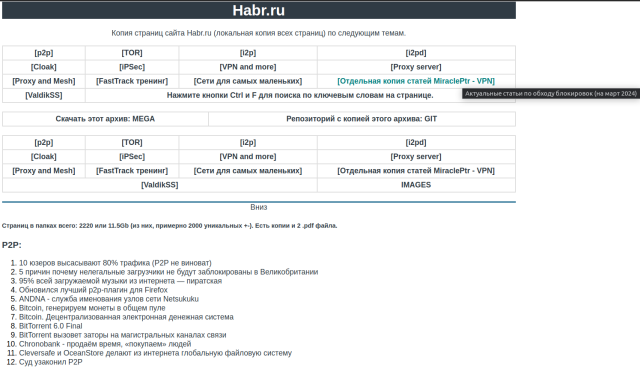
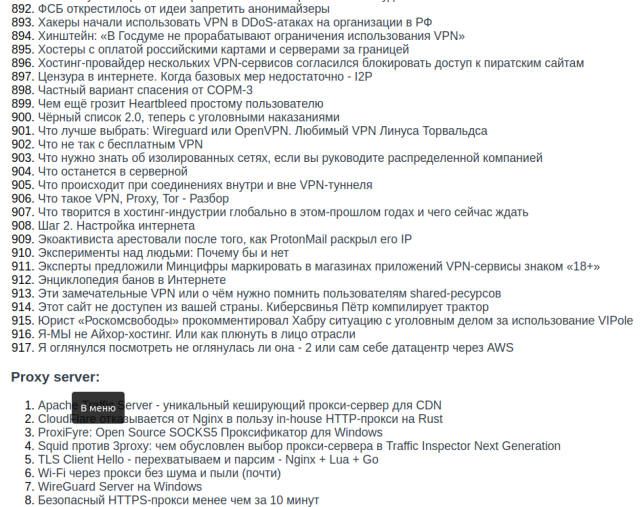
Все страницы сайта Habr.ru (локальная копия)
по следующим темам:
[VPN]
[Proxy][proxy-server]
[Mesh]
[i2p]
[i2pd]
[cloak]
[P2P]
[TOR]
[OpenVPN]
[XraY]
[V2rayNG]
[I2raY]
[V2rayXS]
[V2rayN]
[Yggdrasil]
[ValdikSS]Возможно, вам это будет интересно.
Я нашел эти ссылки в интернете.
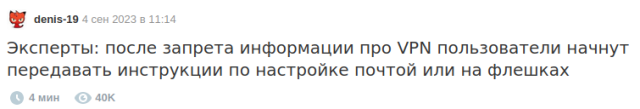
В связи с намерениями правительства удалить всю информацию по обходу блокировок из российского сегмента интернета, кто-то, решил принять меры. 🙂
ОН, судя по всему считает, что статьи это важная часть культуры и нашего прошлого.
Особенно, комментарии больших групп образованных людей на habrahabr.ru.
Этот человек, скорее всего считает важным сохранять и распространять полезную информацию.
А так же, делиться мнениями других людей, т.к. это развивает и помогает обществу рости в лучшую сторону.
Не смотря на мои предположения, для меня остается загадкой мотивация этой неизвестной личности.
Но я разделяю некоторые идеи, в плане того, что знаниями нужно делиться.
Мне всегда становится грустно, когда я обнаруживаю умерший сайт,
или удаленную страницу и потерянную информацию.
Поэтому, делюсь этими ссылками с вами.
А вы, можете поделиться с другими.
(будет что почитать, если интернет совсем кончится)
К тому же, 14 марта на хабре вышла статья
"Надежный обход блокировок в 2024 протоколы,
клиенты и настройка сервера от простого к сложному"
под которой один человек предложил сохранить статьи по обходу блокировок.
(эта статья сохранена в этом сборнике)
UPD1: "Статья уже была удалена. Но доступна если искать из другой страны."
UPD2: Сейчас, автор статей по "актуальному обходу блокировок MiraclePtr" - удален((
Учитывая времена, думаю стоит сохранить все локально, потому что не известно,
какие именно категории данных будут удаляться в будущем.
И нет надежды, что веб архив не будет заблокирован.
Да и не понятно, как сильно все изменится со временем.
