Search
Items tagged with: security

In-Process 6th April 2023
The big news this time around is the release of NVDA 2023.1! But there’s plenty more exclusive news below so let’s get into it: NVDA 2023.1 It’s new release time! NVDA 2023.1 is n…NV Access
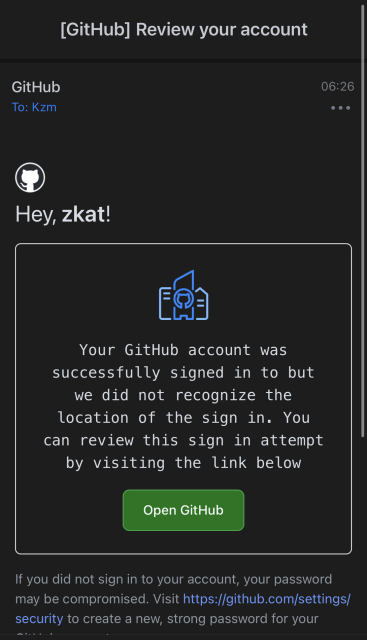
Whole Foods, owned by Amazon, now has biometric handprint scanning to pay for your groceries.
When I expressed my concern, the feller behind the counter said, “It’s just like the biometric scanner on your phone…”
“Um, no, it’s not,” I replied. “Because THAT biometric data is on MY device, not yours.”
He shrugged in response.
I don’t advise you to go this route, friends. Not until there are more legal standards and protections in place to protect consumers.
If you search the web for why software updates are important, you will get loads of results that say there are "3 or 5 reasons why software updates are important". While this may be correct, there is only one major reason why you must keep your software up to date: Security.
Stay secure, update your systems! 😎💪🔒
https://tutanota.com/blog/posts/why-updates-are-important
#LastPass #Security
https://www.bleepingcomputer.com/news/security/critical-microsoft-outlook-bug-poc-shows-how-easy-it-is-to-exploit/

Critical Microsoft Outlook bug PoC shows how easy it is to exploit
Security researchers have shared technical details for exploiting a critical Microsoft Outlook vulnerability for Windows (CVE-2023-23397) that allows hackers to remotely steal hashed passwords by simply receiving an email.Ionut Ilascu (BleepingComputer)
In this video, we downloaded the authenticator app from the App Store and we opened it as we monitored the iPhone network traffic. While the app was showing the permission prompt, we captured at least 3 calls made by the app sending diagnostics to Microsoft. The app sent 14 KB of analytics even before accepting the prompt.
The message on the prompt actually says that Microsoft needs to collect diagnostic data in order to keep Authenticator secure and up to date. 😵💫
#Privacy #Cybersecurity #2FA #InfoSec #Security #Microsoft
https://youtu.be/r5456XXG6v0

Privacy: Microsoft Authenticator sends analytics even before accepting the privacy statement
When opening Microsoft Authenticator for the first time after downloading it from the App Store, it prompts the user to accept sharing diagnostics with Micro...YouTube
https://www.kuketz-blog.de/adaway-werbe-und-trackingfrei-im-android-universum/
Hinweis: Habe Blokada aus der Empfehlungsecke entfernt.
#tracking #datenschutz #dsgvo #ttdsg #sicherheit #security #privacy

