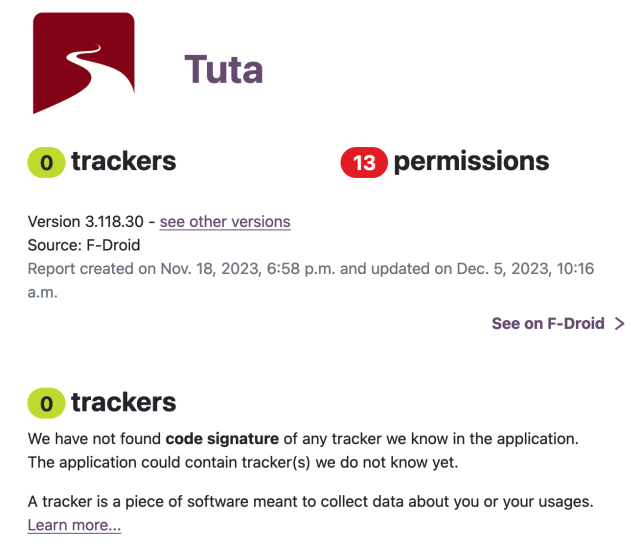
Performed by Trail of Bits. They found things to fix but nothing critical and no security flaws.
Search
Items tagged with: security
#monocles chat 1.7.9 is released on the playstore with a lot of updates and improvements! (See comments below)
play.google.com/store/apps/det…
#xmpp #chat #privacy #security #messenger

monocles chat - Apps on Google Play
monocles chat - The secure and ethical chat clientplay.google.com
RFC time! We're working on specifying how Accrescent's repository should look technically.
If you're an app developer who cares about app store features, an Accrescent user, or just interested in our development, leave your comments in the issue below 👇
github.com/accrescent/meta/iss…
#android #appstore #security #privacy #accrescent

RFC: Repository metadata reorganization · Issue #31 · accrescent/meta
Problem Accrescent's repository metadata format and organization was not designed for cacheability, internationalization, or atomicity. As a result, Accrescent has limited scalability, target audie...GitHub
isc.org/blogs/2024-bind-securi…
#dns #security

BIND 9 Security Release and Multi-Vendor Vulnerability Handling, CVE-2023-50387 and CVE-2023-50868
Yesterday we published BIND 9.16.48, 9.18.24, and 9.19.21. These releases mitigate several vulnerabilities that are described in our announcement.www.isc.org
- "The EU Court ruled that “Backdoors may also be exploited by criminal networks and would seriously compromise the security of all users’ electronic communications.”"
- “mass surveillance does not appear to have contributed to the prevention of terrorist attacks, contrary to earlier assertions made by senior intelligence officials.”
💖 Wow 
➡️ European Court of Human Rights's ruling: }]https://hudoc.echr.coe.int/eng/#{%22itemid%22:[%22001-230854%22]}
#Privacy #Encryption #Security
HUDOC - European Court of Human Rights
The HUDOC database provides access to the case-law of the Court (Grand Chamber, Chamber and Committee judgments and decisions, communicated cases, advisory opinions and legal summaries from the Case-Law Information Note), the European Commission of H…hudoc.echr.coe.int
Accrescent 0.17.1 released! This one fixes a bug where the download progress indicator was hidden and makes preparations for some upcoming server scaling improvements (follow for more info on that 😉).
Check out the release notes below!
github.com/accrescent/accresce…
#privacy #security #accrescent #appstore #android
Release 0.17.1 · accrescent/accrescent
This release fixes a UI bug where the download progress indicator was hidden and prepares for future server scaling improments by adding a backup pinned TLS certificate key. Bug fixes Fix download...GitHub
In addition to the measures that should be taken by various device manufacturers to secure and update their Internet-connected products, this incident suggests that we should follow the security recommendation according to which Internet of Things devices belong on a separate wireless network from your workstations or other systems containing valuable data.
tomshardware.com/networking/th…
#security #InternetOfThings

