🦾6 AI Tos Used by Hackers
🔹Poisongpt
🔹Wormgpt
🔹Speechif.ai
🔹Deepl.ai
🔹Freedom.ai
🔹Passgan.ai
🦾6 AI Tos Used by Hackers
🔹Poisongpt
🔹Wormgpt
🔹Speechif.ai
🔹Deepl.ai
🔹Freedom.ai
🔹Passgan.ai

To better manage growing responsibilities, 84% of CISOs believe the role should be split into technical (CISO) and business-focused roles.Help Net Security
ICYMI: Internet Archive hacked, data breach impacts 31 million users
1. Nobody is safe.
2. A non-profit is using bcrypt to hash passwords, no reason why your for-profit company can't do the same.
American Water shuts down online services after #cyberattack
American Water is the largest water and wastewater treatment utility in the US…
OT systems not affected - so appears this only affects their IT systems. Suspected nation state activity (Russia).
(I encourage everyone sharing this with their friends because cyber attacks absolutely can have direct “real world” consequences.)
T-Mobile reaches $31.5 million settlement with FCC over past data breaches
Apparently, T-mobile is now mandated to implement better cybersecurity controls, such as properly segmenting networks and using phishing resistant #MFA.
This settlement covers the breaches in 2021, 2022, and 2023. Will we get a 2024 special? 💀
Today I made my threat hunt book publicly known on LinkedIn. So far the feedback has been overwhelming. I do hope my efforts will contribute to educate both threat hunters and SOC analysts!
Tor insists its #network is safe after German cops convict CSAM dark-web admin
Kind of boils down to opsec fail here. Using outdated software, which in this case didn’t properly secure Tor connections.
Timing attacks are still viable (especially with hostile nodes), but this reads as an #opsec fail to me.
Remember: a major part of anonymity is maintaining great opsec.
Obligatory: Tor is not “just for criminals,” despite one getting caught in this case (glad he did tbh). Regular people use Tor everyday.
#cybersecurity #security #privacy
theregister.com/2024/09/19/tor…

Outdated software blamed for cracks in the armorIain Thomson (The Register)
Say it with me...
Network vulnerability!!!
A quick story/rant.. my cousin got my mother a new coffee maker. I don't expect my mom to use the WiFi functionality, but I'm still concerned about why we would need a whole coffee maker to have a small computer in it... I understand the versatility of not having a hub, and that hubs are also a single point of access for any malicious actors, but I'm sure a hub for multiple devices instead of a thing for a coffee maker would be updated much more frequently, and supported for longer.
If nothing else, maybe I can pull it into my janky Home Assistant setup somehow.
Even if it doesn't end up being a gateway for snooping on home network, it is quite silly, in my opinion.
Now, I must go check to see if anyone's hacked at these yet lol...
#NetSec #Networking #cybersecurity #cybersec #IoT #smarthome #coffee #keurig #hacking
Privacy-focused Tuta Mail Opens Second Office in Munich:
See how Tuta stacks up with other email providers in keeping your information private:
The city of Columbus Ohio got hacked by a ransomware gang, they didn't pay the ransom so the gang released half of the stolen data which included secret police and prosecutor files. The leak exposed countless victims, witness and confidential informants personal info and communications with the city.
The city claimed NO info was leaked. A cyber security enthusiast went to the media and proved otherwise.
When you search for "identita občana" (Citizen Identity, ID for the Czech e-government), the first link #Google gives you (as an ad) is to a malicious website.
I wonder if companies like Google will ever be held accountable for spreading dangerous scams and getting paid for it.
I learned about secure software development on the job, but like ethical computing (which I've talked about before), this should also be included in formal education. Because of the current threat models, topics like security by design and zero-trust frameworks are critical when developing Internet systems. linuxfoundation.org/press/linu…
#securitybydesign #security #softwaredevelopment #zerotrust #infosec #cybersecurity #education