AdAway: Werbe- und trackingfrei im Android-Universum
AdAway kann der Auslieferung von (schädlicher) Werbung und dem Abfluss von persönlichen Daten an zweifelhafte Anbieter einen Riegel vorschieben.Kuketz IT-Security Blog
#privacy #security
https://safing.io/
#security #privacy #firewall #sicherheit #datenschutz #windows
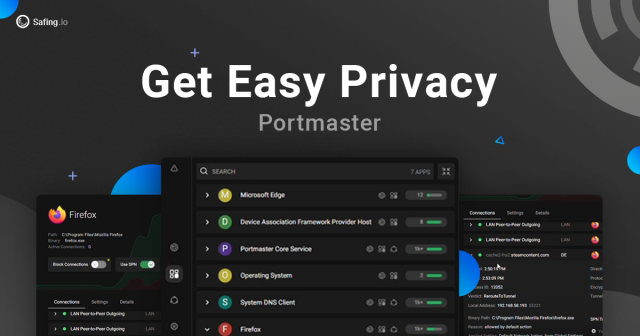
Safing Portmaster - Easy Privacy
Portmaster is a free and open-source application that puts you back in charge over all your computer's network connections. Increase your privacy and security. Get peace of mind.safing.io
📱 Android-DataBackup
https://github.com/XayahSuSuSu/Android-DataBackup/blob/main/README_EN.md

Android-DataBackup/README_EN.md at main · XayahSuSuSu/Android-DataBackup
数据备份 DataBackup for Android. Contribute to XayahSuSuSu/Android-DataBackup development by creating an account on GitHub.GitHub
Here are some privacy-first apps frequently recommended by the Tutanota community.
What are your favorite apps to quit #BigTech?
#DataProtection #Encryption #Security #Privacy
But we say: Stop the #CryptoWars. Destroying everybody's #privacy will not increase #security.
Read here why: 👇
https://tutanota.com/blog/posts/going-dark
#GoingDark

Going dark: Is encryption a threat to our security? The Swedish EU Council says yes.
Politicians often warn that criminals are 'going dark'. This warning is used like the argument to 'protect the children': to undermine encryption.Tutanota
Read our article below for more details and to see how easy it is for developers to get set up:
https://f-droid.org/en/2023/01/15/towards-a-reproducible-fdroid.html

Towards a reproducible F-Droid | F-Droid - Free and Open Source Android App Repository
A common criticism directed at F-Droid is that F-Droid signs published APKswith its own keys. Using our own keys doesn’t mean insecure — we have a goodtrack ...f-droid.org
🇩🇪 Noch wer mit Android < 4.4 unterwegs und somit auf TLS 1.0/1.1 angewiesen (1. ja, 2. macht nix, 3. nein)?
So:

SSL Labs Grade Change for TLS 1.0 and TLS 1.1 Protocols | Qualys Security Blog
Update 1/31/2020: The grade change is now live on www.ssllabs.com. Servers that support TLS 1.0 or TLS 1.1 are capped to B grade. Update 1/16/2020: The grade change is now live on the development…Qualys Security Blog
- I still use such a device and need compatibility (1%, 4 votes)
- I still use such a device but wouldn't mind (6%, 21 votes)
- I don't care (92%, 320 votes)
Let's Encrypt is hiring for someone to join our SRE team and help run the largest Certificate Authority in the world! Come work with me and some of the most wonderful folks in tech, to make the web a better place.
https://www.abetterinternet.org/careers/le-sre-sw3/
#jobs #sre #webPKI #security #privacy #cryptography

Let's Encrypt Software Engineer (SRE)
Posted: September 29, 2022 Start Date: January 2023 Position Status: Open Location: Remote within US Compensation: $140k USD, 100% 401k Match, Excellent Insurance We’re making HTTPS easier for developers to use, we’re doing it at scale, and we need y…Internet Security Research Group
✊🏽 We must hold them accountable for the risks and damages their actions cause: it's unacceptable to allow society to continue this way.
 Thanks to #CCC for helping expose the dangerous truth.
Thanks to #CCC for helping expose the dangerous truth.#SurevillanceCapitalism #infosec
https://web.archive.org/web/20221227125216/https://www.nytimes.com/2022/12/27/technology/for-sale-on-ebay-a-military-database-of-fingerprints-and-iris-scans.html

