reshared this
reshared this
CoMaps is now on IzzyOnDroid!
IzzyOnDroid is an Android store for Free & Open Source Software. The apps are free (as in „free beer“ and as in „free speech“) and Open Source.
Builds for IzzyOnDroid are directly from developers and signed by developers. This enables very fast publishing (whereas F-Droid re-builds apps from source).
There are several ways to install and update CoMaps via IzzyOnDroid:
apt.izzysoft.de/fdroid/index/a…
#IzzyOnDroid #FOSS #OpenSource #FreeSoftware #FOSSCommunity #LibreApps
Easy map navigation - Discover more of your journey - Powered by the communityIzzyOnDroid Repo Browser
reshared this
Srovnáváme naší cyklistickou infrastrukturu se zahraničím! Proč má Praha jen symbolické cyklopruhy, zatímco třeba polský Białystok buduje stovky kilometrů chráněných cyklostezek?
Podívejte se, jak se město s mnohem menším rozpočtem a rozlohou stalo vzorem pro městskou cyklistiku. Zjistíte, proč oddělené cyklostezky nejsou jen o asfaltu, ale o bezpečnosti a plynulosti dopravy pro všechny.
Městská cyklistika je budoucnost! Přináší méně zacpané silnice, zdravější obyvatele a čistší vzduch. Inspirujte se s námi a pojďme společně pomoci Praze stát se cyklistickým rájem.
V tomto videu se dozvíte:
Problémy a nedostatky pražské cyklistické infrastruktury.
Jak funguje moderní cyklistika v Białystoku.
Konkrétní čísla a srovnání cyklostezek.
Výhody rozvinuté městské cyklistiky pro celé město.
Na závěr rychlý pohled do města Lodž.
Pomozte nám zlepšit Prahu! Sdílejte toto video s úředníky, politiky a všemi, kterým záleží na budoucnosti našeho města. Máte fotky nebo videa cyklostezek ze zahraničí, které fungují? Pošlete nám je!
U SPD je to jako kdysi u Miroslava Sládka. Odpadlíci promluvili a obvinili vedení hnutí, že vyvádí z SPD peníze.
A podali kvůli tomu trestní oznámení.
"Získané informace nasvědčují tomu, že mohlo dojít a dochází k účelovému vyvádění finančních prostředků hnutí SPD," stojí v oznámení pro policii.
Jde o stejné podezření, kterému Tomio Okamura čelil už v Úsvitu. Lídr SPD pochybnosti vždy striktně odmítal.
Dnešní článek na Neovlivní
Krásné #dobréRáno a parádní den vám přeju, přátelé a kamarádi Mastodontíci ❤️💙☕️
Díky zdeňkovi @archos jsem se mohl vrátit. Děkuju vám všem za podporu v době, kdy jsem tu nebyl
(@onka6, @KaterinaGloserova , ...)
Dost se mi po vás stýskalo, jen jsem si to chtěl všechno v hlavě ujasnit. Chvíli jsem byl na BS, je tam pár fajn lidí, kteří tady nejsou, ale jinak je to tam takový neosobní...
No a pak už jsem se neuměl vrátit. Zapomněl jsem vstupní údaje...
Odpusťte mi, chyběli jste mi...
❤️💙😉
reshared this
[arch-dev-public]: New way to support Arch Linux: GitHub Sponsors
Peter Vágner reshared this.
Snow v1.0.0 is released!
It's the first release, so no changes to report. With some larger changes coming up and the FPU being mostly complete, it seemed like a good time.
v1.0.0 emulates Macintosh 128K, 512K, 512Ke, Plus, SE, Classic and Macintosh II.
Website: snowemu.com/
Downloads: github.com/twvd/snow/releases/…
Putting Zork 1 on my Atari Portfolio for some gaming on the go.
All the Rust Core Type System
Back in April, I preached a sermon titled "God is our source of worth and approval." I was preaching for myself because I need to hear that message, but a lot of other people said that it helped them as well. Sharing here in case it might help you, too.
Here's the intro:
We all need to feel worthy, accepted, and that we’re doing a good job. There can be two errors that can cause us a lot of anxiety and to make bad decisions.
One error is looking for these affirmations of worth, acceptance, and approval from other people. That will cause us to always seek to try to please people. Our actions will be controlled by them.
The other error is to stop caring about what other people think and just do whatever we want. This could be good, but we all have sinful natures and can deceive ourselves. Besides that, pride is a very dangerous thing. The original sin of the devil was pride, thinking that he knew better than God. Adam and Eve fell because the devil promised them that when they ate of the fruit of the Tree of Knowledge of Good and Evil, then they would become like God. For the first time in their lives, they choose something contrary to the will of God—because of pride.
So, what is the right way to fulfill our needs for feeling worthy, accepted, and approved?
Just like we trust God for our basic needs like food and clothing, we can look to him for our need for love, belonging, and esteem. The more that you understand this, the freer you will be in your life. You will be able to make good decisions and relate to people in a proper and healthy way.
Google doc for the full sermon notes: docs.google.com/document/d/11K…
YouTube recording of the sermon:
youtube.com/live/y_A6GKwlseo?s…
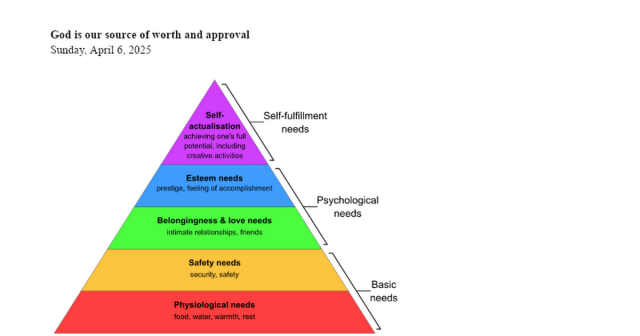
God is our source of worth and approval Sunday, April 6, 2025 We all need to feel worthy, accepted, and that we’re doing a good job. There can be two errors that can cause us a lot of anxiety and to make bad decisions.Google Docs
EVT-stage prototype multi-disk iPod; it featured multiple dual-platter 1.8" hard drives in a RAID-0 configuration with a total storage capacity of 240GB.
my boss used to have Thor's hammer. He does have the entire Batman suit from one of the movies, can't recall which one. And the Bane suit. So probably that movie.
I believe they called him up and bought back the Thor hammer because they wanted it back for a movie
An update for JAWS, ZoomText, and Fusion 2025 is now available! Download the September update and check out the "What’s New" pages to learn more:
JAWS - support.freedomscientific.com/…
ZoomText - support.freedomscientific.com/…
Fusion - support.freedomscientific.com/…
We built local backdoors for Signal, 1Password & Slack through V8 heap snapshot tampering (CVE-2025-55305).
Method: Replace v8_context_snapshot.bin files with versions that override JavaScript builtins. When apps call Array.isArray(), malicious code executes.
Works because integrity checks ignore these "non-executable" files that actually contain executable JavaScript.
Impact: Nearly every Chromium-based app is vulnerable.
blog.trailofbits.com/2025/09/0…
A vulnerability in Electron applications allows attackers to bypass code integrity checks by tampering with V8 heap snapshot files, enabling local backdoors in applications like Signal, 1Password, and Slack.Darius Houle (The Trail of Bits Blog)
reshared this
Archiv.
Muzeum BMW v Mnichově.
Při první návštěvě jsem si myslel, že autor expozice měl neomezený rozpočet a neomezený přísun omamných látek.
#bw #photography #archiv #BMW