Findings show nearly one-third of industry professionals are not familiar with secure software development practicesThe Linux Foundation
#WhatsApp for #Windows lets Python, PHP scripts execute with no warning
Granted, Python needs to be installed on the system prior.
Meta says they will not bother to fix this, despite maintaining a built-in list of potentially dangerous file types (ex: .exe)
We've partnered with Abside to create a groundbreaking secure communication solution for government agencies. Our Liberty phone, featuring Made in USA Electronics and running our non-Android PureOS, now integrates with Abside's N79 5G private network. The result? A fully American-made, ultra-secure platform for government personnel to communicate and access critical data on the move. Privacy, security, and performance – all in one package. #Purism #Cybersecurity #Abside
puri.sm/posts/abside-and-puris…

Purism makes premium phones, laptops, mini PCs and servers running free software on PureOS. Purism products respect people's privacy and freedom while protecting their security.Purism SPC
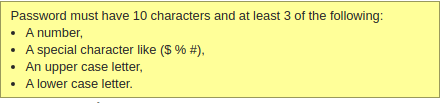
This dumb password rule is from SecureAccess Washington.
Central authentication for all Washington State services
(DoL, ESD, etc).
Password must have *exactly* 10 characters, but form happily
lets you enter more and only throws errors after submit,
providing no useful feedback.
dumbpasswordrules.com/sites/se…
#password #passwords #infosec #cybersecurity #dumbpasswordrules
Central authentication for all Washington State services (DoL, ESD, etc). Password must have *exactly* 10 characters, but form happily lets you enter more and only throws errors after submit, providing no useful feedback.dumbpasswordrules.com
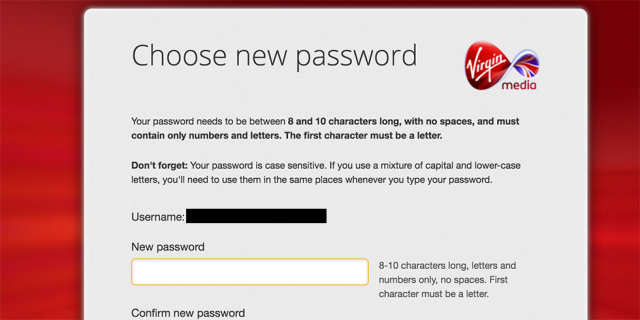
This dumb password rule is from Virgin Media.
Your password needs to be between 8 and 10 characters long, with no
spaces, and must contain only numbers and letters. The first character
must be a letter.
Feb 2020 Update: policy remains the same but the description is hidden
leaving you to guess the acceptable length/chars. Users are now lef...
dumbpasswordrules.com/sites/vi…
#password #passwords #infosec #cybersecurity #dumbpasswordrules
Your password needs to be between 8 and 10 characters long, with no spaces, and must contain only numbers and letters. The first character must be a letter.dumbpasswordrules.com
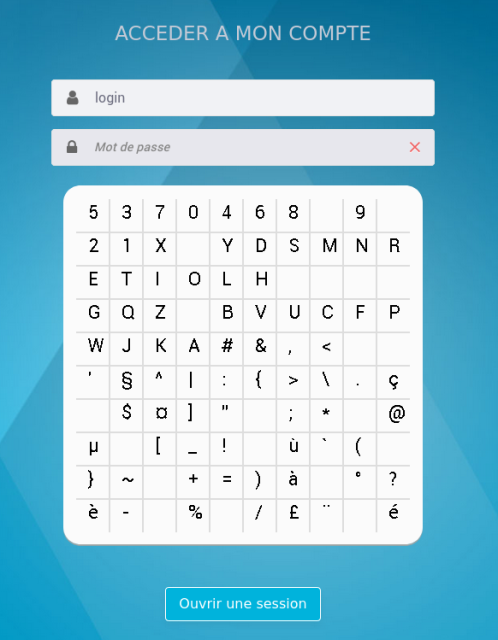
This dumb password rule is from Banque de Tahiti.
You have to enter your password using this *very* Frenchy keypad. You don't have lowercase letters, the blanks are not spaces but just non-clickable gaps, but as a compensation you have some weird symbols that your keyboard does not have a key for (e.g. `µ`).
No accessible version available.
dumbpasswordrules.com/sites/ba…
#password #passwords #infosec #cybersecurity #dumbpasswordrules
You have to enter your password using this *very* Frenchy keypad. You don't have lowercase letters, the blanks are not spaces but just non-clickable gaps, but as a compensation you have some weird symbols that your keyboard does not have a key for (e…dumbpasswordrules.com
STAGGERING: Nearly all #ATT customers' text & call records breached.
An unnamed entity now has an NSA-level view into Americans' lives.
Damage isn't limited to AT&T customers.
But everyone they interacted with.
Also a huge national security incident given government customers on the network.
And of course, third party #Snowflake makes an appearance.
cnn.com/2024/07/12/business/at…
#infosec #cybersecurity #telco #cellular #privacy #security #breach
Computer hardware maker #Zotac exposed customers' RMA info on Google Search
Misconfiguration of permissions folders holding customer info related to RMAs have been indexed by search engines like #Google. As a result, it has shown up on SERPs.
Information leaked includes invoices, addresses, and contact information.
Fun fact: Security Misconfiguration is number 6 on the OWASP Top 10 Web app Security Risks.
Do you want to help secure GNOME and get a reward? 🏅
We are testing a new program in which people get a payment for reporting and/or solving vulnerabilities.
yeswehack.com/programs/gnome-b…
From €500 to €10,000 depending on criticality 💶
For now only GLib is in scope but we will expand the list of modules and advertise as the program grows.
In partnership with @yeswehack and @sovtechfund
#GNOME #infosec #FreeSoftware #security #bugBounty #OpenSource #cybersecurity

