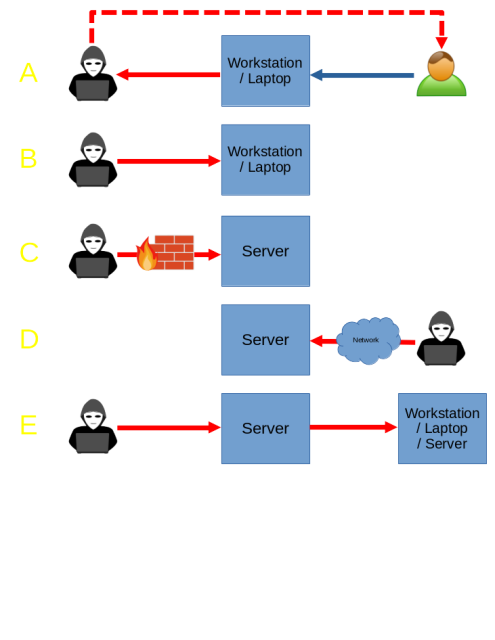
This dumb password rule is from Banco Mercantil.
8 to 15 chars. No special chars allowed but requires special chars. Also
requires lowercase, uppercase, and numbers. Consecutive chars are
prohibited. Did I mention the page hangs while you type? That eye icon
tho.
https://dumbpasswordrules.com/sites/banco-mercantil/
#password #passwords #infosec #cybersecurity #dumbpasswordrules
Banco Mercantil - Dumb Password Rules
8 to 15 chars. No special chars allowed but requires special chars. Also requires lowercase, uppercase, and numbers. Consecutive chars are prohibited. Did I mention the page hangs while you type? That eye icon tho.dumbpasswordrules.com
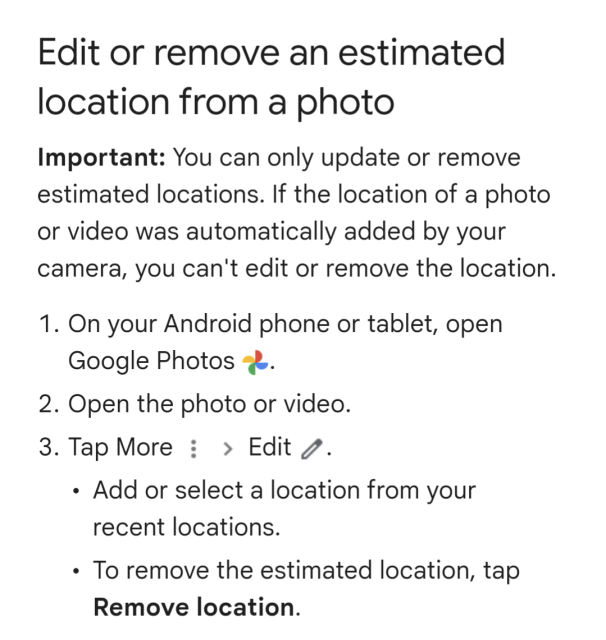
So Google is now preventing people from removing location data from photos taken with Pixel phones.
Remember when Google's corporate motto was "don't be evil?"
Obviously, accurate location data on photos is more useful to a data mining operation like Google.
From Google: "Important: You can only update or remove estimated locations. If the location of a photo or video was automatically added by your camera, you can't edit or remove the location."
It's enshitification in action.
Source: https://support.google.com/photos/answer/6153599?hl=en&sjid=8103501961576262529-AP
#technology #tech @technology #business #enshitification #Android #Google @pluralistic #infosec
https://letsencrypt.org/
#opensource #TLS #PKI #infosec

Let's Encrypt
Let's Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG).letsencrypt.org
My kids are all grown now, so I am more than willing to travel / relocate. If you have any leads or tips on some good companies, please let me know.
#GetFediHired
[matrix] • [SimpleX]

Matrix - Decentralised and secure communication
You're invited to talk on Matrix. If you don't already have a client this link will help you pick one, and join the conversation. If you already have one, this link will help you join the conversationmatrix.to
In this video, we downloaded the authenticator app from the App Store and we opened it as we monitored the iPhone network traffic. While the app was showing the permission prompt, we captured at least 3 calls made by the app sending diagnostics to Microsoft. The app sent 14 KB of analytics even before accepting the prompt.
The message on the prompt actually says that Microsoft needs to collect diagnostic data in order to keep Authenticator secure and up to date. 😵💫
#Privacy #Cybersecurity #2FA #InfoSec #Security #Microsoft
https://youtu.be/r5456XXG6v0