For Sale on eBay: A Military Database of Fingerprints and Iris Scans
German security researchers studying biometric capture devices popular with the U.S. military got more than they expected for $68 on eBay.Kashmir Hill (The New York Times)
So, here are my responses to all of these concerns!
Let me start by saying I used to support LastPass. I recommended it for years and defended it publicly in the media. If you search Google for "jeremi gosney" + "lastpass" you'll find hundreds of articles where I've defended and/or pimped LastPass (including in Consumer Reports magazine). I defended it even in the face of vulnerabilities and breaches, because it had superior UX and still seemed like the best option for the masses despite its glaring flaws. And it still has a somewhat special place in my heart, being the password manager that actually turned me on to password managers. It set the bar for what I required from a password manager, and for a while it was unrivaled.
But things change, and in recent years I found myself unable to defend LastPass. I can't recall if there was a particular straw that broke the camel's back, but I do know that I stopped recommending it in 2017 and fully migrated away from it in 2019. Below is an unordered list of the reasons why I lost all faith in LastPass:
- LastPass's claim of "zero knowledge" is a bald-faced lie. They have about as much knowledge as a password manager can possibly get away with. Every time you login to a site, an event is generated and sent to LastPass for the sole purpose of tracking what sites you are logging into. You can disable telemetry, except disabling it doesn't do anything - it still phones home to LastPass every time you authenticate somewhere. Moreover, nearly everything in your LastPass vault is unencrypted. I think most people envision their vault as a sort of encrypted database where the entire file is protected, but no -- with LastPass, your vault is a plaintext file and only a few select fields are encrypted. The only thing that would be worse is if...
- LastPass uses shit #encryption (or "encraption", as @sc00bz calls it). Padding oracle vulnerabilities, use of ECB mode (leaks information about password length and which passwords in the vault are similar/the same. recently switched to unauthenticated CBC, which isn't much better, plus old entries will still be encrypted with ECB mode), vault key uses AES256 but key is derived from only 128 bits of entropy, encryption key leaked through webui, silent KDF downgrade, KDF hash leaked in log files, they even roll their own version of AES - they essentially commit every "crypto 101" sin. All of these are trivial to identify (and fix!) by anyone with even basic familiarity with cryptography, and it's frankly appalling that an alleged security company whose product hinges on cryptography would have such glaring errors. The only thing that would be worse is if...
- LastPass has terrible secrets management. Your vault encryption key always resident in memory and never wiped, and not only that, but the entire vault is decrypted once and stored entirely in memory. If that wasn't enough, the vault recovery key and dOTP are stored on each device in plain text and can be read without root/admin access, rendering the master password rather useless. The only thing that would be worse is if...
- LastPass's browser extensions are garbage. Just pure, unadulterated garbage. Tavis Ormandy went on a hunting spree a few years back and found just about every possible bug -- including credential theft and RCE -- present in LastPass's browser extensions. They also render your browser's sandbox mostly ineffective. Again, for an alleged security company, the sheer amount of high and critical severity bugs was beyond unconscionable. All easy to identify, all easy to fix. Their presence can only be explained by apathy and negligence. The only thing that would be worse is if...
- LastPass's API is also garbage. Server-can-attack-client vulns (server can request encryption key from the client, server can instruct client to inject any javascript it wants on every web page, including code to steal plaintext credentials), JWT issues, HTTP verb confusion, account recovery links can be easily forged, the list goes on. Most of these are possibly low-risk, except in the event that LastPass loses control of its servers. The only thing that would be worse is if...