GNOME Bug Bounty Program bug bounty program detailsYesWeHack #1 Bug Bounty Platform in Europe
This dumb password rule is from CenturyLink Residential.
Your password is too long. But how long can it be? Oh, we won't tell you.
dumbpasswordrules.com/sites/ce…
#password #passwords #infosec #cybersecurity #dumbpasswordrules
Russian hackers read the emails you sent us, Microsoft warns more customers.
Read more in my article on the @Bitdefender blog:
bitdefender.com/blog/hotforsec…
#cybersecurity #databreach #microsoft

More of Microsoft's clients are being warned that emails they exchanged with the company were accessed by Russian hackers who broke into its systems and spied on staff inboxes.Hot for Security
ID Verification Service for #TikTok, #Uber, X Exposed Driver Licenses
In this case, the ID verification vendor leaked admin credentials and exposed people’s information (sensitive documents and status of verification) for over a year.
All for “age verification” we introduce another EZ mode way for people’s real life identities to be compromised. Companies want you to provide sensitive documents to prove you’re real/your age but can’t be bothered to invest money/time/effort in basic #security to secure what you give them.
404media.co/id-verification-se…

As social networks and porn sites move towards a verified identity model, the actions of one cybersecurity researcher show that ID verification services themselves could get hacked too.Joseph Cox (404 Media)
Wait...What?
microsoft.com/en-us/security/b…
Microsoft recently discovered a new type of generative AI jailbreak method called Skeleton Key that could impact the implementations of some large and small language models.Mark Russinovich (Microsoft Security Blog)

The background of the network attack threat environment — what is happening, and what should we worry about?Bob Cromwell: Travel, Linux, Cybersecurity
If anyone out there is looking for some #infosec / #cybersecurity-related training, feel free to peruse this giant list I've been putting together over time ⬇️
shellsharks.com/online-trainin…
Know of a training that isn’t listed here? Let me know about it and I can add!
We're truly in a golden age of resources for learning infosec/IT, the hardest part becomes choosing the best thing!
We've been doing this a while. Let's SWING for the big leagues.
Tomorrow, we're doing a deep dive on #burpSuite from a #screenReader perspective. It will be mostly #blind (as in playthrough) as I've not looked at this program for a few years, and fully blind (as in sight) given ... well ... screenReader user :)
I've learned more, and hey who knows, maybe they've improved ......
If it turns out they haven't, we'll look at @zaproxy next as a more viable, generally more #accessible alternative. See you tomorrow at 3 EST over at twitch.tv/ic_null #infosec #cybersecurity #zaproxy #portswigger #java #programming