Privacy: Microsoft Authenticator sends analytics even before accepting the privacy statement
When opening Microsoft Authenticator for the first time after downloading it from the App Store, it prompts the user to accept sharing diagnostics with Micro...YouTube
Red Queen Dynamics needs 1) a leader for engineering/cloud infrastructure, and 2) a product designer. We are a remote-first security company and we welcome people from all backgrounds and life journeys. #infosec #infosecjobs #hiring #cybersecurity
You can apply here! Tech Lead: https://www.linkedin.com/jobs/view/3475289250/
Product Designer: https://www.linkedin.com/jobs/view/3475289426/
Or stay up to date with all our job postings on our website: https://rqdn.io/career-opportunities
Career Opportunities
Looking for a place to stretch your wings? Check out our remote work opportunities that range from sales to product development.rqdn.io
At the moment, when you press delete on a Twitter DM (an individual message or conversation) the DM isn't actually deleted from Twitter's servers, just your inbox view.
So people in Europe have been making requests for Twitter to blitz all their messages. It hasn't properly answered them. And now regulators are looking at it
Full story here: https://www.wired.com/story/delete-twitter-dms-gdpr/
#Twitter #gdpr #infosec #technology #news #wired

Want to Delete Your Twitter DMs? Good Luck With That
People in Europe are making GDPR requests to have their private messages erased, but Elon’s team is ignoring them.Matt Burgess (WIRED)
https://gist.github.com/cutiful/4f36da3ed37b24f9a7106064393f5e7f
I wonder how many instance admins using Cloudflare know about this? My hunch is most do not, because the primary justification I see for using Cloudflare here is DDoS protection.
Cloudflare won't help if the attacker knows your origin IP, and you can't hide that with Cloudflare alone, due to the nature of ActivityPub.
#MastoAdmin #InfoSec

Detecting the real IP of a Cloudflare'd Mastodon instance
Detecting the real IP of a Cloudflare'd Mastodon instance - mastodon-ip.mdGist
But first I need to do a bunch of explaining because most people (my past self from a few months ago included) are largely unfamiliar with the Korean software landscape. See: they have those “security” applications that everyone has to install if they want to use online banking for example.
What could possibly go wrong with applications developed by private vendors without any kind of security vetting and that everyone in a country has to install, whether they like it or not? A lot of course.
In this first blog post I explain how in my limited understanding the current situation came about, show why the companies lack incentive to really invest in security and give you a first slight idea of the disastrous consequences.
No, I’m not exaggerating. The next blog post is scheduled for January 9th, and it will be about a specific application. I submitted seven vulnerability reports for this one. It took a real issue and claimed to have solved it – by making matters considerably worse than they were.
https://palant.info/2023/01/02/south-koreas-online-security-dead-end/
#infosec #ApplicationSecurity #privacy #korea
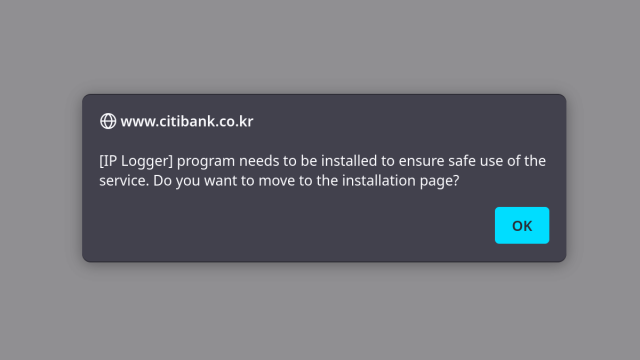
South Korea’s online security dead end
Websites in South Korea often require installation of “security applications.” Not only do these mandatory applications not help security, way too often they introduce issues.Almost Secure
Steals all your SSH keys!
"If you installed PyTorch-nightly on Linux via pip between December 25, 2022 and December 30, 2022, please uninstall it and torchtriton immediately, and use the latest nightly binaries (newer than Dec 30th 2022)."
#infosec #machinelearning #deeplearning
https://pytorch.org/blog/compromised-nightly-dependency/
https://news.ycombinator.com/item?id=34202836