- LastPass has suffered 7 major #security breaches (malicious actors active on the internal network) in the last 10 years. I don't know what the threshold of "number of major breaches users should tolerate before they lose all faith in the service" is, but surely it's less than 7. So all those "this is only an issue if LastPass loses control of its servers" vulns are actually pretty damn plausible. The only thing that would be worse is if...
- LastPass has a history of ignoring security researchers and vuln reports, and does not participate in the infosec community nor the password cracking community. Vuln reports go unacknowledged and unresolved for months, if not years, if not ever. For a while, they even had an incorrect contact listed for their security team. Bugcrowd fields vulns for them now, and most if not all vuln reports are handled directly by Bugcrowd and not by LastPass. If you try to report a vulnerability to LastPass support, they will pretend they do not understand and will not escalate your ticket to the security team. Now, Tavis Ormandy has praised LastPass for their rapid response to vuln reports, but I have a feeling this is simply because it's Tavis / Project Zero reporting them as this is not the experience that most researchers have had.
You see, I'm not simply recommending that users bail on LastPass because of this latest breach. I'm recommending you run as far way as possible from LastPass due to its long history of incompetence, apathy, and negligence. It's abundantly clear that they do not care about their own security, and much less about your security.
So, why do I recommend Bitwarden and 1Password? It's quite simple:
- I personally know the people who architect 1Password and I can attest that not only are they extremely competent and very talented, but they also actively engage with the password cracking community and have a deep, *deep* desire to do everything in the most correct manner possible. Do they still get some things wrong? Sure. But they strive for continuous improvement and sincerely care about security. Also, their secret key feature ensures that if anyone does obtain a copy of your vault, they simply cannot access it with the master password alone, making it uncrackable.
- Bitwarden is 100% open source. I have not done a thorough code review, but I have taken a fairly long glance at the code and I am mostly pleased with what I've seen. I'm less thrilled about it being written in a garbage collected language and there are some tradeoffs that are made there, but overall Bitwarden is a solid product. I also prefer Bitwarden's UX. I've also considered crowdfunding a formal audit of Bitwarden, much in the way the Open Crypto Audit Project raised the funds to properly audit TrueCrypt. The community would greatly benefit from this.
Is the cloud the problem? No. The vast majority of issues LastPass has had have nothing to do with the fact that it is a cloud-based solution. Further, consider the fact that the threat model for a cloud-based password management solution should *start* with the vault being compromised. In fact, if password management is done correctly, I should be able to host my vault anywhere, even openly downloadable (open S3 bucket, unauthenticated HTTPS, etc.) without concern. I wouldn't do that, of course, but the point is the vault should be just that -- a vault, not a lockbox.
I hope this clarifies things! As always, if you found this useful, please boost for reach and give me a follow for more password insights!
#infosec #wikipedia #security #hiring
https://boards.greenhouse.io/wikimedia/jobs/4611087
@dsearls and @katherined talk to @kyle about hardware supply chains, building the only USA-made mobile phone, trust, open standards, and much more. Full episode here: https://www.reality2cast.com/133
https://youtube.com/shorts/bCR-S0nWRZE
#opensource #security #trust #openstandards #vendorLockin #podcast #NewEpisode