Three million malware-infected smart toothbrushes used in Swiss DDoS attacks — botnet causes millions of euros in damages
Dental IoT devices caused millions of Euros in damages for Swiss company, says report.Mark Tyson (Tom's Hardware)
I gave a talk at #fosdem #fosdem2024.
Video and slides are now available:
fosdem.org/2024/schedule/event…
#thunderbird #security #openpgp #librepgp #smime
I'm interested in your feedback on these thoughts. Either here, or, if your feedback is longer, for a discussion it might be best to post to
thunderbird.topicbox.com/group…
Thanks a lot to the organizers of @fosdem and the modern email developer room.
github.com/modern-email/FOSDEM…

GitHub - modern-email/FOSDEM-24
Contribute to modern-email/FOSDEM-24 development by creating an account on GitHub.GitHub
"Mastodon: Diebstahl beliebiger Identitäten im föderierten Kurznachrichtendienst" 😬
Die Versionen 3.5.17, 4.0.13, 4.1.13 und 4.2.5 beheben die Sicherheitslücke. 👇
heise.de/news/Mastodon-Diebsta…
#mastodon #security #vulnerability #schwachstelle #sicherheit

Mastodon: Diebstahl beliebiger Identitäten im föderierten Kurznachrichtendienst
In einem knappen Sicherheitshinweis lassen die Entwickler eine Bombe platzen: Angreifer können jeden beliebigen Account übernehmen und fälschen.Dr. Christopher Kunz (heise online)
Getting security online right seems like a daunting task. But one thing is certain: Password managers help! 💪
🔥Here are our top three: tuta.com/blog/best-password-ma… 🔥
What are your favorite #PasswordManagers❓
#privacy #security #opsec #passwords #passwordfatigue #databreach #breachdata #infosec

Why Password Managers Are Important
Password managers are easy tools to increase your privacy and security online. Start using them now!Tutanota
- KeePassXC (49%, 218 votes)
- Bitwarden (46%, 201 votes)
- Pass (4%, 18 votes)
S/MIME E-Mail Verschlüsselung mit Thunderbird einrichten? Wie das geht, erkläre ich in diesem Video:
youtube.com/watch?v=exPq87oSJL…
spacefun.ch/linux-videos#extra…
#Linux #Thunderbird #SMIME #Video #YouTube #Tutorial #Security #Privacy

S/MIME E-Mail Verschlüsselung einrichten
Mit S/MIME kannst du auf einfache Weise verschlüsselte und sichere Mails schreiben. Ich zeige dir, wie du ein kostenloses Zertifikat beziehen und in deinem M...YouTube
Today, we call on all Interior, Justice & Economy ministers of EU countries, to choose the right side: #privacy or #surveillance.
Together with other privacy-first companies we call on our ministers to defend encryption & protect privacy. 🔒
Read the full text here: tuta.com/blog/open-letter-encr…
#chatcontrol #encryption #security #cybersecurity
Open Letter Calling On EU Member States To Defend Encryption
As the trilogue is about to start, EU Member States must decide what side they are on: privacy or surveillance.Tutanota
Accrescent 0.17.0 is out! Accrescent now caches repository metadata, reducing bandwidth use a smidge, paving the way for a revamped download system, and bringing offline support just a *little* bit closer.
Check out the release notes below! github.com/accrescent/accresce…
#accrescent #security #privacy #android #appstore
Release 0.17.0 · accrescent/accrescent
This release implements repository metadata caching, making Accrescent more usable without Internet and saving bandwidth! Improvements Add caching for repository metadata Updates Bump Compose co...GitHub
Switch easily between work and personal Bitwarden accounts on Desktop, Mobile apps, and now the Bitwarden browser extension! Learn more in this blog: bitwarden.com/blog/account-swi…
#cybersecurity #security #passwordsecurity #passwordmanager #passwordmanagement