Microsoft has open-sourced its original 6502 BASIC code. It was created in 1976 to run on the same CPU that powered the Apple II, NES, and Atari 2600.Tom Warren (The Verge)
How is it even legal to have such barbaric employment policies like this. Surely air crew should be on the clock from the moment they start security clearance, until they exit the secure area at the end of their shift. Anything else is exploitation.
How does this compare with European airlines.

An accessible, light-weight, cross-platform ebook and document reader. - trypsynth/paperbackGitHub
Jason Fayre reshared this.
"For decades, the phrase “Year of the Linux Desktop” has been tossed around like a tech industry punchline. But now, it’s no longer a meme—it’s a movement.
This isn’t just about numbers—it’s about momentum. GNU/Linux’s desktop share hovered below 2% for years. But since 2020, it’s been climbing fast.
From the lens of @purism this shift is more than market share—it’s a cultural awakening."
puri.sm/posts/the-quiet-revolu…
#GNULinux #Linux #marketshare #yearofthelinuxdesktop #privacy #freedom #desktop

Purism makes premium phones, laptops, mini PCs and servers running free software on PureOS. Purism products respect people's privacy and freedom while protecting their security.Purism SPC
Trošku jsem se pustila do Nejvyššího soudu. medium.seznam.cz/clanek/pavla...
Nejvyšší soud a jeho opomíjená...

Nejvyšší soud má být garantem jednotného výkladu práva. V řadě oblastí však tuto funkci nezajišťuje, což vede k právní nejistotě. Z pohledu advokáta, který denně sleduje dopady soudních rozhodnutí na klienty, jde o problém, který nelze přehlížet.Pavla Krejčí (Médium.cz)