Hardware Supply Chains, Trust Agility, and Avoiding Vendor Lock-in
Doc Searls and Katherine Druckman talk to Kyle Rankin about hardware supply chains, building the only USA-made mobile phone, trust, open standards, and much more.Reality 2.0
[1]Nein? Doch! Ohh! 😉
Schmeißt dieses unnütze Schlangenöl endlich von euren Rechnern. Einzig den Microsoft Defender würde ich noch (mit leichten Schmerzen) eingeschaltet lassen. Mehr Infos unter [2].
#antivirus #security #snakeoil
[1] https://www.heise.de/news/Virenschutz-Rechteausweitung-durch-Schwachstelle-in-AVG-und-Avast-7367529.html
[2] https://www.kuketz-blog.de/antiviren-scanner-mehr-risiko-als-schutz-snakeoil-teil1/

Virenschutz: Rechteausweitung durch Schwachstelle in AVG und Avast
Die Virenscanner von AVG und Avast hätten Angreifern ermöglichen können, ihre Rechte im System auszuweiten. Updates zum Beheben des Fehlers sind verfügbar.Dirk Knop (heise online)
https://youtube.com/@geek-room - nový playlist Geek Room CZ
https://youtu.be/3tF8Be0E3xc - Archinstall Skript pro LUKS a BTRFS Arch Linux Instalaci.
https://youtu.be/YdqGsv3tmN4 - Arch Linux Manuální Instalace s LUKS (encrypt) a BTRFS souborovým systémem. (probíhá ještě zpracování vyšších HD rozlišení.)
https://github.com/raven2cz/geek-room
https://github.com/raven2cz/geek-room/blob/main/arch-install-archinstall-luks-btrfs/arch-install-archinstall-luks-btrfs.md
https://github.com/raven2cz/geek-room/blob/main/arch-install-luks-btrfs/arch-install-luks-btrfs.md #archlinux #linux #geek #security #arch #youtube #dotfiles #guide #czech
GitHub - raven2cz/geek-room: Repository dedicated to an enthusiast for technology, games, new software features and GNU/Linux.
Repository dedicated to an enthusiast for technology, games, new software features and GNU/Linux. - GitHub - raven2cz/geek-room: Repository dedicated to an enthusiast for technology, games, new sof...GitHub
#News #TSA #privacy #biometrics #security #HumanRights #SurveillanceCapitalism #HomelandSecurity #DHS #Airport
https://www.washingtonpost.com/technology/2022/12/02/tsa-security-face-recognition/
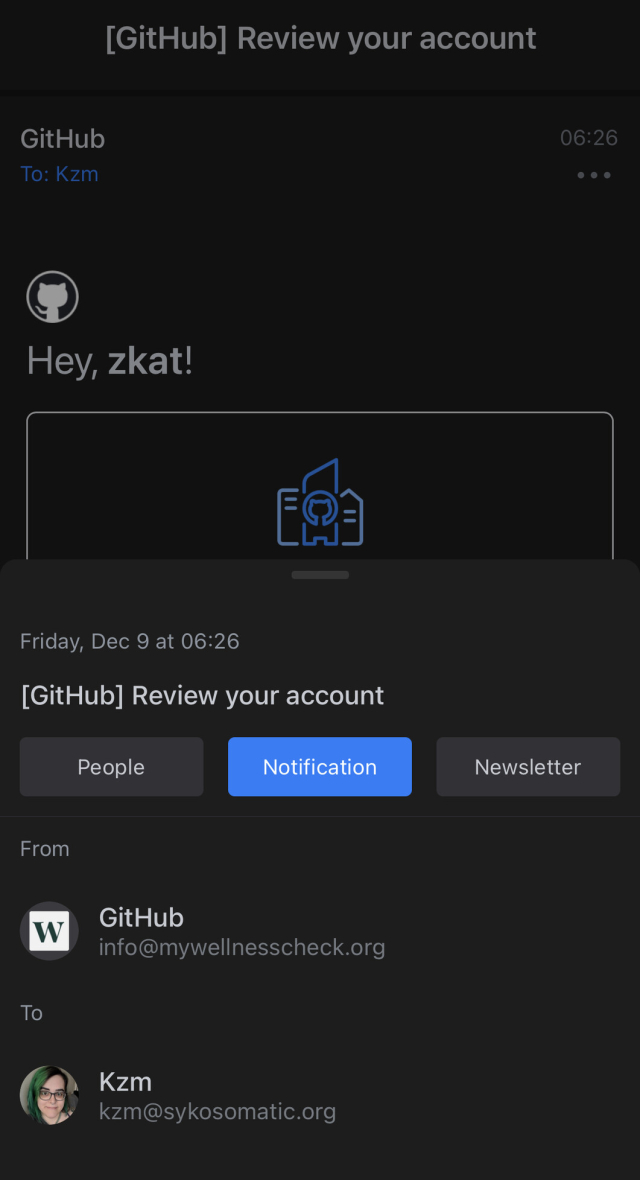
According to research conducted by @zerforschung, the #Twitter alternative Hive Social has got a number of dangerous #security vulnerabilies.
They allow attackers to completely access and even to partly edit anyone's data, including private posts, deleted direct messages, e-mail addresses and phone numbers signed up with etc.
Once again this demonstrates that you should not rely on closed-source software to guard sensitive data.
🔗 https://zerforschung.org/posts/hive-en