Switch between Bitwarden accounts quickly and easily | Bitwarden Blog
Quickly switch between multiple Bitwarden accounts in the browser extension, desktop and mobile apps.Bitwarden
Falsehoods programmers believe about… Biometrics
(For the new reader, there is a famous essay called Falsehoods Programmers Believe About Names. It has since spawned a long list of Falsehoods Programmers Believe About....)
Everyone has fingerprints!
The BBC has a grim tale of a family with a genetic mutation which means they have no fingerprints. It det
shkspr.mobi/blog/2021/01/false…
#/etc/ #design #falsehoods #policy #security
Today at apt.izzysoft.de/fdroid not just some #AndroidAppRain with 11 updated apps, but also some "evaporation": 12 apps have been removed as they used expired debug keys, more will follow them the next days. Some background on this can be found at gitlab.com/IzzyOnDroid/repo/-/…
For some more background: I'm currently implementing additional checks for better app security, see gitlab.com/IzzyOnDroid/repo/-/… – once done and working, details will follow with a blog article.

IzzyOnDroid F-Droid Repository
This is a repository of apps to be used with F-Droid. Applications in this repository are official binaries built by the original application developers, taken from their resp. repositories (mostly Github, GitLab, Codeberg).IzzyOnDroid App Repo
cURL-Maintainer: KI liefert "Scheiß-Berichte" als Bug-Reports
Mit sehr deutlichen Worten hat sich cURL-Maintainer Daniel Stenberg zu KI geäußert: Sie werde bei der Bug-Bounty missbraucht und liefere falsche Ergebnisse.
In 2024, please switch to Firefox roytanck.com/2023/12/23/in-202… #privacy #security #opensource #unix #linux #macos
feistyduck.com/newsletter/issu…
#security #ssh
docs-develop.pleroma.social/ba…
#pleroma #fediverse #security
cisa.gov/news-events/news/urge….
#security #programming
The Urgent Need for Memory Safety in Software Products | CISA
Cybersecurity Technical Advisor Bob Lord stresses the importance of memory safety in making software safer by design.Cybersecurity and Infrastructure Security Agency CISA
lawfaremedia.org/article/the-l…
#security #SecurityPolicy #law

The Lawfare Podcast: Three CISA Senior Advisers on Secure by Design
What is Security by Design?Default
Say hello to privacy! 👋
Tuta comes with zero trackers.
Thanks @exodus for providing this great test! 😍 👍
🔥 Grab YourName@tuta.com with our new domain! 🔥
Pick you favorite! ✊ Go Revolutionary now: tuta.com/create-email-address?…
#privacy #privateemail #encryption #emailaddress #security
Tuta Mail: Create a secure, private & encrypted email account for free
Tuta is the secure email service, built in Germany. Use encrypted emails on all devices with our open source email client, mobile apps & desktop clients.Tutanota
same reason for #Linux I guess and same reason why I do all the #OS1337 code in #bash with only .config makefiles where needed:
Readable and thus easy to #audit code allows for #transparency, which is vital for #maintainability and #security...
After all, mistakes do happen and I'd rather have it easy find and fix than optimize every bit at the cost of unmaintainable code.
Big Brother is watching you - now also via Google's & Apple's push. 🤬
That's why we don't use Google Push. When using Tuta, Google sees nothing! 💪
✅ Zero tracking
✅ Fully encrypted
✅ Maximum privacy
The data they don't get, they can't hand out to authorities! Go secure now: tuta.com/create-email-account?…
Here's more info on why we don't use Google Push and do not send any info via Apple notifications: tuta.com/blog/open-source-emai…
#security #privacy #google #apple #notifications #surveillance #tracking
Apple & Google Monitor All Your Push Notifications. But Tuta Protects You From This Since 2017.
We're here to stop surveillance by corporations like Google and Apple. That's why we replaced Google’s FCM with our own notification system and keep Apple Notification Data at a minimum. Read on to learn why this is important.Tutanota
LibreOffice supports symmetric and asymmetric encryption for OpenDocument Format (ODF) files.
Select File > Save/Save As
The "Save with password" option encrypts the file with AES-256.
The "Encrypt with GPG key" option encrypts the file with a public key.
Symmetric encryption: en.wikipedia.org/wiki/Symmetri…
Asymmetric encryption: en.wikipedia.org/wiki/Public-k…
Website: libreoffice.org
Mastodon: @libreoffice
#LibreOffice #Encryption #OpenSource #OpenPGP #PGP #GnuPG #GPG #InfoSec #Privacy #Security
Home | LibreOffice - Free Office Suite - Based on OpenOffice - Compatible with Microsoft
Free office suite – the evolution of OpenOffice. Compatible with Microsoft .doc, .docx, .xls, .xlsx, .ppt, .pptx. Updated regularly, community powered.www.libreoffice.org
Accrescent 0.16.0 is released! Apps can now include short descriptions, MTE is enabled by default for extra security, and update notifications aren't quite as pesky anymore. See the changelog below 👇
github.com/accrescent/accresce…
Developers can learn how to add short descriptions to their own apps in our freshly updated documentation. Check it out! accrescent.app/docs/guide/main…
#security #privacy #appstore #android #Accrescent

