Mini Blue Team Diaries Story:
Was responsible for SecOps at a SaaS platform that managed lots of things for companies, including travel bookings.
We had a bunch of customers in the higher education space who used SSO to login to our app. Unfortunately, MFA within the SSO configuration was not common back then, so a compromised university account would lead to much access, including to our platform.
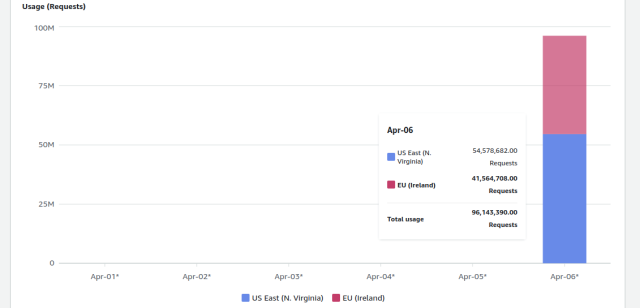
Suddenly, a thing we saw a lot of, was higher-ed customers reporting that they were being charged for trips that just didn't make sense. These were bookings for same day travel, usually between two African cities.
After some digging around and investigation, we figured out that a threat actor would phish or purchase the users university credentials, then, using the SSO into our environment, they'd make bookings using the travel booking feature - those bookings were made on behalf of the threat actors customers, who actually thought they were dealing with a legit, well-connected travel agent.
We were able to advise our customers on how to stop this type of thing happening, with approval rules for bookings, and ya know, MFA, and also managed to build in some detective controls so our team could detect and shut down such bookings as soon as they came in.
What made this particularly interesting though, through some OSINT, we were able to determine the true identity of the actor responsible - and we connected with them on Facebook, mainly because we wanted to ask them about their methods now that we'd all but shut down their scheme.
We chatted for a bit, and got some useful intel. At the end, the actor congratulated the team on our new controls, and said they'd moved on to using another service they'd found to make his bookings.
For more, slightly less mini, Blue Team Diaries stories like this, check out infosecdiaries.com
#infosec #DFIR #BlueTeam #infosecreads #cybersecurity