⚠️ Warning: do not use Hive Social 👉🐝👈
Dieser Artikel ist auch auf deutsch erschienen. Following the Twitter takeover, a number of services promising to be an alternative gained traction. One of those is “Hive Social”, which reached more than a million users in the last weeks.zerforschung.org

Let’s Encrypt issued over 3 billion certificates, securing 309M sites for free
Internet Security Research Group (ISRG), the nonprofit behind Let's Encrypt, says the open certificate authority (CA) has issued its three billionth certificate this year.Sergiu Gatlan (BleepingComputer)
Standard orders ship within 10 business days. 🚀
#librem5usa #librem #phone #purism #security #freedom #madeinUSA
https://puri.sm/posts/special-year-end-promotion-for-librem-5-usa?mtm_campaign=organic&mtm_source=promo&mtm_medium=librem-social&mtm_content=ls-year-end-promotion-l5usa
Special Year End Promotion for Librem 5 USA – Purism
Purism makes premium phones, laptops, mini PCs and servers running free software on PureOS. Purism products respect people's privacy and freedom while protecting their security.Purism SPC
If you use WhatsApp, your details could well be up for sale
#news #tech #technology @WhatsApp #security #privacy #databreach
https://www.techradar.com/news/whatsapp-data-breach-sees-nearly-500-million-user-records-up-for-sale
TalkBack depends on a text-to-speech (TTS) implementation installed/configured/activated. It needs to have Direct Boot support to function before the first unlock of a profile. Google's TTS implementation supports this and can be used on GrapheneOS, but it's not open source.
We requested Direct Boot support from both prominent open source implementations:
RHVoice: https://github.com/RHVoice/RHVoice/issues/271
eSpeak NG: https://github.com/espeak-ng/espeak-ng/issues/917
eSpeak NG recently added it but it's not yet included in a stable release and their licensing (GPLv3) is too restrictive for us.
RHVoice itself has acceptable licensing for inclusion in GrapheneOS (LGPL v2.1), but has dependencies with restrictive licensing. Both these software projects also have non-free licensing issues for the voices. Neither provides close to a working out-of-the-box experience either.
Google's Speech Services app providing text-to-speech and speech-to-text works perfectly. Their proprietary accessibility services app with extended TalkBack and other services also works fine. However, many of our users don't want to use them and we need something we can bundle.
There aren't currently any usable open source speech-to-text apps. There are experimental open source speech-to-text implementations but they lack Android integration.
We also really need to make a brand new setup wizard with both accessibility and enterprise deployment support.
GrapheneOS still has too little funding and too few developers to take on these projects. These would be standalone projects able to be developed largely independently. There are similar standalone projects which we need to have developed in order to replace some existing apps.
AOSP provides a set of barebones sample apps with outdated user interfaces / features. These are intended to be replaced by OEMs, but we lack the resources of a typical OEM. We replaced AOSP Camera with our own app, but we still need to do the same with Gallery and other apps.
Google has started the process of updating the open source TalkBack, which only happens rarely. We've identified a major issue: a major component has no source code published.
https://github.com/google/talkback/pull/28
Google has been very hostile towards feedback / contributions for TalkBack...
This is one example of something seemingly on the right track significantly regressing. Another example is the takeover of the Seedvault project initially developed for GrapheneOS. It has deviated substantially from the original plans and lacks usability, robustness and security.
In the case of Seedvault, GrapheneOS designed the concept for it and one of our community members created it. It was taken over by a group highly hostile towards us and run into the ground. It doesn't have the intended design/features and lacks usability, security and robustness.
All of these are important standalone app projects for making GrapheneOS highly usable and accessible. What we need is not being developed by others and therefore we need to the resources including funding and developers to make our own implementations meeting our requirements.
#grapheneos #privacy #security #android #mobile #accessibility #texttospeech #speechtotext #talkback #blind #backup
add Direct Boot support for Android so RHVoice can be used with TalkBack before the initial unlock · Issue #271 · RHVoice/RHVoice
More information: https://developer.android.com/training/articles/direct-boot https://github.com/GrapheneOS/platform_packages_apps_Updater is a trivial example of using this. You need to mark a sub...GitHub
https://www.bleepingcomputer.com/news/security/nordvpn-black-friday-deal-up-to-63-percent-off-a-27-month-vpn-subscription/
#Security
NordVPN Black Friday deal: Up to 63% off a 27-month VPN subscription
NordVPN's Black Friday deal is live with up to 63% off and 3 extra months for free on 1-year or 2-year subscriptions to the NordVPN VPN service.Lawrence Abrams (BleepingComputer)
https://youtu.be/YdbA7Z8Ae4w
#security #supplyChain #infosec #manufacturing #electronics #hardware #phones #teamKyle