Purism makes premium phones, laptops, mini PCs and servers running free software on PureOS. Purism products respect people's privacy and freedom while protecting their security.Purism SPC
Proč už nevěřím Telegramu
Je to deset let, co jsem začal používat Telegram. Za tu dobu jsem přesvědčil hodně lidí, aby ho začali používat, obhajoval jsem ho, ale v poslední době mám čím dál větší pocit, že jsem se v něm mýlil. V tomto blogpostu se pokusím vysvětlit proč.
#Durov #IM #instantMessaging #Signal #Telegram
blog.eischmann.cz/2025/09/04/p…
(reakce na tento příspěvek se může zobrazit jako komentář pod článkem)
reshared this
Today we announced our progressive vision for Public Security in Montreal.
🔸Massive Investment in prevention;
🔸Creation of a civil service for social crises;
🔸An end to budgetary waste;
🔸Abolition of arbitrary police street checks.
we see you also don't want support from disabled people. People that are visually impaired can't read this since you posted an image full of text with no ALT that would spell the text out.
Good job.
What a shock. Carney ran on "no cuts" and lied. Again.
--
Finance Minister François-Philippe Champagne is forecasting “tough choices” in this fall’s federal budget, as the government reviews billions of dollars in proposed spending reductions that he suggested would lead to job losses in the civil service.
Sensitive content
Since I was a kid, I've always wondered how people could have let the Nazis do it... now I know : « #Google’s $45 million contract to spread #Netanyahu's #propaganda »
(all sources in the article)
› jackpoulson.substack.com/p/goo…
#BigTech #GAFAM #Colonialism #Fascism #Palestine #FreePalestine
Google is in the middle of a six-month, $45 million propaganda contract with Netanyahu’s office and was described as a “key entity” supporting Israel's messaging.Jack Poulson (All-Source Intelligence)
Kerplunk
in reply to CoMaps - Hike, Bike, Drive • • •Builds for IzzyOnDroid are directly from developers and signed by developers. This enables very fast publishing (whereas F-Droid re-builds apps from source).
So any developer can distribute self signed malicious apps fast.
Without checks. Wonderful Idea.
Fdroid builds from reviewed source code.
I will stick with FDroid and recommend others to do the same.
IzzyOnDroid ✅
in reply to Kerplunk • • •@Kerplunk we'd suggest you read the security section at apt.izzysoft.de/fdroid/index/i… 😉 TL;DR: multiple scans are performed on apps published via #IzzyOnDroid, to make it as safe & secure as can be. In the 10 years of our existence, there hasn't been a single incident of a malicious app. So please, don't spread uninformed misinformation ("without checks" even). Thanks! @CoMaps
PS: IzzyOnDroid also has #reproducibleBuilds to ensure apps were built from the indicated source. Planned for CoMaps as well
Information on IzzyOnDroid's F-Droid compatible repo
IzzyOnDroid App RepoNeatNit
in reply to IzzyOnDroid ✅ • • •@IzzyOnDroid @Kerplunk I've wondered for a while, better late than never: if I add the #IzzyOnDroid repo to the F-Droid app, how does the app choose which repo to pull updates from for each app? And in particular for CoMaps?
And are there other F-Droid client apps that handle this better that you'd recommend?
Thanks
IzzyOnDroid ✅
in reply to NeatNit • • •NeatNit
in reply to IzzyOnDroid ✅ • • •@IzzyOnDroid @Kerplunk Thanks! Perhaps worthy of an article to link to, similar to the security one you linked before. For me this is one of the things I overthink that makes me wary.
For example I have added the repository for Bitwarden, and I'm worried that they can (for example, in theory) add a malicious version of whatever app I'm searching for in the real F-Droid repo with a fake version number that's newer than the real one.
IzzyOnDroid ✅
in reply to NeatNit • • •Reproducible builds, signing keys, and binary repos | F-Droid - Free and Open Source Android App Repository
f-droid.orgNeatNit
in reply to IzzyOnDroid ✅ • • •IzzyOnDroid ✅
in reply to NeatNit • • •@neatnit Yupp. App signing is kind of TOFU (Trust On First Use). So check carefully before the first install, then the "signing stuff" protects you against malicious actors providing "updates". It's just one piece of protection, though – there's e.g. always the "supply chain" (e.g. a dependency the app uses could "sneak things in"), which is why we established several additional scans, @CoMaps @Kerplunk
(1/2)
IzzyOnDroid ✅
in reply to IzzyOnDroid ✅ • • •(2/2) For example, our "APK library scanner" finding "unexpected (proprietary) libs" is no rarity. For apps in our repo, in 90% this was unintended and got fixed by the corresponding dev quickly. In the other 10% we were either able to convince the dev to use a FOSS alternative (while updates were stalled here), or (in rare cases) had to remove the app entirely.
@neatnit @Kerplunk
IzzyOnDroid ✅
Unknown parent • • •@Kerplunk @ib I cannot really tell about "malicious" – but "suspicious", yes. Usually before (or rather instead) of inclusion. We then do not include such app unless clarified and found "OK". And yes, we avoid proprietary components like GMS. We make few exceptions where it's unavoidable, but then clearly mark the app with the NonFreeComp anti-feature
And yes, being cautious is essential, so thanks for taking care! We try to assist you there as good as we can, eg. with full transparency
Kerplunk
Unknown parent • • •@ib @IzzyOnDroid
Have your system ever detected anything malicious before?
I was hit by a malicious verified by playstore app, so yes, the experience was painful.
The most malicious thing on any android device is inclusion of GAPPS, the google tracking and spyware suite.
I have absolutely nothing against izzysoft way but now have a non google phone and after binning a phone that became malicious, extremely cautious with regard to applications and stores.