Release 0.16.0 · accrescent/accrescent
Improvements Add support for short descriptions Enable MTE Make "update finished" notification channel non-noisy Updates Bump AGP to 8.2.0 Bump bundletool Gradle plugin to 0.2.3 Bump Compose com...GitHub
My colleague discovered this really solid collection of cheat sheets on application security topics:
cheatsheetseries.owasp.org/
Introduction - OWASP Cheat Sheet Series
Website with the collection of all the cheat sheets of the project.cheatsheetseries.owasp.org
A new update is coming to the Tuta Calendar! 🥳
Stay tuned!
Enjoy your weekend. 💯🔒
#security #encryption #calendar #email #sneakpeek #weeklyview
Are you looking for a new email address?
🔥 Grab YourName@tuta.com while you still can. 🔥
Pick you favorite now! ✊ Go Revolutionary: tuta.com/create-email-account?…
#privacy #privateemail #encryption #emailaddress #security
Secure email: Tuta free encrypted email.
Tuta is the secure email service, built in Germany. Use encrypted emails on all devices with our open source email client, mobile apps & desktop clients.Tutanota
Sending end-to-end encrypted emails has never been easier! 😍
With a few simple clicks you can communicate securely and converse in total privacy.🔒
Protect yourself today with a new Tuta.com address!👇
tuta.com/
#privacy #encryption #opensource #security #sunday
Secure email: Tutanota free encrypted email.
Tutanota is the secure email service, built in Germany. Use encrypted emails on all devices with our open source email client, mobile apps & desktop clients.Tutanota
monocles chat 1.7.7.2 is released today on f-droid with a big update! 🎉
Enjoy your new and secure chat experience!
f-droid.org/en/packages/de.mon…
And see the changelog since the previous version in the comments
#fdroid #monocles #chat #xmpp #security
monocles chat | F-Droid - Free and Open Source Android App Repository
is an Open Source XMPP chat client for Androidf-droid.org
Say NO to broken browsers! ⛔
The EU is preparing a very dangerous law that would undermine the security of every browser.
Speak up now! 🗣️
@Jeremiah has more on how you can help to protect the web! 💪
jeremiahlee.com/posts/2023-eu-…
#EU
#privacy
#security
#webdev
#eIDAS
No Broken Browsers
Open letter to the European Commision on its eIDAS proposalJeremiah Lee (www.jeremiahlee.com)
Lauschangriff auf russischen Jabber-Server in Deutschland: Wer steckt dahinter?
Rein zufällig flog auf, dass sich Unbekannte mit einem eigenen Zertifikat in Jabber-Chat-Verbindungen einklinkten. Die Betreiber vermuten eine Polizeiaktion.
heise.de/news/Lauschangriff-au…
#Jabber #Let'sEncrypt #ManintheMiddle #Security #XMPP






 “
“