Fully blind person hacking, coding and tinkering while using a screen reader. THM, HTB, accessibility, all the things.Twitch
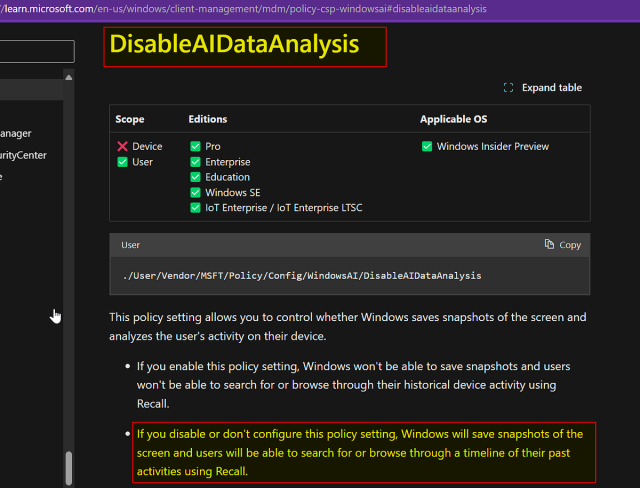
Microsoft's Recall function is looking like a total security disaster.
doublepulsar.com/recall-steali…
#Microsoft #Recall #CyberSecurity
I wrote a piece recently about Copilot+ Recall, a new Microsoft Windows 11 feature which — in the words of Microsoft CEO Satya Nadella- takes “screenshots” of your PC constantly, and makes it into an…Kevin Beaumont (DoublePulsar)

Fully blind person hacking, coding and tinkering while using a screen reader. THM, HTB, accessibility, all the things.Twitch
#Android is getting an AI-powered #scam call detection feature
Will be powered by Gemini Nano, which #Google says can be run locally and offline to process "fraudulent language and other conversation patterns typically associated with scams" and push real-time alerts during calls where detected red flags are present.
It will be opt-in, but Gemini Nano is currently only supported on Google Pixel 8 Pro and Samsung S24 series devices.
theverge.com/2024/5/14/2415621…

Google is testing a new call monitoring feature that warns users if the person they’re talking to is likely attempting to scam them and encourages them to end such calls.Jess Weatherbed (The Verge)
Mini Blue Team Diaries Story:
Was responsible for SecOps at a SaaS platform that managed lots of things for companies, including travel bookings.
We had a bunch of customers in the higher education space who used SSO to login to our app. Unfortunately, MFA within the SSO configuration was not common back then, so a compromised university account would lead to much access, including to our platform.
Suddenly, a thing we saw a lot of, was higher-ed customers reporting that they were being charged for trips that just didn't make sense. These were bookings for same day travel, usually between two African cities.
After some digging around and investigation, we figured out that a threat actor would phish or purchase the users university credentials, then, using the SSO into our environment, they'd make bookings using the travel booking feature - those bookings were made on behalf of the threat actors customers, who actually thought they were dealing with a legit, well-connected travel agent.
We were able to advise our customers on how to stop this type of thing happening, with approval rules for bookings, and ya know, MFA, and also managed to build in some detective controls so our team could detect and shut down such bookings as soon as they came in.
What made this particularly interesting though, through some OSINT, we were able to determine the true identity of the actor responsible - and we connected with them on Facebook, mainly because we wanted to ask them about their methods now that we'd all but shut down their scheme.
We chatted for a bit, and got some useful intel. At the end, the actor congratulated the team on our new controls, and said they'd moved on to using another service they'd found to make his bookings.
For more, slightly less mini, Blue Team Diaries stories like this, check out infosecdiaries.com
Start of a new project. As IC_Null on Twitch, I'll be covering hacking, coding and overall tech content. The content will be archived here.Follow my new hack...YouTube