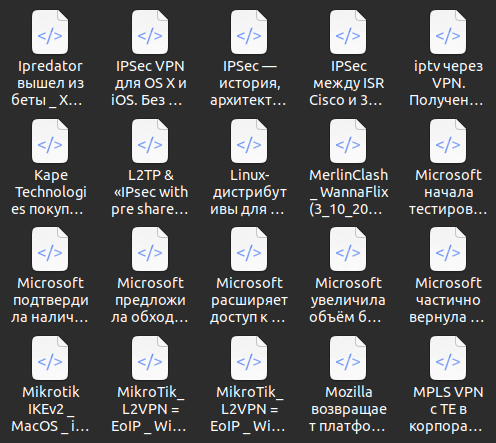
Страниц в папках всего: 2223 или 11.5Gb
1) Видео о содержимом 13Mb можно по этой ссылке:
mega.nz/file/cLMUHSAT#PHjc7WfT…
2) Скачать архивом .7z - 3.3Gb (сжат):
mega.nz/file/hf8xSbiI#3DrGc3P2…
3) Скачать отдельные папки 11.5Gb:
mega.nz/folder/9TVGgZjL#pGAidX…
4) Копия архива .7z - 3.3Gb:
fileconvoy.com/dfl.php?id=gee7…
5) Ссылка на репозиторий, если кому-то удобней скачивать так:
codeberg.org/hrabr/Habr.git
О содержимом.
Судя по ссылкам в страницах, они были сохранены с середины марта 2024.
Информация собрана по темам (список вверху) и все рассортировано по папкам.
Сохранены практически все страницы (за исключением откровенно рекламных статей).
Возможно вы встретите небольшое количество дублей, т.к. темы пересекаются.
(так же, встречаются одинаковые статьи опубликованные в разное время, но имеющие разные комментарии)
Возможна какая-то информация вам будет не интересна.
Есть страницы с устаревшей информацией (с 2008 года).
Они и комментарии из этих статей сохранены для истории.
В архиве есть index.html, через который можно искать статьи по ключевым словам через Ctrl+F.
Так же, под этим сообщением есть скриншеты и видео о структуре.
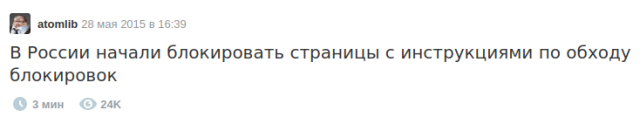
Если у вас в закладках, есть страницы с инструкциями для построения защищенных сетей,
или что-то, что вы считает полезными и это может быть потеряно,
добавляйте ссылки под этим постом, с описанием.
Может быть, ваша информация будет кому-то полезна.
Страницы были сохранены через невероятное дополнение: SingleFile
Если кто-то захочет оформить раздачу на rutracker,
то этот человек очень поможет нашему большому обществу,
когда страницы будут удалены с хабра (я считаю, это вопрос времени).
Как это уже произошло со страницами сайта 4pda.to.
Хочу сказать спасибо MiraclePtr за чудесные статьи и отдельное спасибо UranusExplorer за простые инструкции.
А так же, всему Хабр-сообществу, которое десятилетиями писало статьи и делилось своим мнением в комментариях.
#хабр #обходблокировок
#habr #pages #backup #cloak #i2p
#xray #nekobox #v2ray #v2rayn
#v2rayxs #v2rayng #i2ray #git
#amnezia #outline #shadowsocks
#vpn #proxy #server #mesh #p2p
#roskomnadzor #valdikss #network
#internet #dns #ssl #wireguard
#ikev2 #ipsec #l2tp #mikrotik
#linux #unix #mozilla #softether
#softethervpn #openvpn #peervpn
#pptp #security #ssh #openbsd
#ubuntu #debian #router #firewall
#private #http #https #openxray
#tor #info #articles #p2panda
#yggdrasil #habr #habrahabr #i2pd
#telegram #mega #rutracker #4pda
#блокировки
#ru #ua @rf @ru
@Revertron - тут куча твоих комментов и статьи есть, поэтому решил упомянуть тебя.
Пожалуйста, поделитесь этой информацией с друзьями. 💗
Если у вас есть идея куда еще можно залить эти статьи, предлагайте.
A copy of articles and comments from https://habr.ru, for the sake of history.
Please share this information with your friends.
Peace and love.
Codeberg.org