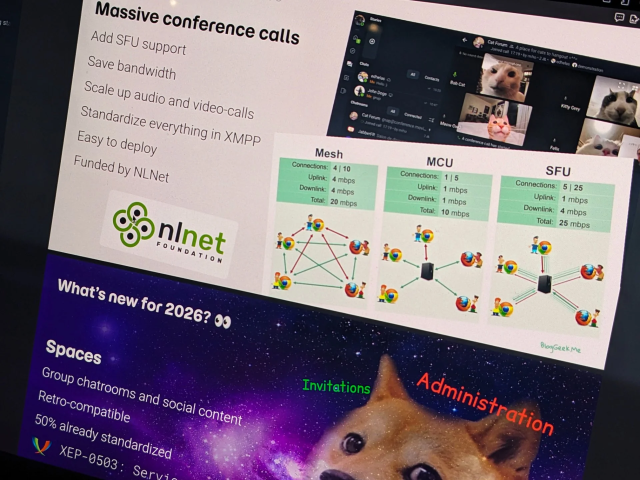
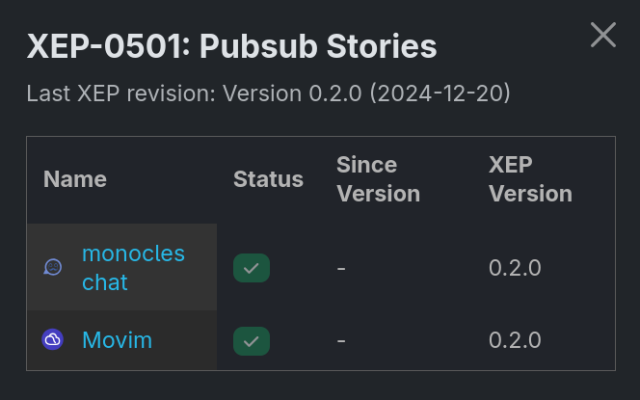
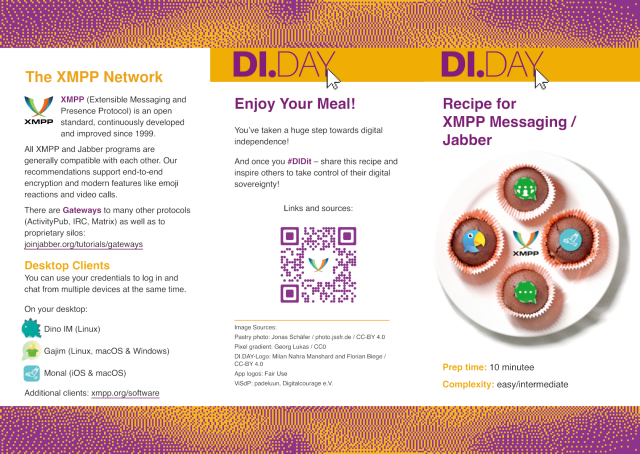
#XSF Announcement
Tomorrow the 28th #XMPP #Summit is taking place in #Brussels, #Belgium.
Start at 09:00 am (UTC+1).
If you come in person, reach out before (almost full). Else join remotely
xmpp.org/2025/11/xmpp-summit-2…
Meet us at #FOSDEM 2026, too!
#jabber #chat #opensource #messaging #federation
XMPP Summit 28 | XMPP - The universal messaging standard
The XMPP Standards Foundation (XSF) is exited to announce the 28th XMPP Summit taking place in Brussels, Belgium next year - just before FOSDEM 2026. The XSF invites everyone interested in development of the XMPP protocol to attend, and discuss all …xmpp.org