PyTorch
An open source machine learning framework that accelerates the path from research prototyping to production deployment.pytorch.org
✊🏽 We must hold them accountable for the risks and damages their actions cause: it's unacceptable to allow society to continue this way.
 Thanks to #CCC for helping expose the dangerous truth.
Thanks to #CCC for helping expose the dangerous truth.#SurevillanceCapitalism #infosec
https://web.archive.org/web/20221227125216/https://www.nytimes.com/2022/12/27/technology/for-sale-on-ebay-a-military-database-of-fingerprints-and-iris-scans.html

For Sale on eBay: A Military Database of Fingerprints and Iris Scans
German security researchers studying biometric capture devices popular with the U.S. military got more than they expected for $68 on eBay.Kashmir Hill (The New York Times)
You think unencrypted URLs are bad? Take a look at this seven years old presentation by Martin Vigo and Alberto Garcia Illera: https://www.blackhat.com/docs/eu-15/materials/eu-15-Vigo-Even-The-Lastpass-Will-Be-Stolen-deal-with-it.pdf. Starting with page 69 it explains how the custom_js feature could be abused to extract users’ passwords.
Guess what, this feature is still present and used on PayPal for example. Still no encryption and nothing to protect the users. No change whatsoever in at least seven years that LastPass was made aware of this issue.
Instead, when disclosing #LastPassBreach they again lie that they don’t have access to your passwords. But they do. Anyone with access to their server does. NSA could order them to extract your passwords. Hackers who gain access to their server could abuse this to get your passwords. Or just to run their JavaScript code on any website, and then they don’t even need your passwords.
And that’s only one out of the many documented backdoors that LastPass chooses to ignore, both in terms of implementation and their public communication.
#infosec #ApplicationSecurity
If you know the folks who run these lists and can help remove Codeberg from them, I’d appreciate it.
More details: https://codeberg.org/Codeberg/Community/issues/850
CC @Codeberg
#codeberg #infosec #foss #freeSoftware

Codeberg on more block lists
Further to #841 (which is now closed), Codeberg is on some other block lists: - https://osint.digitalside.it/Threat-Intel/lists/latestdomains.txt - https://v.firebog.net/hosts/Prigent-Malware.txt See https://mastodon.ar.Codeberg.org
#infosec #wikipedia #security #hiring
https://boards.greenhouse.io/wikimedia/jobs/4611087
U2F keys are now supported on all @Tutanota clients.
(Tutanota is also an avoidthehack recommended encrypted email provider).
#mfa #2fa #privacy #cybersecurity #infosec #infosecurity
https://tutanota.com/blog/posts/app-update

U2F support is now also available on Android and iOS.
Celebrate with us the new release of Tutanota!Tutanota

Bug on Hyundai app allows hackers to unlock and start cars remotely - KoDDoS Blog
Researchers have detected a vulnerability on Hyundai and SiriusXM. The vulnerability allows an attacker to start and unlock cars remotely. An attacker can execute commands on a car by just knowing the vehicle identification number.Ali Raza (KoDDoS)
This Inkplate e-ink screen shows Conway's Game of Life, seeded from tarpits I have on the Internet. The tarpits are programs on my computer that superficially look like insecure Telnet and Remote Desktop services, but actually exist to respond super slowly and make bots scanning the Internet 'get stuck'.
When a bot connects to the tarpit, the data it sends gets squished into a 5x5 grid and 'stamped' onto a Game of Life board. Data from a bot at the IP address 1.1.x.x will get stamped on the top left corner, data from a bot at 254.254.x.x will get stamped on the bottom right corner.
Conway's Game of Life, a set of simple rules that govern whether cells should turn on or off, updates the display once per second. The result is that bot attacks end up appearing as distinct 'creatures', that get bigger and more angry looking over time (as their centre is updated with new data). After the attack finishes, the 'creature' eventually burns itself out.
Despite that description, it's a really chill piece of art that doesn't draw too much attention but I can happily watch for a long time.
Credit for the idea goes to @_mattata, I had been wanting to make a real-life version of XKCD #350 for years before seeing his Botnet Fishbowl project.
#projects #inkplate #esp32 #eink #infosec #tarpit
https://youtu.be/YdbA7Z8Ae4w
#security #supplyChain #infosec #manufacturing #electronics #hardware #phones #teamKyle