Why The U.S. Fell Behind In Phone Manufacturing
Made in China. It’s a common phrase known by many. Cell phones, TV screens and game consoles are just some of the millions of electronics manufactured and im...YouTube
Our Made-in-USA-electronics Librem 5 USA phone also got a number of shout-outs. Pretty neat!
https://youtu.be/YdbA7Z8Ae4w #security #supplychain #infosec #manufacturing

Why The U.S. Fell Behind In Phone Manufacturing
Made in China. It’s a common phrase known by many. Cell phones, TV screens and game consoles are just some of the millions of electronics manufactured and im...YouTube
#Privacy #Security #Crytology #Cryptography #InfoSec

Episode 7: Scaling Up Secure Messaging to Large Groups With MLS!
Raphael Robert from Wire talks about how MLS wants to scale secure messaging to groups with hundreds or even thousands of participants.Cryptography FM
https://youtu.be/MrvWrBaYTyI

PASS ZX2C4 - Keep Your Secrets
PASS ZX2C4 - The Standard Unix Password Manager* Password Storage* Simple and follow Unix philosophy * Each password lives inside of a GPG encrypted file * T...YouTube
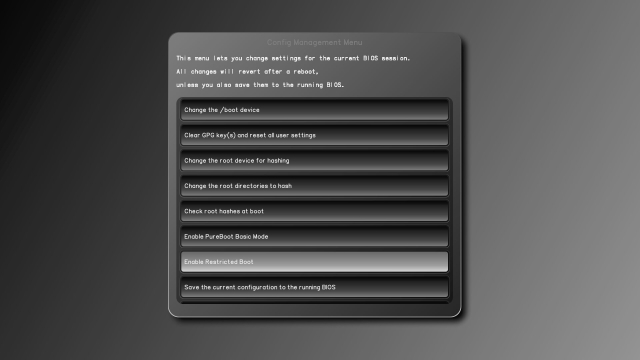
Introducing PureBoot Restricted Boot – Purism
Purism makes premium phones, laptops, mini PCs and servers running free software on PureOS. Purism products respect people's privacy and freedom while protecting their security.Purism SPC
I've written a number of books (https://kylerank.in/writing.html) and was a long-time columnist for Linux Journal magazine.
I have many hobbies including #weaving, refurbishing mechanical #calculators, #3dprinting, #brewing, and many other things.
We’re no longer living in the mainframe era. The security properties of the Internet are different to mainframes. This is actually an anti-feature that either complicates life or actually compromises security (when folks run servers as root and forget to drop privileges , etc.).
If anyone has any sway within the kernel team, etc., please do your thing.
https://source.small-tech.org/site.js/app/-/issues/169
#linux #security #theatre #networking

Disable privileged ports security theatre on Linux instead of using setcap (#169) · Issues · Site.js / app
Summary Currently, we’re using setcap to grant the CAP_NET_BIND_SERVICE privilege to allow Node.js (during development and testing) and the Site.js binary...GitLab