Why The U.S. Fell Behind In Phone Manufacturing
Made in China. It’s a common phrase known by many. Cell phones, TV screens and game consoles are just some of the millions of electronics manufactured and im...YouTube
Our Made-in-USA-electronics Librem 5 USA phone also got a number of shout-outs. Pretty neat!
https://youtu.be/YdbA7Z8Ae4w #security #supplychain #infosec #manufacturing

Why The U.S. Fell Behind In Phone Manufacturing
Made in China. It’s a common phrase known by many. Cell phones, TV screens and game consoles are just some of the millions of electronics manufactured and im...YouTube
#Privacy #Security #Crytology #Cryptography #InfoSec

Episode 7: Scaling Up Secure Messaging to Large Groups With MLS!
Raphael Robert from Wire talks about how MLS wants to scale secure messaging to groups with hundreds or even thousands of participants.Cryptography FM
https://www.hertzbleed.com/
When constant-time crypto code doesn’t run in constant time…
#infosec
#News #Firefox #Mozilla #privacy #cookies #infosec #Cybersecurity
https://www.theregister.com/2022/06/30/firefox_tracking_cookie_loophole/

Firefox kills another tracking cookie workaround
URL query parameters won't work in version 102 of Mozilla's browserBrandon Vigliarolo (The Register)
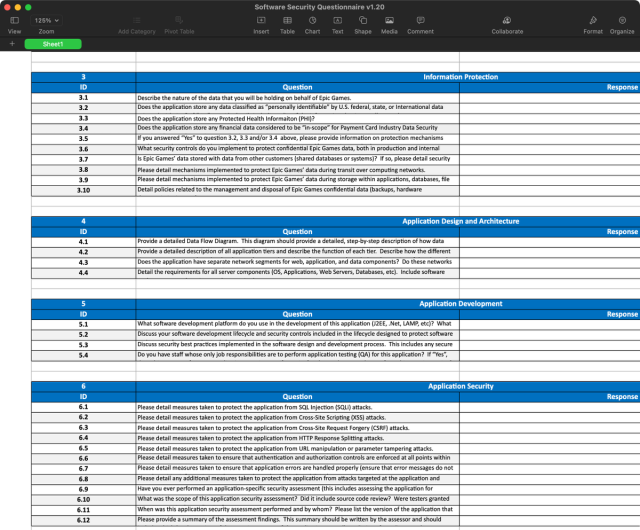
A: Social Engineering
B: Physical Access
C: Vuln Exploitation
D: Lateral Movement
E: Supply Chain Attack
What am I missing?
https://threatpost.com/iphones-attack-turned-off/179641/
“Evil Never Sleeps: When Wireless Malware Stays On After Turning Off iPhone”
https://arxiv.org/pdf/2205.06114.pdf
#infosec

iPhones Vulnerable to Attack Even When Turned Off
Wireless features Bluetooth, NFC and UWB stay on even when the device is powered down, which could allow attackers to execute pre-loaded malware.Elizabeth Montalbano (Threatpost)

Cyber Engineer
Cyber EngineerExperience: SeniorsLocation: Dulles, VANode is supporting a U.S. Government customer on a large mission-critical development and sustainment program to design, build, deliver, and operate a network operations environment; including …infosec-jobs.com
Hi, I'm Max. I live in #NYC and do #journalism at PCMag where I cover #infosec, #security, and #privacy. I also write reviews of #VPN and professionally complain about #capitalism. I'm the Unit Chair of the ZDCG #union and moonlight as a #labor organizer. If you want to learn about how to unionize your workplace, plz DM me. I play #banjo badly and think about #medieval literature. I'm spending too much money on #fountainpens.
Looking for a new challenge.
I am really good at:
- #infosec marketing
- #technicalwriting
- #marketing
- #infosec
- #scripting (#python)
Hoping to bypass the HR filter. If you are #recruiting at a humane company that respects & values employees, please reach out!
#remote
(++ to anyone who picks up on my good/excessive hashtag usage)
I did two years of engineering school and two years of journalism. I'm a geek who loves to tell a story.
I make #comics, #illustrations & #paintings. I do a lot of #memoir work, kids books (#kidlit), and speculative #fantasy.
I've spent about 15 years in the world of #infosec (thank you, day job!) and I do a lot of writing and podcasting in this field. I'm not an expert but I am a nerd for #tech and #privacy.
Links are all in my profile if you want to learn more. I'm not gonna spam you.
This is not my first time on Mastodon but I'm trying to consolidate a bunch of my older profiles right here.